@michelandre
Salut Michel-André
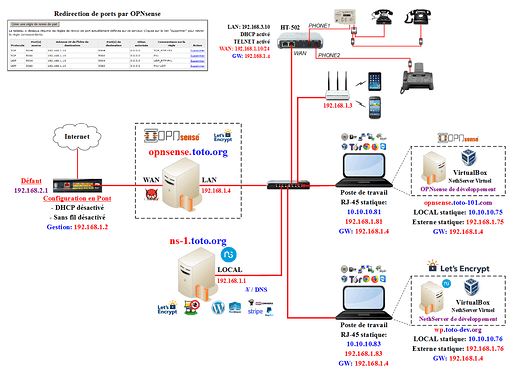
In my diagrams, most are from clients, in their offices. My NethServers at clients all only run with one NIC (GREEN). There’s still a basic firewall running on NethServer, even if you do not install firewall or two NICs. And my clients also have workstations, printers and other stuff. The doctors have an X-Ray, not something any freak has at home!
These all need network and Internet, that’s the main reason a switch is there. The Switch in some cases, is as virtual as nethServer and OPNsense, everything in Proxmox.
I’ve done that kind of setup, even helping people here at the forum setting this up!
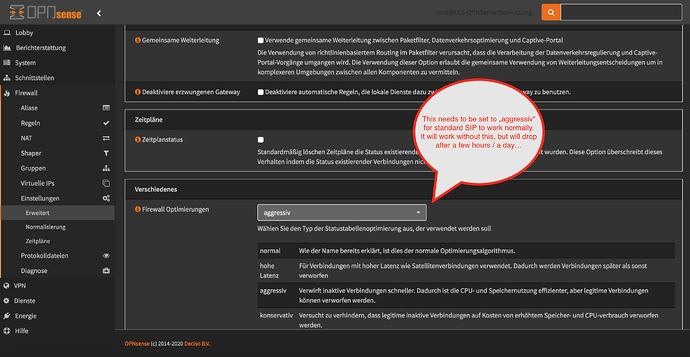
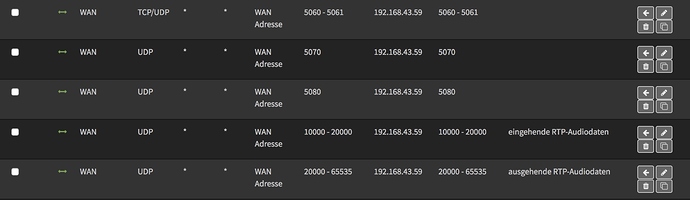
If both NethServer and OPNsense act as Firewall, you’ld end up with double NAT, not the best background for VoIP. I have been forced to use double NAT before, it does work, but can cause unexpected issues.
My suggestion would be as in this description:
https://wiki.nethserver.org/doku.php?id=userguide:nethserver_and_proxmox
I’d use IP 1 for the OPNsense, my firewalls always use 1 as IP. My NethServers almost always use 20 as their IP (GREEN). NethServers AD is uses IP 11.
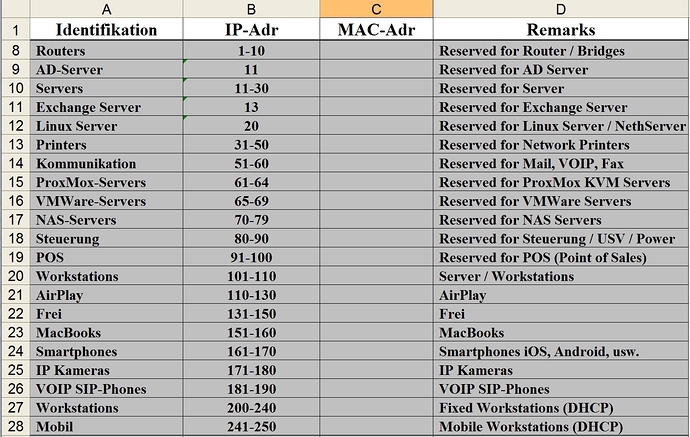
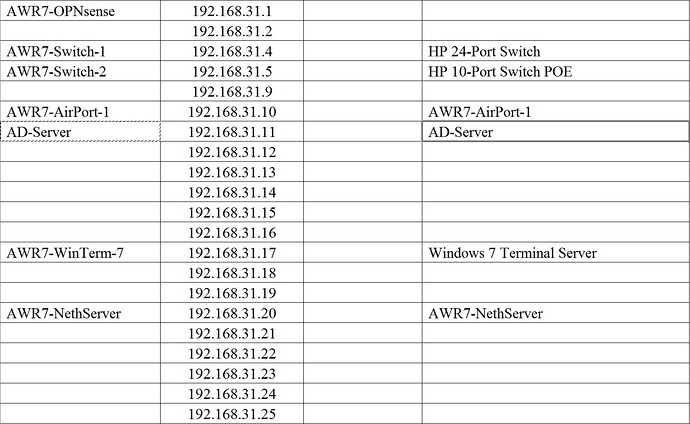
I use a XL table like this for all networks, the dark grey (below) are “standards” for devices.
The rest looks like this (no MAC addresses shown…)
If you want, I can provide a sample in XL on my nextcloud at home…
If you’re in doubt as to why two networks and two firewalls to configure - you most likely don’t need a second firewall, which can make life difficult.
If you’re happy with OPNsense features and stability (like I am), then remove the second NIC from your NethServer (or deconfigure it) and only use a single GREEN Network.
I’ve set up 30+ NethServers for clients, and only twice setup a NethServer for a friend, and only because the firewall he had fried between Xmas and New Year, when getting spares is difficult. And no internet during those xmas just isn’t an option!
All the rest were all configured with only one NIC. Together, OPNsense and NethServer make it happen! And even if you have a problem with something you set up on NethServer and it doesn’t work as expected - you still have internet to check the NethServer Forum or Google for help!
There are legit reasons for going the extra mile and using more than one firewall:
20 years ago, I had to secure a bank’s internet connection.
At the time, I used three different firewalls, cascaded.
All three using different OS and Systems.
Checkpoint, Cisco and a MonoWall, behind each other.
All three had out of band and internal monitoring.
A break in would have entailed hacking the checkpoint, using whatever was working after the hack to attack the cisco. And after the cisco, you’ld still have had to attack the M0n0wall.
Even if you cut their telefone / cable connection, a SMS would have been sent from the monitoring system.
And all in all, you would have had exactly 2x 5 minutes to do the break in, else the alarm would have been triggered!
But at home or in the office, you don’t really need this kind of over-security - and they had the budget for that!
My 2 cents
Andy