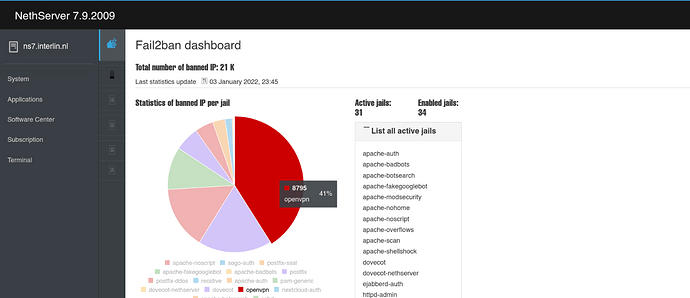
I noticed a enormous amount of fail2ban mails about attempts to log in / abuse the openvpn service.
Anyone else noticed a dramatic increase in openvpn traffic/hack attempts?
Worth asking: default port for your daemon?
no, regular level ± 500/day
Does fail2ban blocks the attacker?
Check the fail2ban log
Yes, the last days there were a lot of attempts.
Fail2ban banned them.
No hints of successfull login in logs!
Thanks to @stephdl for this great peace of software in nethserver! 

I have default modules for openvpn and fail2ban installed so, probably either 1194 or 943… I must say I didn’t look into that too much…
I agree that running on a non standard port will reduce attempts dramatically. I have seen that with SSH: since I run that on a non standard port I have almost no SSH login attempts anymore…
However, it does feel quite safe to have fail2ban running.
Let’s say that It could avoid most… malicious OpenVPN knockers for access…
Seeing the same thing over the last couple of days. A HUGE increase in the number of connection attempts.
Instead of less than 10 attempts a day, it’s now around 2,500 per day.
Similar pattern to here from a couple of years back.
Cheer.
Does failed attempts of breaking the Openvpn certificated access really a need for attention. Trying to learn here.
Thanks.