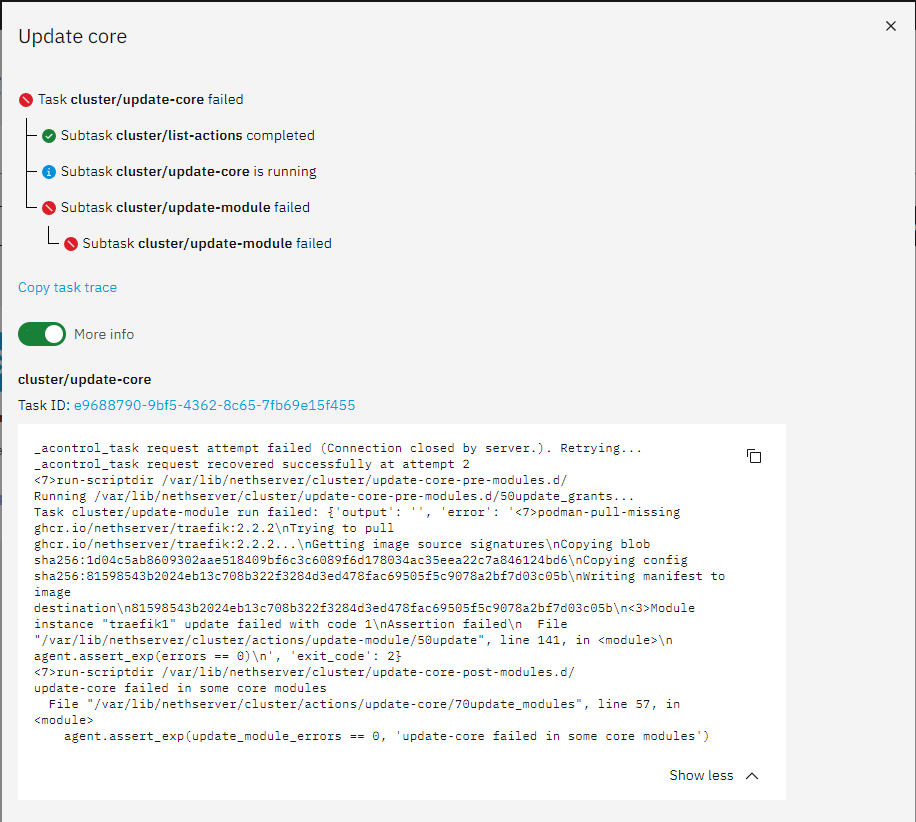
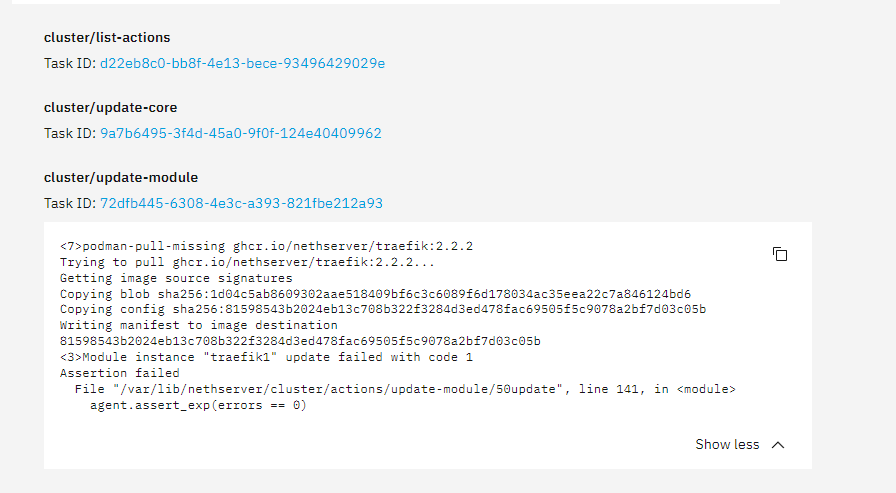
cluster/update-module
Task ID: Copy to clipboard04038089-9066-49cc-a604-20f7cd870850
<7>podman-pull-missing Package traefik · GitHub
Trying to pull Package traefik · GitHub…
Getting image source signatures
Copying blob sha256:1d04c5ab8609302aae518409bf6c3c6089f6d178034ac35eea22c7a846124bd6
Copying config sha256:81598543b2024eb13c708b322f3284d3ed478fac69505f5c9078a2bf7d03c05b
Writing manifest to image destination
81598543b2024eb13c708b322f3284d3ed478fac69505f5c9078a2bf7d03c05b
<7>podman-pull-missing docker.io/traefik:v2.11.2
Trying to pull Docker…
Getting image source signatures
Copying blob sha256:4abcf20661432fb2d719aaf90656f55c287f8ca915dc1c92ec14ff61e67fbaf8
Copying blob sha256:e2ea386b2b17283914c6ebe44480fe40ee91b08c0a9ddc27bb7b8f097bfbceef
Copying blob sha256:43642c84faa0177dd56ccef5d516b3a2884d2f7a43db9bd96fa0b3e959aad61d
Copying blob sha256:34770c1f816cac86b87c016e6cb4b72caea0eea51842af9870f2eecb35a4c7e8
Copying config sha256:dfbe0021cb966a1eaeffb1cd79f490edb9a9b90a129f32f2caddf3764f70417a
Writing manifest to image destination
dfbe0021cb966a1eaeffb1cd79f490edb9a9b90a129f32f2caddf3764f70417a
<7>extract-image Package traefik · GitHub
‘.imageroot.lst’ → ‘.imageroot.lst~’
Extracting container filesystem imageroot to /home/traefik1/.config
Всего прочитано байт: 143360 (140KiB, 176KiB/s)
imageroot/actions/
imageroot/actions/create-module/
imageroot/actions/create-module/05set_env
imageroot/actions/create-module/10expandconfig
imageroot/actions/create-module/20certificate
imageroot/actions/create-module/30grants
imageroot/actions/create-module/50create
imageroot/actions/create-module/51waitsync
imageroot/actions/delete-certificate/
imageroot/actions/delete-certificate/20writeconfig
imageroot/actions/delete-certificate/21waitsync
imageroot/actions/delete-certificate/validate-input.json
imageroot/actions/delete-certificate/validate-output.json
imageroot/actions/delete-route/
imageroot/actions/delete-route/20file
imageroot/actions/delete-route/21sync_hosts
imageroot/actions/delete-route/29waitsync
imageroot/actions/delete-route/validate-input.json
imageroot/actions/dump-custom-config/
imageroot/actions/dump-custom-config/20readconfig
imageroot/actions/get-acme-server/
imageroot/actions/get-acme-server/20readconfig
imageroot/actions/get-acme-server/validate-output.json
imageroot/actions/get-certificate/
imageroot/actions/get-certificate/20readconfig
imageroot/actions/get-certificate/validate-input.json
imageroot/actions/get-certificate/validate-output.json
imageroot/actions/get-route/
imageroot/actions/get-route/20readconfig
imageroot/actions/get-route/validate-input.json
imageroot/actions/get-route/validate-output.json
imageroot/actions/list-certificates/
imageroot/actions/list-certificates/20readconfig
imageroot/actions/list-certificates/validate-input.json
imageroot/actions/list-certificates/validate-output.json
imageroot/actions/list-routes/
imageroot/actions/list-routes/20readconfig
imageroot/actions/list-routes/validate-input.json
imageroot/actions/list-routes/validate-output.json
imageroot/actions/set-acme-server/
imageroot/actions/set-acme-server/20writeconfig
imageroot/actions/set-acme-server/30expandconfig
imageroot/actions/set-acme-server/30restart_service
imageroot/actions/set-acme-server/validate-input.json
imageroot/actions/set-certificate/
imageroot/actions/set-certificate/20writeconfig
imageroot/actions/set-certificate/21waitsync
imageroot/actions/set-certificate/validate-input.json
imageroot/actions/set-certificate/validate-output.json
imageroot/actions/set-route/
imageroot/actions/set-route/10validate_headers_name
imageroot/actions/set-route/11validate_host
imageroot/actions/set-route/20writeconfig
imageroot/actions/set-route/21sync_hosts
imageroot/actions/set-route/29waitsync
imageroot/actions/set-route/validate-input.json
imageroot/actions/upload-certificate/
imageroot/actions/upload-certificate/20decode_upload
imageroot/actions/upload-certificate/21validate_certificates
imageroot/actions/upload-certificate/22save_certificates
imageroot/actions/upload-certificate/validate-input.json
imageroot/bin/
imageroot/bin/export-certificate
imageroot/bin/module-cleanup-state
imageroot/bin/redis2yml
imageroot/bin/write-hosts
imageroot/pypkg/
imageroot/pypkg/custom_certificate_manager.py
imageroot/pypkg/get_certificate.py
imageroot/pypkg/get_route.py
imageroot/systemd/
imageroot/systemd/user/
imageroot/systemd/user/certificate-exporter.path
imageroot/systemd/user/certificate-exporter.service
imageroot/systemd/user/traefik.service
imageroot/update-module.d/
imageroot/update-module.d/10grants
imageroot/update-module.d/11dir_structure
imageroot/update-module.d/20restart
imageroot/update-module.d/30upgrade_to_beta2
chown: изменение владельца ‘./state/manual_flags’: Операция не позволена
63c2531c6e3e7041fd05c9201b41107ebb00aa373c8ad249aea80abed90e8a37
Traceback (most recent call last):
File “/usr/local/agent/actions/update-module/05pullimages”, line 85, in
).check_returncode()
^^^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/subprocess.py”, line 502, in check_returncode
raise CalledProcessError(self.returncode, self.args, self.stdout,
subprocess.CalledProcessError: Command '(‘extract-image’, 'ghcr.io/nethserver/traefik:2.2.2’)’ returned non-zero exit status 1.