hmm… ok still struggling with this.
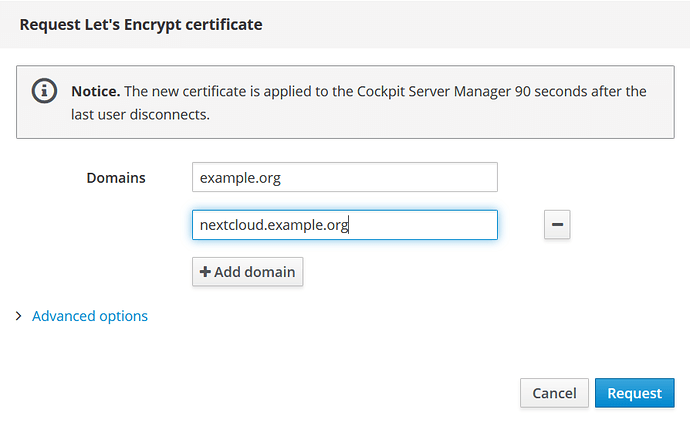
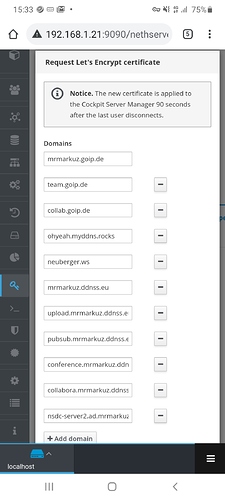
i had requested a subdomain. next.example.org (not example.org, next.example.org)
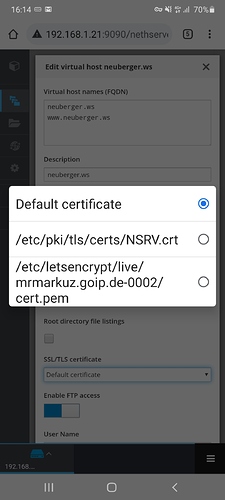
virtual host settings -> vhostname and domain are set to next.example.org
submitting those nc vhost settings gives me an error “config not saved”.
conf.d/zz_nextcloud.conf has the correct domain in the 80 and 443 sections. i dont see any links to certs tough.
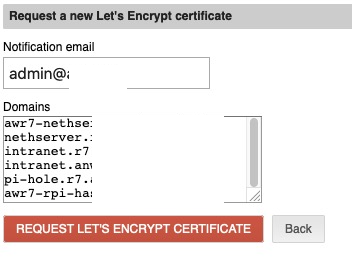
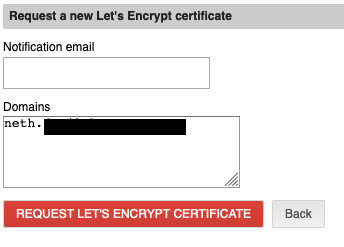
while looking through my old nexcloud notes i remembered that i was not allowed to request certs on my old system without a serverAdmin email entry in the conf files… which i dont see here on the nethserver system…
maybe im just too brain dead today…
thats the output of the error msg
echo '{"props":{"VirtualHost":"next.DOMAIN.org","TrustedDomains":["next.DOMAIN.org"],"Wellknown":"disabled"},"name":"nextcloud"}' | /usr/bin/setsid /usr/bin/sudo /usr/libexec/nethserver/api/nethserver-nextcloud/update | jq
{
"steps": 3,
"pid": 10679,
"args": "",
"event": "nethserver-nextcloud-save"
}
{
"step": 1,
"pid": 10679,
"action": "S05generic_template_expand",
"event": "nethserver-nextcloud-save",
"state": "running"
}
{
"progress": "0.33",
"time": "0.088606",
"exit": 0,
"event": "nethserver-nextcloud-save",
"state": "done",
"step": 1,
"pid": 10679,
"action": "S05generic_template_expand"
}
{
"step": 2,
"pid": 10679,
"action": "S30nethserver-nextcloud-occ-conf",
"event": "nethserver-nextcloud-save",
"state": "running"
}
{
"progress": "0.67",
"time": "5.601304",
"exit": 256,
"event": "nethserver-nextcloud-save",
"state": "done",
"step": 2,
"pid": 10679,
"action": "S30nethserver-nextcloud-occ-conf"
}
{
"step": 3,
"pid": 10679,
"action": "S90adjust-services",
"event": "nethserver-nextcloud-save",
"state": "running"
}
{
"progress": "1.00",
"time": "1.418999",
"exit": 0,
"event": "nethserver-nextcloud-save",
"state": "done",
"step": 3,
"pid": 10679,
"action": "S90adjust-services"
}
{
"pid": 10679,
"status": "failed",
"event": "nethserver-nextcloud-save"
}
{
"id": "1601494076",
"type": "EventFailed",
"message": "See /var/log/messages"
}