Hi folks, few weeks ago we have released the interface of the firewall module developed on Cockpit, this new interface represents a considerable evolutionary step, which goes far beyond the simple upgrade, in this thread I’m going to show you the salient points.
Introduction
As you certainly already know Nethesis is working on porting the current server-manager to a new modern, high-performance web interface based on cockpit with many more features.
Currently this interface can be installed from the software center and works in parallel with the current interface on a specific port (9090).
The project with the new interface is to cover and improve the functionality of the current one (as far as it is possible to do without breaking compatibility) and then proceed to the definitive switch that will open the way for further developments.
The “core” part of Nethserver has already been released, in this case instead we have dealt with rewriting the most “classic” firewall part (rules, multiwan, traffic shaping, connections tracking).
UTM services will follow later (IPS, proxy, content filter, VPN and so on).
Installation
If you have installed nethserver-cockpit from the software center and you have the firewall packages you will find the firewall application available on the new interface:
I advise you to click on “add shortcut” to have it always available in the main menu
The image shows the different sections available.
News
The firewall interface is the result of a total redesign and analysis of the current critical issues to have a product that is simple to use but complete, these are the guidelines that you will find on different panels.
-
Smart search
On many panels it is possible to search by host, ip, roles or whatever to speed up the reading and compilation of the rules -
Advanced Properties
When creating the rules only the most common fields are shown, but it’s possible to display other uncommon parameters just clicking the field “Advanced” -
Self-contained sections
Some sections that previously shared some configuration panels (multiwan, traffic shaping) are now separate and in each of them it is possible to have all the necessary informations and editing possibilities. -
Possibility to also use IP directly without having to create a specific firewall object
-
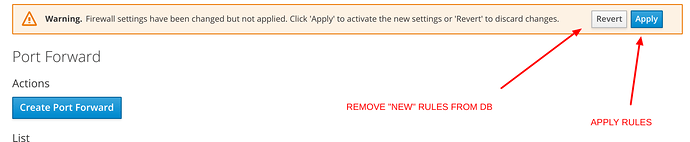
Changing configurations affects only the database
The firewall runs on the basis of the configurations made, whenever there are changes to the configuration these are not applied immediately, but written in a temporary database.
To make the changes effective, click on the apply button that appears at the top right.
This way, you get faster in creating the rules. -
Revert
As long as the new rules created have not been applied you can delete them by clicking on the appropriate Revert button.
The Revert button eliminates all the new rules from the temporary database and at the same time makes the top bar disappear (since there are no more rules to apply).
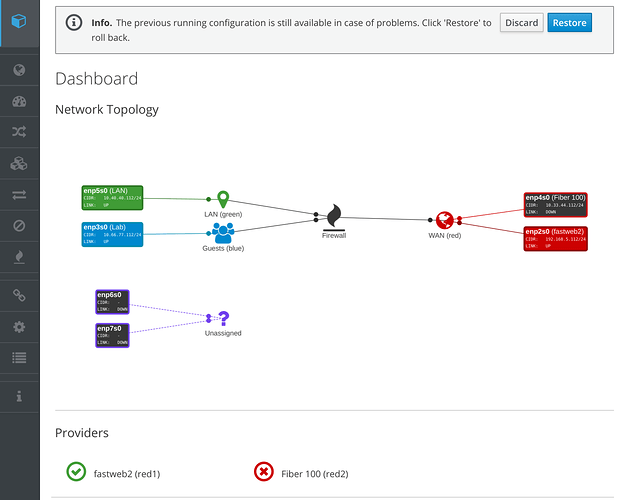
Firewall
The firewall section shows the network topology and other summary information.
Objects and sNAT
These 2 sections have remained essentially the same, more news will be possible after we’ll leave the current interface.
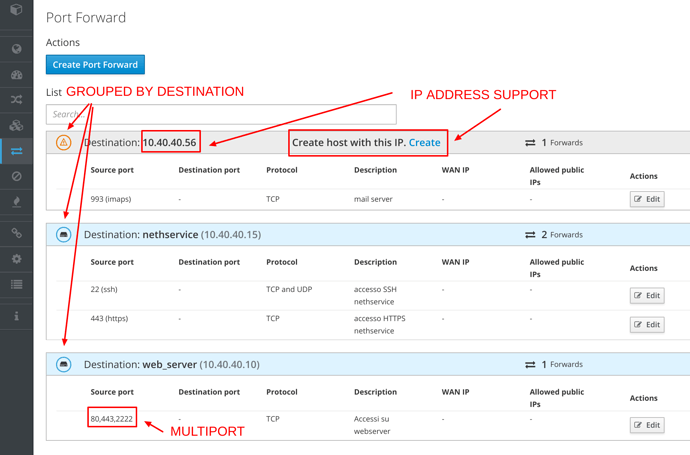
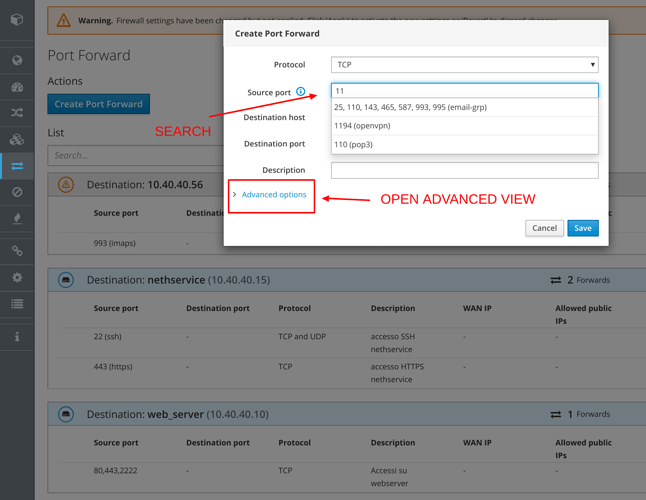
Port Forward
This section has been completely reorganized:
- The rules are grouped by destination
- Rules with multiple ports (comma separated) are also supported
- You can create rules directly using the IP address
The rule creation phase has completely changed:
When entering the fields the search finds all the correspondences, it is possible to specify other protocols besides tcp and udp (eg: ah, esp, gre …), the port forward rules are not applied immediately, but it is possible to create all the desired rules and then apply them only once for the benefit of the rapid configuration of the device.
Portrange and multiple ports separated by commas are supported.
Once you have created the port forward rules, you can apply them by clicking on the Apply button at the top of the page:
Or remove them in bulk (only the new rules not yet applied) by clicking on Revert.
Further improvements about management of allowed public IPs will follow after the old interface will be abandoned (at the moment it is not possible because they would break compatibility).
Firewall Rules
The Firewall Rules Section which previously gave the possibility to also create routing rules, Qos rules and rules “from/to” the firewall was divided into separate sections in order to be more intuitive and better organized.
The sections are as follows:
- Rules: Rules to block/allow traffic passing through the firewall
- Local rules: Rules that block/allow traffic to/from the firewall
- Traffic shaping: The Qos rules are made directly in their own section
- WAN: Policy routing rules are made in WAN section
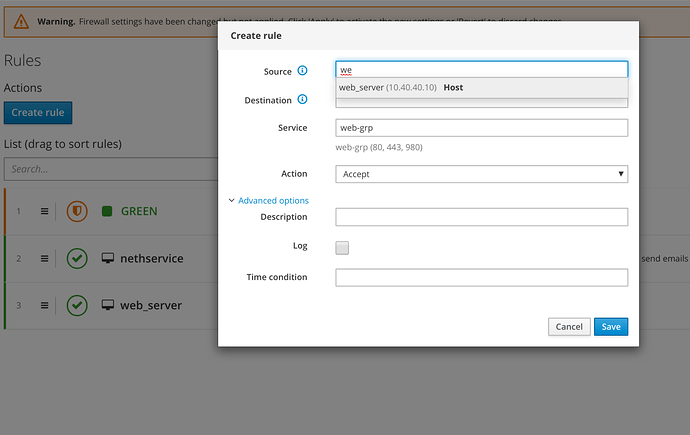
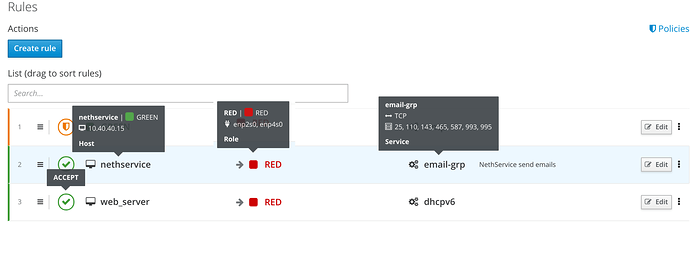
Rules
The creation of the rules has been simplified and speeded up
Rules are showed in a very simple way, they only show very important parameters, but you just need to pass the mouse over the fields to get more informations on the source, destination, services, etc.
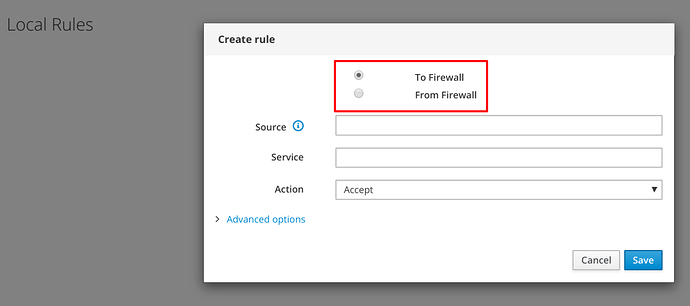
Local Rules
Similar to the previous ones but specifically referring to traffic to / from the firewall.
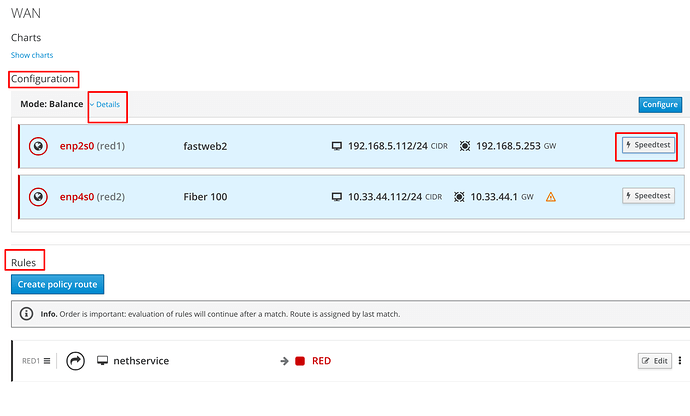
WAN
The WAN section contains the data relating to the configuration of the various REDs and the routing policy rules.
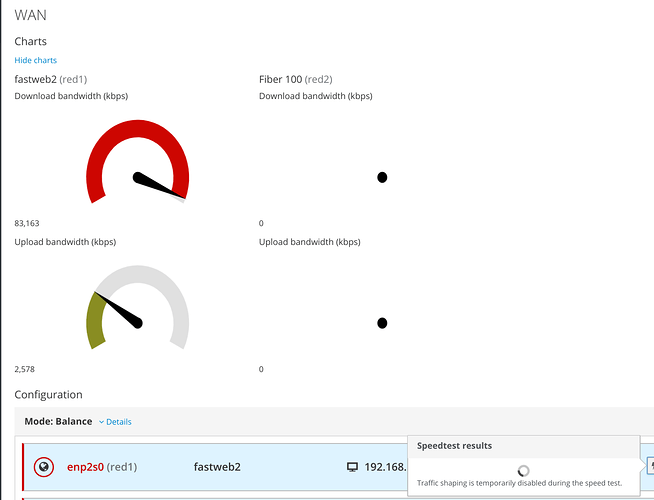
It is possible to view band in upload download in real time and perform speedtest on the specific connectivity, the collected data can be assigned to the interface.
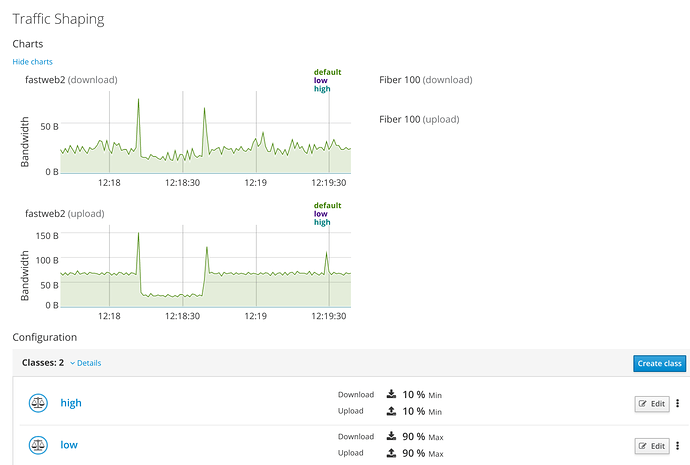
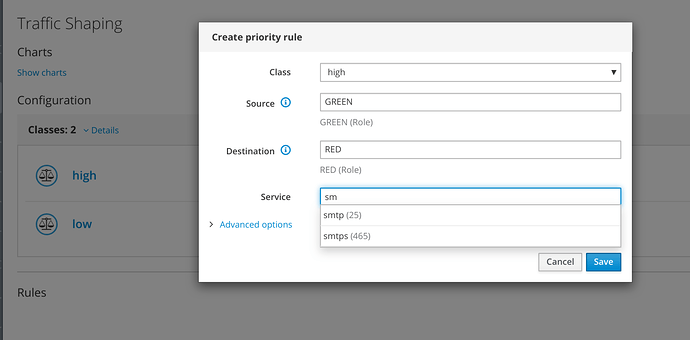
Traffic Shaping
Also in this case all the information related to traffic shaping is managed on this page:
You can create QoS rules :
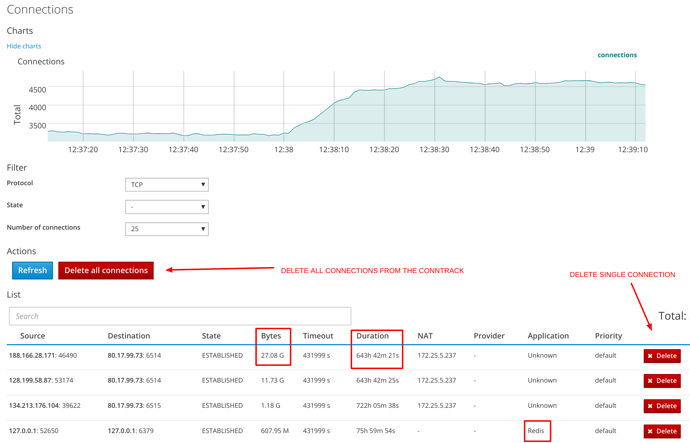
Connections
Through this new panel it is possible to view the connections table, filter them, analyze them and even remove them (individually or globally) if desired.
The panel also shows the duration and traffic exchanged by the connections as well as the fact that they are natted or not, if the DPI module is installed the recognized applications are shown in the Application section.
Logs
It allows you to view the firewall.log file and follow it “live”.
Settings
In this section there are the general configurations (those currently accessible from the Firewall Rules page -> Configure) and the general switch for the Hairpin NAT on the Port Forward.
I invite you to try the new interface and let us have your feedback to improve it further.
Thanks to @edoardo_spadoni and @giacomo for the excellent work they have done!
I’m waiting for your feedbacks! 
Davide