Thanks,
Ok to get keycloak to use a ghost I did this and it works:
- create a conf file in /etchttpd/conf.d
conf file
<VirtualHost *:80>
ServerName key.nethserver.com
Redirect “/” “https://key.nethserver.com/”
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/nethserver.crt
SSLCertificatekeyFile /etc/pki/tls/certs/key.nethserver.key
SSLCertificateChainFile /etc/pki/tls/certs/nethserver.ca-bundle.crt
ErrorLog /var/log/keycloak/keycloak-error.log
CustomLog /var/log/keycloak/keycloak-access.log combined
ProxyPreserveHost On
ProxyRequests Off
RequestHeader set X-Forwarded-Proto "https"
RequestHeader set X-Forwarded-Port "443"
SSLProxyEngine On
SSLProxyCheckPeerCN on
SSLProxyCheckPeerExpire on
ProxyPass / http://127.0.0.1:8080/
ProxyPassReverse / http://127.0.0.1:8080/
#ProxyHTMLURLMap / http://127.0.0.1:8080/
</VirtualHost>
- Then I restarted httpd service
Now I can access keycloak with https://key.nethserver.com
However, when I try a sync with the users, keycloak gets the users, however when I try to add a user or modify an imported user, I get an error,
Here is a snap of my error.log from keycloak.
Error
Caused by: javax.naming.NoPermissionException: [LDAP: error code 50 - Insufficient Access Rights]; remaining name ‘uid=kc,ou=People,dc=directory,dc=nh’
at com.sun.jndi.ldap.LdapCtx.mapErrorCode(LdapCtx.java:3162)
at com.sun.jndi.ldap.LdapCtx.processReturnCode(LdapCtx.java:3100)
at com.sun.jndi.ldap.LdapCtx.processReturnCode(LdapCtx.java:2891)
at com.sun.jndi.ldap.LdapCtx.c_modifyAttributes(LdapCtx.java:1475)
at com.sun.jndi.toolkit.ctx.ComponentDirContext.p_modifyAttributes(ComponentDirContext.java:277)
at com.sun.jndi.toolkit.ctx.PartialCompositeDirContext.modifyAttributes(PartialCompositeDirContext.java:192)
at com.sun.jndi.toolkit.ctx.PartialCompositeDirContext.modifyAttributes(PartialCompositeDirContext.java:181)
at javax.naming.directory.InitialDirContext.modifyAttributes(InitialDirContext.java:167)
at javax.naming.directory.InitialDirContext.modifyAttributes(InitialDirContext.java:167)
at org.keycloak.storage.ldap.idm.store.ldap.LDAPOperationManager$7.execute(LDAPOperationManager.java:553)
at org.keycloak.storage.ldap.idm.store.ldap.LDAPOperationManager$7.execute(LDAPOperationManager.java:549)
at org.keycloak.storage.ldap.idm.store.ldap.LDAPOperationManager.execute(LDAPOperationManager.java:745)
at org.keycloak.storage.ldap.idm.store.ldap.LDAPOperationManager.modifyAttributes(LDAPOperationManager.java:549)
… 81 more
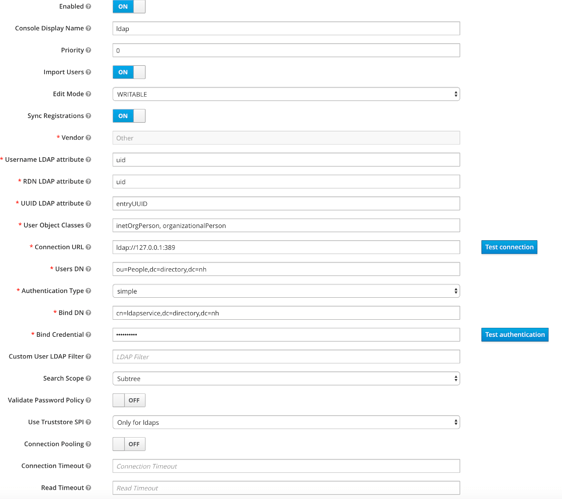
I use the following settings:
Therefore I believe I need a superuser for the ldap, however I have no idea which one to use.
I tried with libuser, uid=admin etc and I cannot get it to work.
The I can’t nor add new users from keycloak, I would like to be able to manage users from that interface and not phpldapadmin and user from NS interface (too limitative)
EDIT:----
Just being curious and reading the documentation I found the user password for libuser. With it it works. Perfectly well.
However I believe that this is not the right thing to user as a user for ldap admin.
Thank you very much