Salut @oneitonitram ,
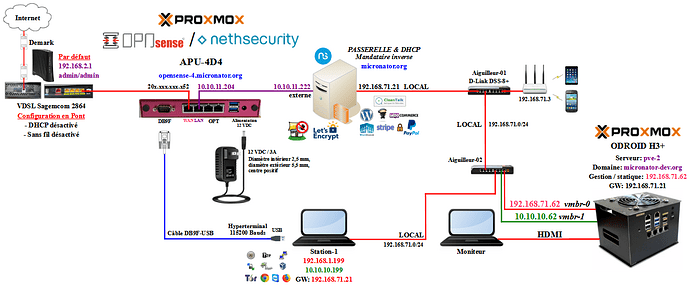
With NethServer-7.9, I used the server to request the PPPOe as it is much easier to configure NethServer with its reverse proxy for redirection of domains, ports, etc.
I also used NethServer-7 to handle the DHCP as I have a router on the LOCAL LAN as a DHCP relay for Wireless devices. If I were using the modem for DHCP then the Wireless router would still have to be on LOCAL LAN to be protected by NethServer-7 and therefore the server would have to be the relay for the DHCP. Much easier to configure the Wireless router to be the relay.
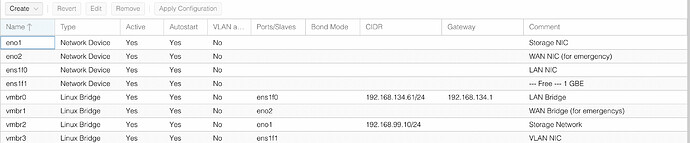
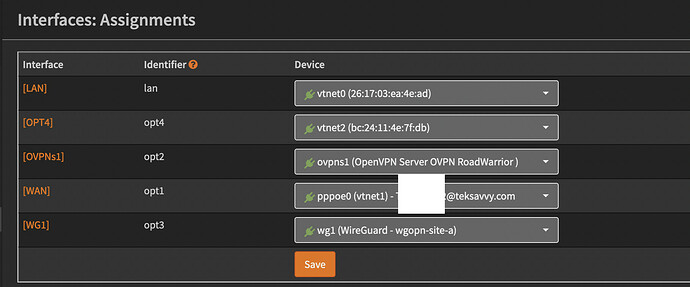
For NS-8, I wanted to replicate the same way and use the Proxmox filrewall option to handle the protection and also host NS-8, so no need for another box for the firewall.
The problem with this approach is that Proxmox can not be the PPPOe requester as it will jeopardise some of its functionality because of some version problem with one of the component of the PPPOe software needing a different version of the one used by Proxmox.
Another problem with NS-8 requesting the PPPOe is that it will be directly connected to the internet and it will have no direct protection while been exposed.
The solution I was thinking was to use another box for the firewall. This solution need two machines to do the job and I wanted to use only one.
Another way will be to host the firewall inside Proxmox. That way, Proxmox can take backups of the VMs and transfer those backups on another machine.
The problem is which firewall to use? NethSecurity is not ready yet and it will take some time to mature to a level of trustability. For the time been, I reopened my studies of OPNsense…
At some point I was even considering using Porxmox hosting ISPconfig with its Fail2ban/Amavis/firewall/web hosting etc… (it has everything, just like NethServer-7).
There is only one problem with ISPconfig; it has no PPPOe possibility for the same reason as Proxmox, i.e some software component version incompatibility related to Debian PPPOe.
Maybe using Rocky to host ISPconfig but now, since the story of CentOS, I only go with Linux distros that I am sure will still be there for many years and won’t change their lisense; Debian is the only one to count on.
Like a very large number of people, I am inconsolable at the loss of the functionality and robustness of NethServer-7.
Every night I wake up to curse CentOS, RedHat and IBM.
Michel-André