Ohh … coool finally this is going on … 
Just to mention… all configuration is still working just fine.
Now am curious about this free radius server.
is it whats used to authenticate PPPOE users?
if say, i am offering internet services through edgemax equipments, can this be a good use case for it to authenticate users?
Hi Martin
RADIUS does stand for:
Remote Access Dial-In User Server.
At all providers, RADIUS is the large, fast system authenticating users. Before, users “dialed in” to the internet, nowadays, it’s mostly DSL, Cable or Fibre - but behind the scenes it’s almost always a RADIUS server.
RADIUS can not only authenticate users, it can also log (and limit) usage per user/connection.
In short, a very powerful software package! Technologies have come and gone, (Anyone still remembers a 56K Modem? or an Acoustic Coupler with 1200 Baud?) but it’s still a RADIUS handling it!
My 2 cents
Andy
PS: OPNsense includes a full Radius…
with samba AD authentication ?
If you use the LetsEncrypt Certs (Transfered with a script triggered by a Software Hook on the acme script) in your OPNsense, you can even use NethServer’s AD as Userbase in your OPNsense.
So this means, yes, OPNsense can use NethServers AD for Authentification, and thus also for FreeRadius…
Mes deux Centimes
Andy
I should take time to find some interest on free-radius but the documentation is awful…
As stated here, https://freeradius.org/documentation/, there are a lot of outdated docs lying about. The software functionality, APIs and such have changed greatly in the past 4 years…
Many people try to find documentation by Googling keywords, but this method is not generally productive. Most of the links are to other people asking the same question, or to out-dated third party documentation. It is easy to get lost in a mess of contradictory and confusing documentation, leading to frustration and a badly configured server.
Most third-party documentation and How-To’s are wrong and outdated. We strongly suggest that you do not follow any documentation which is more than 4 years old. If you do follow such ancient documentation, the result will likely be a server that does not work.
This is a better starting point:
Mes deux centimes
Andy
the copyright of this documentation : Copyright © 2014 Network RADIUS SARL 58 of 58

so I have to read another one 
My understanding of a RADIUS server is that it is a layer between a user or application to grant access to a service WITHOUT having to know the credentials…
This way the user or application asks the RADIUS server: I have this account and that password. Can I go on? The RADIUS server passes the request on to the account provider. The account provider says yes or no, If yes the RADIUS server gives a ‘access granted’, if no the RADIUS server gives an ‘access denied’.
The RADIUS server does not know the credentials, it only gets a yes or no from the accountprovider.
really? so i can just deploy opnsense and it will handle Radius auth.
Hi Martin
Yes. With whatever options you may need. Even failover for redundancy. (The whole firewall opnsense is ha with carp)…
My 2 cents
Andy
Seems still to be impossible to install from repos. How can I build the package from git? Can you sketch the procedure?
The LDAP service provided by NethServer is easily adapted to any application. I adapted my custom PHP organization user interface to authorize using LDAP no problems at all.
It should also be possible to setup freeradius to authorize using LDAP, but in this case it makes sense to use ntlm-auth, because:
- freeradius configuration files and freeradius itself are a bit difficult to unterstand at first, it will probaby be a bit more complex to setup auth using LDAP, but probably possible, a good testing environment is necessary
- using ntlm-auth corresponds very closely to MS AD - expired passwords are not allowed to authorize, as well as expired or blocked accounts fail to authorize, as far as I know samba still supports the protocol
- works with a single command under nsdc container, no problems so far with a userbase of ~1500 users where freeradius is critically needed for all users
- in my case radius is used for WPA-Enterprise only, users have to enter the details once and save the connection, not enter the credentials everytime (captive portal), also MSCHAPv2 works out of the box
- MSCHAPv2 is still supported starting from Windows 7 to 10, altrough Windows 7 is not just enter username and password, but needs a bit more configuration. W7 and lower versions are EOL, but it is still possible to connect (for example if a guest user should connect to the WLAN using a outdated OS)
- iOS and Android works with no problems as well
Downsides:
- outdated and insecure authentication protocol (MSCHAPv2)
I use freeradius eap module besides ntlm-auth with a certificate to authenticate WLAN clients where no user account should be used. For example - laptop computers and the configuration and certificate is pushed trough GPO. Works no problems at all and NethServer updates havent done any harm to the configuration.
Wish there was a way to get this working, I have been putting off an install for almost a year, keep hoping one of the wizards here would figure this out. 
While I understand that I can use OpenSense to do it, would be much nicer to have Nethserver handle it all. Guess I better give the Opensense option a try.
How about if Freeradius would be installed directly in the AD container? Then the connection between Freeradius and AD could go via localhost only. Would that be a security gain?
Regards
yummiweb
The mschap key exchange would then happen on localhost. This could in theory make the connection a bit more secure, since ntlm_auth runs inside container.
I havent tought about this topic in a while… One way is to migrate the wireless authentication to captive portal based authentication instead of using radius+eap+mschapv2. The support is now pretty good and most devices should support autologin.
It might make sense not to include this solution in next release of NethServer, because of the weak ntlm protocol. On the other hand in Nethserver - as it is based on CentOS, you can install freeradius manually and configure like I did. But distros like Zentyal still include and enable ntlm_auth as far as I know, havent used/tested those other servers for quite while tho.
Really interesting, do you think you could write a howto, this could be a start before any rpm solution
Hi Kellerman,
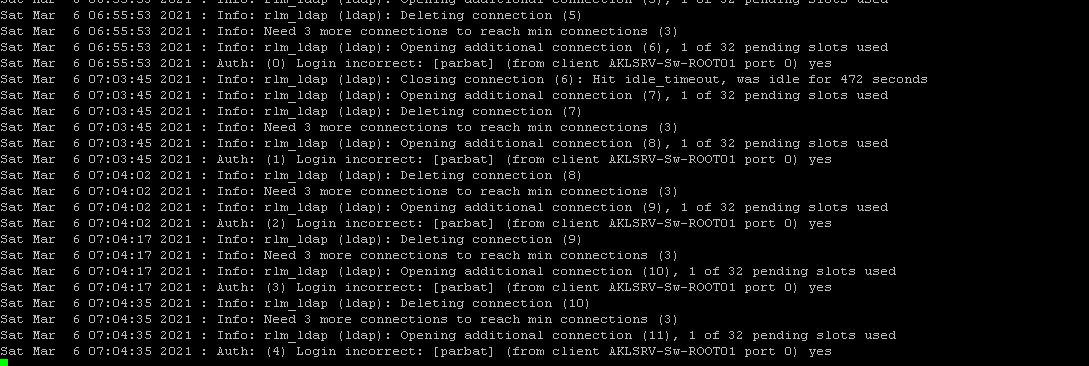
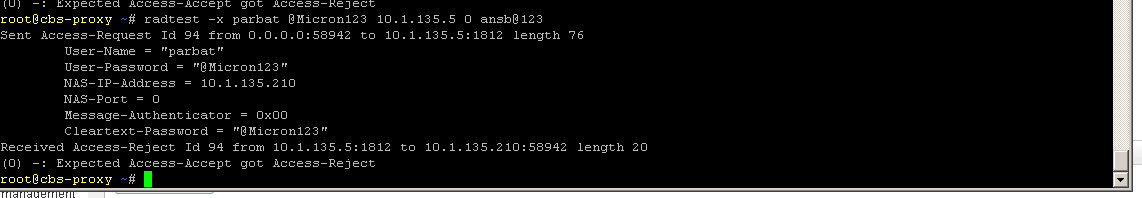
I have tried a lot to get it working on Nethserver 7.9. Followed your instruction step by step verified I comply properly more than thrice but failed to get authenticated using pap or mschap.
Please find attached screenshots, help me if you have time to spare with me.
Thanks and regards,
Prashant
I am having success with pap by editing mods-enabled\default but not with mschap.
Can some one share mods-enabled\default and mods-enabled\inner-tunnel configs. Below is output for radiusd -X
(0) Received Access-Request Id 219 from 127.0.0.1:53064 to 127.0.0.1:1812 length 133
(0) User-Name = “kjadhav”
(0) NAS-IP-Address = 10.1.135.5
(0) NAS-Port = 1812
(0) Message-Authenticator = 0xc371dc0a0d683ef1274fe877486eb437
(0) MS-CHAP-Challenge = 0x28d890dd38bf4734
(0) MS-CHAP-Response = 0x0001000000000000000000000000000000000000000000000000cece725ff2c921f645ac99a36753b7d150f260660e7d01a7
(0) # Executing section authorize from file /etc/raddb/sites-enabled/default
(0) authorize {
(0) policy filter_username {
(0) if (&User-Name) {
(0) if (&User-Name) -> TRUE
(0) if (&User-Name) {
(0) if (&User-Name =~ / /) {
(0) if (&User-Name =~ / /) -> FALSE
(0) if (&User-Name =~ /@[^@]@/ ) {
(0) if (&User-Name =~ /@[^@]@/ ) -> FALSE
(0) if (&User-Name =~ /…/ ) {
(0) if (&User-Name =~ /…/ ) -> FALSE
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+).(.+)/)) {
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)/)) -> FALSE
(0) if (&User-Name =~ /./) {
(0) if (&User-Name =~ /\./) -> FALSE
(0) if (&User-Name =~ /@./) {
(0) if (&User-Name =~ /@./) -> FALSE
(0) } # if (&User-Name) = notfound
(0) } # policy filter_username = notfound
(0) [preprocess] = ok
(0) [chap] = noop
(0) mschap: Found MS-CHAP attributes. Setting ‘Auth-Type = mschap’
(0) [mschap] = ok
(0) [digest] = noop
(0) suffix: Checking for suffix after “@”
(0) suffix: No ‘@’ in User-Name = “kjadhav”, looking up realm NULL
(0) suffix: No such realm “NULL”
(0) [suffix] = noop
(0) eap: No EAP-Message, not doing EAP
(0) [eap] = noop
(0) [files] = noop
rlm_ldap (ldap): Reserved connection (0)
(0) ldap: EXPAND (uid=%{%{Stripped-User-Name}:-%{User-Name}})
(0) ldap: --> (uid=kjadhav)
(0) ldap: Performing search in “dc=AD,dc=AGRASENBANK,dc=CO,dc=IN” with filter “(uid=kjadhav)”, scope “sub”
(0) ldap: Waiting for search result…
TLS certificate verification: Error, unable to get local issuer certificate
rlm_ldap (ldap): Rebinding to URL ldaps://ad.agrasenbank.co.in/CN=Configuration,DC=ad,DC=agrasenbank,DC=co,DC=in
rlm_ldap (ldap): Waiting for bind result…
rlm_ldap (ldap): Bind successful
(0) ldap: Search returned no results
rlm_ldap (ldap): Deleting connection (0)
Need 6 more connections to reach 10 spares
rlm_ldap (ldap): Opening additional connection (5), 1 of 28 pending slots used
rlm_ldap (ldap): Connecting to ldaps://10.1.135.6:636
TLSMC: MozNSS compatibility interception begins.
tlsmc_convert: INFO: cannot open the NSS DB, expecting PEM configuration is present.
tlsmc_intercept_initialization: INFO: successfully intercepted TLS initialization. Continuing with OpenSSL only.
TLSMC: MozNSS compatibility interception ends.
TLS certificate verification: Error, unable to get local issuer certificate
rlm_ldap (ldap): Waiting for bind result…
rlm_ldap (ldap): Bind successful
(0) [ldap] = notfound
(0) [expiration] = noop
(0) [logintime] = noop
(0) pap: WARNING: No “known good” password found for the user. Not setting Auth-Type
(0) pap: WARNING: Authentication will fail unless a “known good” password is available
(0) [pap] = noop
(0) } # authorize = ok
(0) Found Auth-Type = mschap
(0) # Executing group from file /etc/raddb/sites-enabled/default
(0) authenticate {
(0) mschap: Client is using MS-CHAPv1 with NT-Password
(0) mschap: Executing: /usr/bin/nsdc-run -e /usr/bin/ntlm_auth_nsdc %{%{Stripped-User-Name}:-%{%{User-Name}:-None}} %{%{mschap:Challenge}:-00} %{%{mschap:NT-Response}:-00}}:
(0) mschap: EXPAND %{%{Stripped-User-Name}:-%{%{User-Name}:-None}}
(0) mschap: --> kjadhav
(0) mschap: mschap1: 28
(0) mschap: EXPAND %{%{mschap:Challenge}:-00}
(0) mschap: --> 28d890dd38bf4734
(0) mschap: EXPAND %{%{mschap:NT-Response}:-00}}
(0) mschap: --> cece725ff2c921f645ac99a36753b7d150f260660e7d01a7}
(0) mschap: ERROR: Program returned code (1) and output ‘The attempted logon is invalid. This is either due to a bad username or authentication information. (0xc000006d)’
(0) mschap: External script failed
(0) mschap: ERROR: External script says: The attempted logon is invalid. This is either due to a bad username or authentication information. (0xc000006d)
(0) mschap: ERROR: MS-CHAP2-Response is incorrect
(0) [mschap] = reject
(0) } # authenticate = reject
(0) Failed to authenticate the user
(0) Login incorrect (mschap: Program returned code (1) and output ‘The attempted logon is invalid. This is either due to a bad username or authentication information. (0xc000006d)’): [kjadhav/] (from client localhost port 1812)
(0) Using Post-Auth-Type Reject
(0) # Executing group from file /etc/raddb/sites-enabled/default
(0) Post-Auth-Type REJECT {
(0) attr_filter.access_reject: EXPAND %{User-Name}
(0) attr_filter.access_reject: --> kjadhav
(0) attr_filter.access_reject: Matched entry DEFAULT at line 11
(0) [attr_filter.access_reject] = updated
(0) [eap] = noop
(0) policy remove_reply_message_if_eap {
(0) if (&reply:EAP-Message && &reply:Reply-Message) {
(0) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE
(0) else {
(0) [noop] = noop
(0) } # else = noop
(0) } # policy remove_reply_message_if_eap = noop
(0) } # Post-Auth-Type REJECT = updated
(0) Delaying response for 1.000000 seconds
Waking up in 0.9 seconds.
(0) Sending delayed response
(0) Sent Access-Reject Id 219 from 127.0.0.1:1812 to 127.0.0.1:53064 length 61
(0) MS-CHAP-Error = “\000E=691 R=1 C=a9f1c4fe098174ba V=2”
Waking up in 3.9 seconds.
(0) Cleaning up request packet ID 219 with timestamp +19
Ready to process requests