We’re excited to announce the release of NethSecurity 8.6 (NethSecurity 8-24.10.0-ns.1.6.0) based on OpenWrt 24.10.
N.B. We strongly recommend always using the latest version when migrating from NethSecurity 7.
Update Now 
 Release Highlights
Release Highlights
NethSecurity 8.6 introduces several new features and improvements. The image also includes updates released after version 8.5 through package updates.
 New Features
New Features
High Availability (Beta)
High Availability for maximum operational continuity ![]()
Support for High Availability with two-node cluster in backup mode has been introduced.
- The primary firewall (FW1) analyzes and processes all traffic
- The secondary firewall (FW2) is connected to all networks but does not process traffic
The secondary firewall automatically takes over when the primary loses communication for any reason, such as power failure, network port failure, etc.
High Availability handles:
- Instant and continuous monitoring of FW1’s operational status
- Configuration synchronization from FW1 to FW2 to ensure proper service transition
High Availability configuration is currently available only via command line.
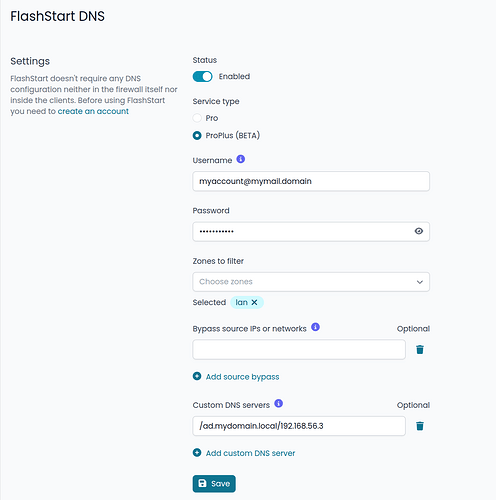
FlashStart ProPlus (Beta)
The FlashStart integration has been completely renewed and now allows you to choose between the Pro and ProPlus versions.
The ProPlus version introduces support for multiple filtering profiles, greater flexibility, and user-level policy enforcement.
- Up to 5 independent profiles, each with its own filtering configuration (categories, Safe Search, etc.)
- More features (IP blocker, APP blocker, Remote Agent for mobile clients)
Profiling can be done using NethSecurity host sets or directly from Microsoft AD server users and groups.
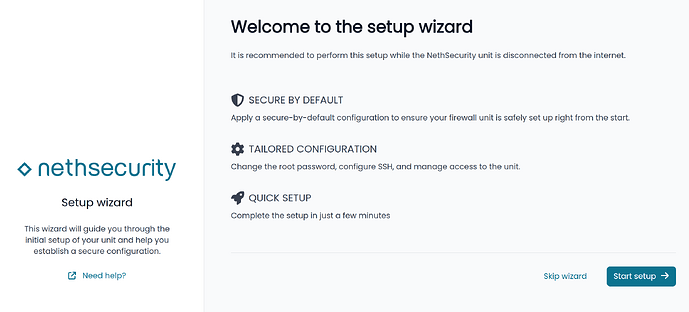
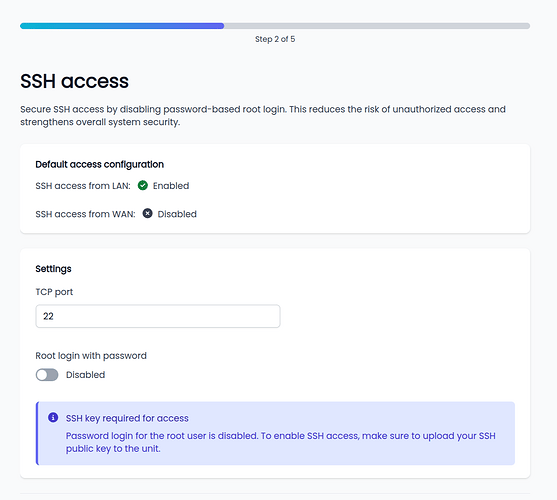
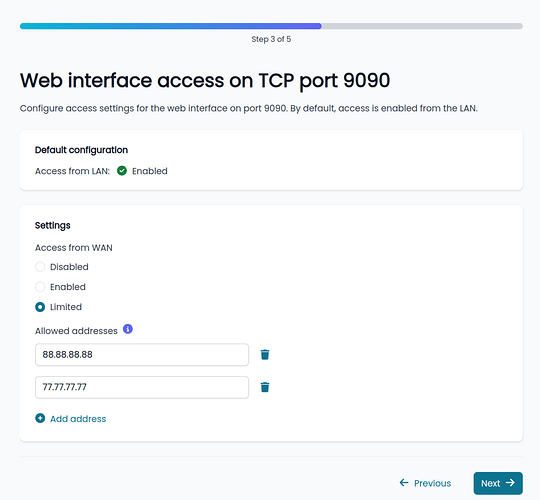
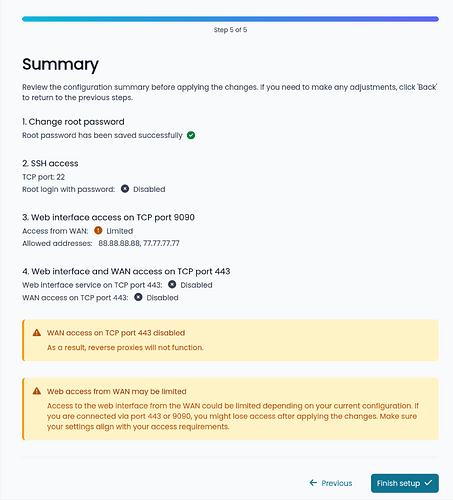
Initial security wizard
Upon first login, a setup wizard helps the user configure security-related parameters to immediately enforce secure passwords and reduce firewall service exposure.
The wizard appears after login if not yet completed.
Here are some screenshots of the wizard.
Persistent logs by default
On bare metal installations, if the disk has available space, NethSecurity 8.6 automatically configures the storage section to enable persistent logs on all installations without admin intervention.
For virtual installations, it is recommended to add a second disk and configure log storage on it (admin intervention is required in this case).
 Changes and improvements
Changes and improvements
Threat Shield: Manage Blocked IPs from the UI
A web interface has been added to view, search, and unblock IPs blocked by Brute Force protection. Now you can manage IPv4 and IPv6 blocklists directly from the UI.
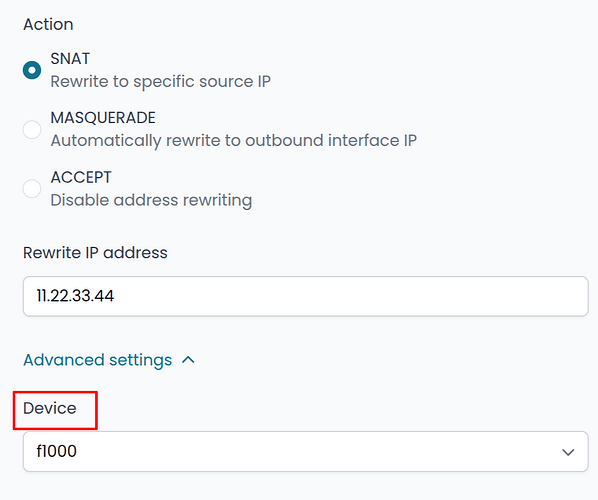
SNAT interface
It’s now possible to create SNAT rules for specific network interfaces, not just zones as before, allowing for better management of advanced routing or failover scenarios.
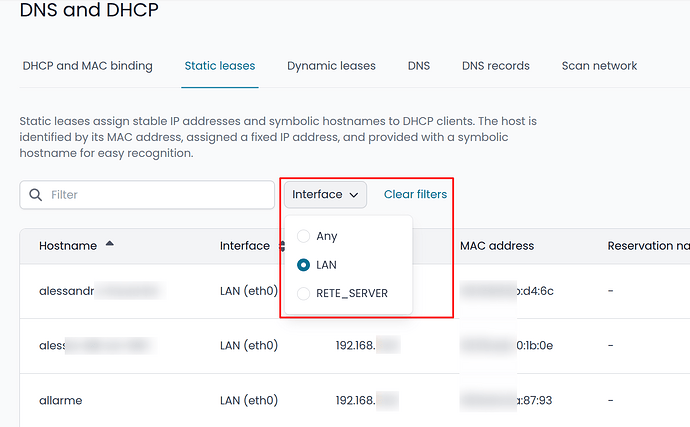
Static lease dropdown filter
A new menu allows filtering DHCP static leases by interface, making it easier to manage complex environments.
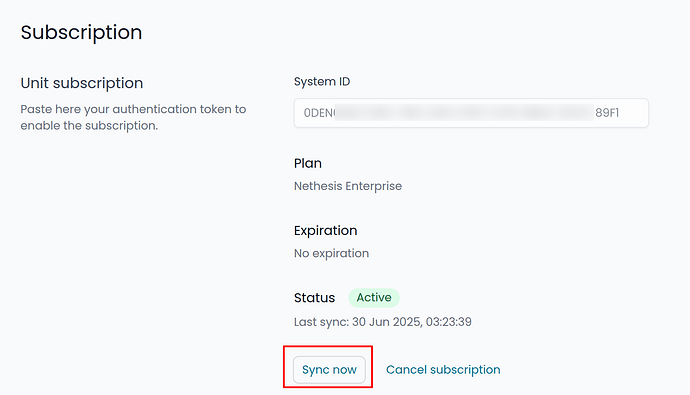
Service center sync status in the UI
The Subscription page now displays connection status, last sync date and time, and a “Send Now” button. This helps quickly verify communication with the my.nethesis.it portal.
Other features already introduced in version 8.5 via automatic updates
-
Sudo mode
A new “sudo mode” has been introduced, requiring password re-entry for sensitive actions such as managing two-factor authentication (2FA) or SSH key updates. This improves security by ensuring that elevated permissions are only valid for a limited time after authentication. -
Custom DHCP options
The DHCP server now supports custom options, allowing admins to specify option numbers and values directly from the interface. This adds flexibility for advanced network configurations. -
GRE support for port forwarding
The port forwarding interface now supports the GRE protocol, providing greater flexibility for network setups. -
Warnings for unencrypted backups
Starting with the release of NethSecurity 8.7 (Q3/2025), the Nethesis Service Center (my.nethesis.it and my.nethserver.com) will no longer accept unencrypted backups.
This is due to security and data privacy concerns.
Verification is already active: if a system has a valid subscription and the backup is not encrypted, a warning is generated:backup:config:notencypted.
To allow time for compliance (you just need to create a passphrase), the service center will continue accepting unencrypted backups until version 8.7 is released.
More information is available in the documentation.
 Bug fixes
Bug fixes
-
OpenVPN: user rename handling and access tracking
Fixed an issue where renamed or deleted AD users could still log in with old credentials and OTP. The system now verifies user existence and updates access tracking from the UI. -
UI: blocked firewall zone names starting with numbers
The UI no longer allows creation of firewall zones with names starting with a digit, preventing rule application issues. -
OpenVPN Road Warrior: disconnects after one hour
Renegotiation settings were adjusted to prevent unexpected disconnections for clients using “Username and Password” or “Certificate, Username and Password”. -
Destination address in port forwarding no longer mandatory
It’s now possible to create port forwarding rules without requiring a destination address, to redirect traffic to the firewall itself with a different port. -
Let’s Encrypt pending certificate requests can now be deleted
You can now delete Let’s Encrypt certificate requests even if they’re still pending. -
OpenVPN migration: editing tunnels with hyphens in the name
Net-to-Net OpenVPN tunnels with hyphens in the name can now be modified post-migration. The UI accepts valid imported names. -
Root filesystem usage after restore
Fixed an issue where the log directory could end up on the root filesystem after a restore, risking full disk usage.
The full list of fixes is available here:
 Known Bugs
Known Bugs
The full list of known bugs is available here:
How to update NethSecurity 
- Go to the System → Updates section in the UI
- The UI should show a new available version (NethSecurity 8-24.10.0-ns.1.6.0)
- Click Update system (the update includes automatic device reboot)
 What is NethSecurity?
What is NethSecurity?
NethSecurity is a powerful, open-source Linux firewall designed to simplify network security deployment. It offers full-featured protection and an easy-to-use interface.
Choose your preferred Subscription Plan
A NethSecurity subscription ensures that your deployment is backed by top-tier technical expertise and the support necessary to maintain your organization’s security infrastructure.
Subscribing also grants exclusive access to the Enterprise repository, which includes Automatic Updates, advanced DPI Applications/protocol detection, and VPN integration with LDAP/AD user databases.
 Get your subscription
Get your subscription
 Help shape NethSecurity’s future
Help shape NethSecurity’s future
Your feedback is invaluable as we continue to refine and enhance NethSecurity. Please share your thoughts, report issues, and suggest features by opening a new topic in the NethSecurity category, using tags like Feature, Bug, or Support.