We are excited to announce the release of NethSecurity 8.5 (NethSecurity 8-24.10.0-ns.1.5.1) , based on OpenWrt 24.10.
Version 8.5 brings a major kernel upgrade:
- we are moving to kernel 6.6.73 (from 5.15.167)
- general improvements
- performance enhancements
- expanded hardware support.
Among the changes introduced with the new kernel, there is network card ordering, which in very specific and limited cases might differ from previous versions.
We therefore invite you to test this new version in a lab environment on the hardware you typically use.
More details on network card management changes can be found here:
NethSecurity 8.5 Network Card Management
 Important
Important 
In version ns.1.5.0, a problem related to network interface bonding was identified, which led us to promptly release a new image (ns.1.5.1).
Please make sure to download and use only version 1.5.1. If you have already downloaded version 1.5.0 (for example, to write a USB key), we recommend deleting it.
 Release Highlights
Release Highlights
NethSecurity 8.5 introduces several new features and improvements. Additionally, known bugs in NethServer 7.9 migration have been fixed (make sure to use the latest version of Firewall Migration on NethSecurity 7.9).
This image also includes the updates released after version 8.4 through package updates.
 New Features
New Features
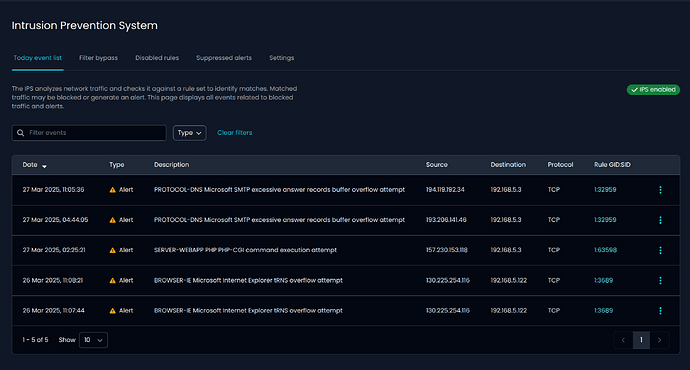
IPS: UI Released
Intrusion Prevention System that is capable of performing real-time traffic analysis and packet logging on IP networks
Threat Shield DNS: UI Released
Threat shield DNS blocks any request to domains considered malicious
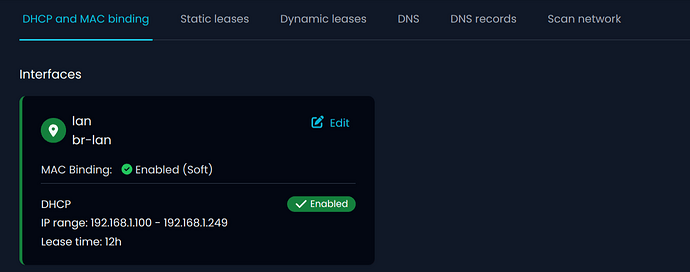
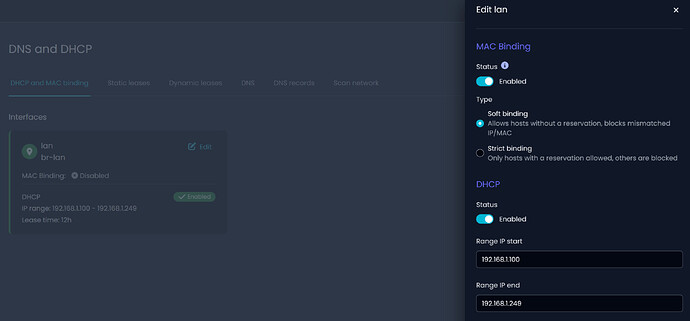
IP/MAC Binding: UI Released
MAC-IP binding is a security feature that allows the firewall to enforce strict control over which devices can communicate on the network.
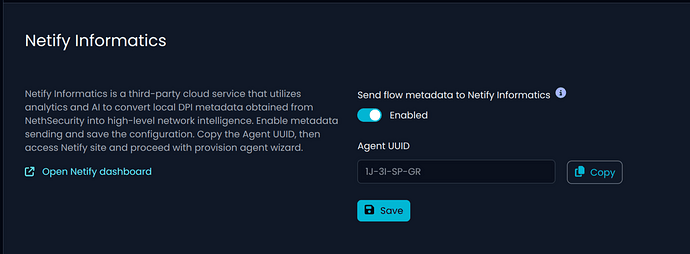
Netify Informatics: UI Released for Service Registration
Netify Informatics is a third-party cloud service that utilizes analytics and AI to convert local DPI metadata obtained from NethSecurity into high-level network intelligence.
 Changes and Improvements
Changes and Improvements
Security
Various modifications have been made to strengthen the system, including:
- API hardening
- SNMP service is now disabled by default
- Backup modifications
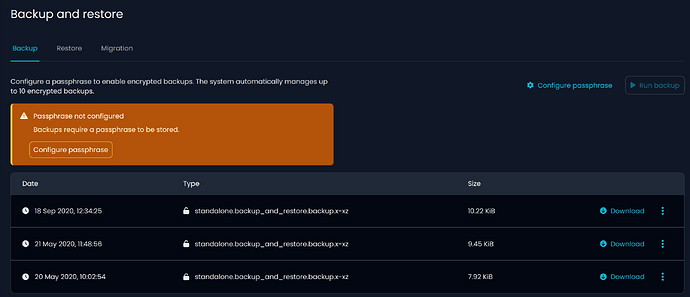
Backup Management Changes (subscription only)
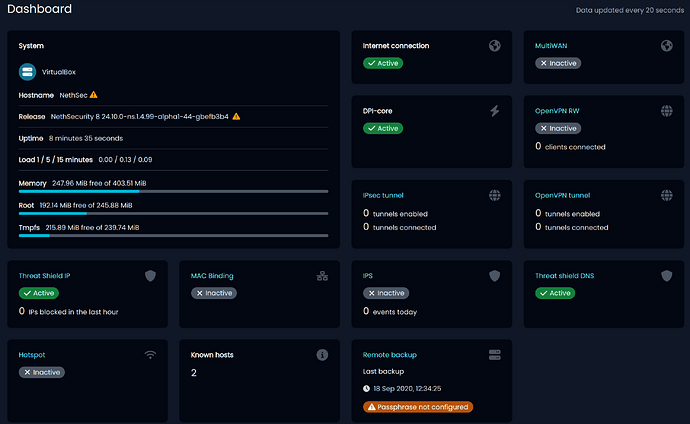
To enhance backup security, an encryption passphrase is now required.
- The dashboard informs users about the passphrase status and prompts for configuration.
- Manual backups cannot be initiated without a configured passphrase.
- To facilitate a smooth transition, automatic backups will continue to be sent to the Nethesis Operation Center even if the passphrase is not configured, until the release of version 8.6. However, we strongly encourage configuring it as soon as possible.
FlashStart DNS: Implementation Improvements (subscription only)
- NethSecurity’s DNS management is now completely separate from the DNS used for FlashStart to avoid any interaction with firewall services.
- External DNS servers are no longer required for unfiltered networks.
New Packages Available in NethSecurity 8 Repositories
Packages for nut (UPS management) and nmap are now available. Installation is optional—follow the documentation.
 Bug Fixes
Bug Fixes
Version 8.5 includes fixes for numerous bugs. Below is a list of the most frequently reported ones, along with a link to the tracker for the complete list and references.
- Migration: OpenVPN device name issue when exceeding 16 characters
- Migration: Loss of configuration for OpenVPN tunnels with similar names
- Migration: Road Warrior client migration interruption if a user certificate is missing
- MultiWAN does not allow the firewall to send traffic outside if the lowest metric route is unavailable
- OpenVPN Tunnel JSON export includes only the first remote endpoint, omitting others
- Enabling logging in firewall rules can overload the CPU
- Netmap rules not loaded after a version update
- OpenVPN server web interface crashes if the user database is removed
- Firewall: “any” zone displayed as inactive
- Port forward: error when assigning an object with an IP range
The full list of fixes is available here:
For those who installed NethSecurity 8.5 Release Candidate
We strongly encourage everyone who installed the RC version to update to the stable release.
 New Network Card Management
New Network Card Management 
NethSecurity 8.5 introduces a different network card ordering method on some specific systems.
NO PANIC! In the vast majority of cases, nothing changes.
So far, differences compared to previous versions have only been observed when SFP slots are present.
Nethesis Hardware
For Nethesis appliances, nothing changes as they are already supported, so the ordering will remain the same even after an update.
What Changes?
Until NethSecurity 8.4, fiber slots were typically enumerated first. For example, on a system with:
- 8 Ethernet cards
- 4 SFP cards
SFPs were recognized as eth0, eth1, eth2, eth3, while Ethernet cards came afterward as eth4, eth5, etc.
With version 8.5, fiber slots are now detected in reverse order, meaning Ethernet cards come first, followed by fiber.
During an upgrade, network card ordering may change—for instance, eth3, which was previously assigned to a fiber slot, might be reassigned to an Ethernet card.
In this case, a manual CLI configuration change would be required to restore the correct order.
Non-Nethesis Hardware
If you usually install NethSecurity on:
- Servers with one or more additional network cards (fiber or Ethernet)
- Multi-port appliances
we strongly recommend preliminary testing in a lab environment.
How to Test Your Devices
- Boot the device using a USB key with NethSecurity 8 and check if the eth assignments match those of the previous version.
- If possible, upgrade from a previous version and verify that eth1, eth2, etc., remain mapped to the same physical ports.
Migration
Migration from 7.9 is unaffected because network cards are remapped based on their MAC address, which does not change.
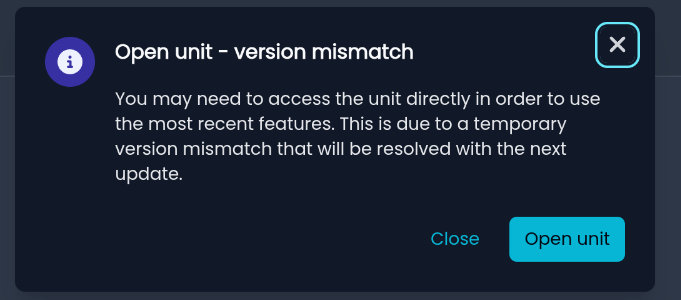
Controller Updates
The update with support for the new version 8.5 has also been released for the controller.
You can either force the controller update or wait for it to install automatically.
Please note that once updated, the controller may display the following message when accessing units running earlier versions:
This does not affect proper functionality, so you can continue to connect and view all firewall sections.
 What is NethSecurity?
What is NethSecurity?
NethSecurity is a powerful, open-source Linux firewall designed to simplify network security deployment. It offers full-featured protection and an easy-to-use interface.
Choose your preferred Subscription Plan
A NethSecurity subscription ensures that your deployment is backed by top-tier technical expertise and the support necessary to maintain your organization’s security infrastructure.
Subscribing also grants exclusive access to the Enterprise repository, which includes Automatic Updates, advanced DPI Applications/protocol detection, and VPN integration with LDAP/AD user databases.
 Get your subscription
Get your subscription
 Help shape NethSecurity’s future
Help shape NethSecurity’s future
Your feedback is invaluable as we continue to refine and enhance NethSecurity. Please share your thoughts, report issues, and suggest features by opening a new topic in the NethSecurity category, using tags like Feature, Bug, or Support.