NethServer Version: 7.4
Module: OpenVPN
As I mentioned in the “what are you working on” thread, I’ve just set up a Neth 7.4 instance on a Contabo VPS. However,
- I don’t like the idea of the server manager being exposed to the whole Internet, and
- I’m going to be wanting to send a good back of data back and forth securely between the Neth VPS and my home network (mostly Neth backups, but other stuff too).
Seems to me that the most straightforward way to do this is to have a more-or-less permanent VPN connection between the Neth instance and my home network. My home network sits behind a pfSense router, which already acts as an OpenVPN server (to allow me to connect to my home network remotely), so it seems the easiest thing for me to do would be to set up the Neth box to connect to that.
So, on pfSense, certificate manager, I created a new user cert for the Neth instance. Went to the OpenVPN client export tool and downloaded that configuration–it contains the CA cert, the user cert, and the user private key.
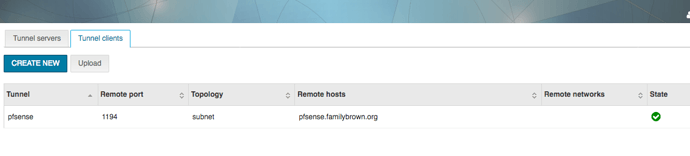
Then, in the server manager, I went to OpenVPN tunnels, tunnel clients, upload, and uploaded the saved config file. The screen gave a red error banner with no further detail. No problem, I thought, and clicked on Create New instead. Filled in a name (pfsense), the FQDN of my router, the port, and in the Certificate field, I pasted both the user cert and the user private key. That saved without issue, and the tunnel clients tab seems to show that it’s connected, but it isn’t:
I expect I’m doing something simple wrong, but what is it?
Edit: The docs, at least as I read them, deal a bit with running Neth as an OpenVPN server, but I don’t see that they deal with the client side, even though the GUI supports that. If this would be easier/simpler to configure with a different type of VPN (e.g., IPSec instead), I could set that up at the router as well, but I’d just as soon stick with what I know (even if I only know a little bit about it).