Hi everyone, I have been using lets’encrypt for 3 years on the nethserver server, never had a problem. The procedure for activating the certificate on the neth server was really simple to complete. The only reminder that I still have to do is that when the certificate expires 30 days before, I am forced to open port 80 with a dnat from the firewall to the nethserver server to allow the exchange and renewal of the certificate. So far everything is ok. I wanted to apply the same procedure on the pfsense firewall then request a lets’encrypt certiifcate. The firewall 192.168.1.2 (wan) receives all traffic from the router 192.168.1.1. During the configuration phase for the certiifcate, there are different methods for validation and I thought I would proceed in the same way as nethserver, that is, I request the certificate, and at the expiration of 30 days, I activate port 80 on the firewall to allow the servers to let 'encrypt to renew. I have posted this procedure on the internet, and to my surprise they tell me that they have never heard of this exchange at port 80. I wonder why with nethserver it was so simple unlike pfsense. Thank you. to anyone who can clarify the correct procedure to apply.
Hi Francesco
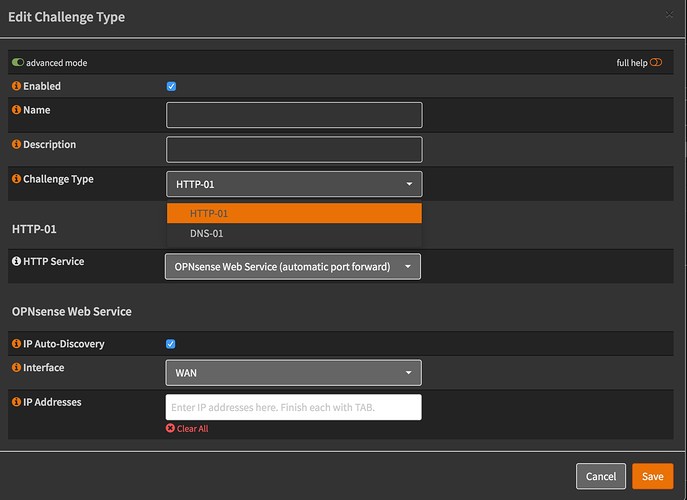
I don’t use PFsense, I use OPNsense, which is a fork of PFsense… The features, and tools used beneath are the same…
OPNsense allows via GUI both http and DNS verification:
The dropdown is down, and on http, but option DNS-01 is visible…
This means you CAN use the same method as on NethServer, as I’m doing at most of my clients…
Onyl difference: I keep Port 80 open! Why should I bother to open / close the port? Anything on Port 80 is essentially available also on Port 443 with SSL…
I would prefer to use DNS verification, but my and most of my clients DNS Registrars/Providers do not support this with an API. 
My servers are well protected, I do not need to worry about script-kiddies!
Why waste time and comfort bothering to open and close a port?
Sometimes I mysel will enter http, knowing my Neth will redirect to https anyway, just being lazy…
And it all works!
See for yourself:
http://intranet.r7.anwi.ch/ is my home connection… It WILL change to https…
My 2 cents
Andy
Thanks andy, I’ve been using this method for 3 years! For the renewal of the certificate I have always set port 80 so it was indicated to me. So from what you say, if the certificate 30 days before expiration, on my server instead of opening the 80 for the exchange and renewal procedure I leave the 443 will it work the same?
LetsEncrypt ONLY checks on http, if using the http challenge. They do NOT check on https!
As said, I’d just leave port 80 open - you have nothing to lose! if whatever is running on NethServer is “hackable”, it’s just as “hackable” using http or https!
…but they will follow a redirect to https. But I’m with you–why close it?
There’s an app for that:
https://wiki.nethserver.org/doku.php?id=userguide:let_s_encrypt_acme-dns
Thanks andy, it’s finally clear. Therefore on pfsense I will try to reproduce the same configuration!
Sorry to get in the mix of this conversation. 
@france something is not clear to me, do you want :
A. Let pfsence request a certificate (which you may copy to Nethserver)
– OR –
B. Let Nethserver request a certificate ?
If it is B you need to forward port 80 to the Nethserver in pfsence too.
Hi
One could use a redirect like this:
But for me it’s simpler if both ports are open, 443 and 80.
I’m aware of this, it’s on my to-do, but as there are a lot of entries, and I want to clean up my infrastructure a bit too, before I tackle the DNS! DNS is too important to tackle on low burner!
My 2 cents
Andy
So Mark, thanks for your intervention. The current scenario which has been in production for 3 years on nethserver and let’s encrypt configured like this: router 192.168.1.1, pfsense 192.168.1.2. The dmz is enabled on the router, all traffic on pfsense. On pfsense a permanent dnat 443 is activated on nethserver, and a dnat active only 30 days before the expiry of the certificate on nethserver port 80. I would like to request a certificate on pfsense and was wondering if I should reproduce the same configuration.