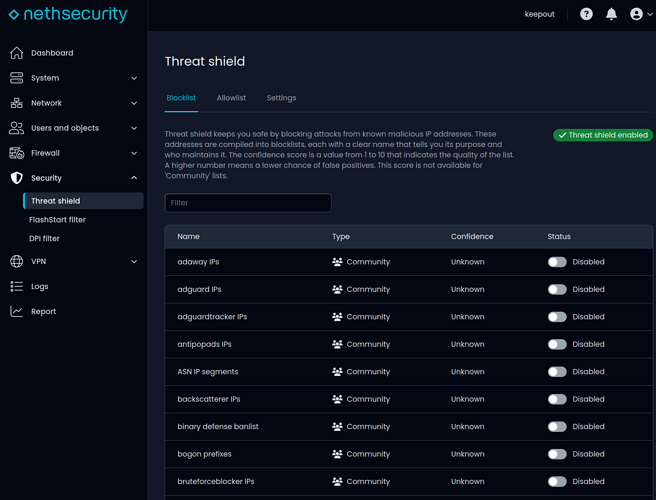
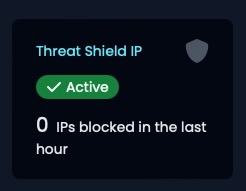
If you follow my steps here and look at the active sources you’ll kinda see why I don’t seem to have any control of TS ip or dns.
root@nsecurity01:~# /etc/init.d/adblock status
::: adblock runtime information
+ adblock_status : enabled
+ adblock_version : 4.1.5
+ blocked_domains : 772056
+ active_sources : malware_lvl2, malware_privacy_lvl2
+ dns_backend : dnsmasq (-), /tmp/dnsmasq.d
+ run_utils : download: /usr/libexec/wget-ssl, sort: /usr/libexec/sort-coreutils, awk: /usr/bin/gawk
+ run_ifaces : trigger: -, report: -
+ run_directories : base: /tmp, backup: /tmp/adblock-Backup, report: /tmp/adblock-Report, jail: /tmp
+ run_flags : backup: ✔, flush: ✘, force: ✔, search: ✘, report: ✘, mail: ✘, jail: ✘
+ last_run : restart, 0m 31s, 2003/1631/1670, 2024-08-16T18:56:41-07:00
+ system : Shuttle Inc SG41, NethSecurity 8-23.05.4-ns.1.2.0 r24012-d8dd03c46f
root@nsecurity01:~# echo '{"blocklist": "malware_privacy_lvl2", "enabled": false}' | /usr/libexec/rpcd/ns.threatshield call dns-edit-blocklist | jq
{
"message": "success"
}
root@nsecurity01:~# uci commit adblock && service adblock restart
root@nsecurity01:~# /etc/init.d/adblock status
::: adblock runtime information
+ adblock_status : running
+ adblock_version : 4.1.5
+ blocked_domains : 0
+ active_sources : adaway, adguard, disconnect, malware_lvl2, yoyo
+ dns_backend : dnsmasq (-), /tmp/dnsmasq.d
+ run_utils : download: /usr/libexec/wget-ssl, sort: /usr/libexec/sort-coreutils, awk: /usr/bin/gawk
+ run_ifaces : trigger: -, report: -
+ run_directories : base: /tmp, backup: /tmp/adblock-Backup, report: /tmp/adblock-Report, jail: /tmp
+ run_flags : backup: ✔, flush: ✘, force: ✔, search: ✘, report: ✘, mail: ✘, jail: ✘
+ last_run : -
+ system : Shuttle Inc SG41, NethSecurity 8-23.05.4-ns.1.2.0 r24012-d8dd03c46f
root@nsecurity01:~# /etc/init.d/adblock status
::: adblock runtime information
+ adblock_status : running
+ adblock_version : 4.1.5
+ blocked_domains : 0
+ active_sources : adaway, adguard, disconnect, malware_lvl2, yoyo
+ dns_backend : dnsmasq (-), /tmp/dnsmasq.d
+ run_utils : download: /usr/libexec/wget-ssl, sort: /usr/libexec/sort-coreutils, awk: /usr/bin/gawk
+ run_ifaces : trigger: -, report: -
+ run_directories : base: /tmp, backup: /tmp/adblock-Backup, report: /tmp/adblock-Report, jail: /tmp
+ run_flags : backup: ✔, flush: ✘, force: ✔, search: ✘, report: ✘, mail: ✘, jail: ✘
+ last_run : -
+ system : Shuttle Inc SG41, NethSecurity 8-23.05.4-ns.1.2.0 r24012-d8dd03c46f
root@nsecurity01:~# /etc/init.d/adblock status
::: adblock runtime information
+ adblock_status : enabled
+ adblock_version : 4.1.5
+ blocked_domains : 733556
+ active_sources : malware_lvl2
+ dns_backend : dnsmasq (-), /tmp/dnsmasq.d
+ run_utils : download: /usr/libexec/wget-ssl, sort: /usr/libexec/sort-coreutils, awk: /usr/bin/gawk
+ run_ifaces : trigger: -, report: -
+ run_directories : base: /tmp, backup: /tmp/adblock-Backup, report: /tmp/adblock-Report, jail: /tmp
+ run_flags : backup: ✔, flush: ✘, force: ✔, search: ✘, report: ✘, mail: ✘, jail: ✘
+ last_run : restart, 0m 55s, 2003/1639/1679, 2024-08-16T20:36:19-07:00
+ system : Shuttle Inc SG41, NethSecurity 8-23.05.4-ns.1.2.0 r24012-d8dd03c46f