Hello,
I’m setting up a NethSecurity VPN server on an AWS EC2 instance and running into issues with firewall behavior after reboot. I’m still learning networking and could use some help understanding what’s happening, and how to configure this securely.
Setup Summary:
NethServer Security: nethsecurity-8-24.10.0-ns.1.5.1
NethSecurity is running on an EC2 instance
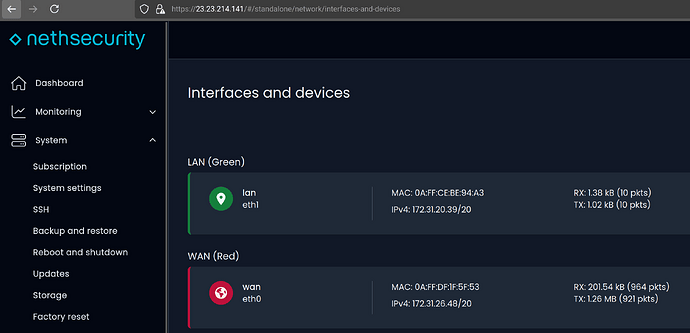
The server has two NICs:
WAN (with Elastic IP/public IP assigned)
LAN
VPN is configured to connect(VPN ip) via the WAN interface
The Issue:
On initial deployment, everything works fine:
I can access the Web UI via the WAN public IP
VPN connection works
However, after a reboot, and without a firewall rule allowing SSH (port 22) from the WAN interface:
- I cannot access the Web UI via WAN public IP
- I cannot SSH, even from the same subnet (via private IP)
- VPN connection fails
Recovery Steps:
To regain access after reboot:
I attach an Elastic IP to the LAN NIC
I can then access the Web UI via LAN’s public IP
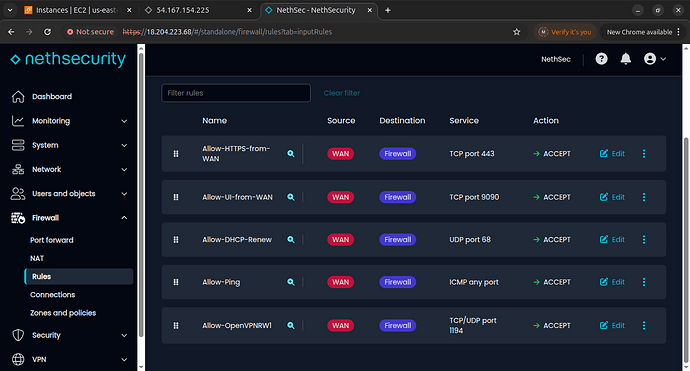
From the Web UI, I manually add a firewall rule to allow SSH (port 22) from any source on the WAN interface
This restores:
Web UI access via WAN
SSH from anywhere via WAN
PN connection via WAN
Additionally:
If I update the VPN server configuration to use the LAN’s public IP as the VPN gateway, VPN connections work again for existing users(also i have to change VPN’s ip as LAN’s ip ).
Clarifications:
The SSH allow rule on WAN is something I add manually from the UI.
The issue starts only after reboot — initial boot works fine even without SSH allowed on WAN.
The fact that I can’t even access via private IP from same subnet is confusing.
My Questions:
What’s the secure and proper way to:
Ensure VPN and Web UI access via WAN
Keep SSH access locked down?
Configuration of firewall with ssh allowed from WAN:
config defaults 'ns_defaults'
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config include 'ns_user_include'
option path '/etc/firewall.user'
option fw4_compatible '1'
config include 'ns_hs_include'
option type 'script'
option path '/opt/icaro/dedalo/dedalo.user'
option fw4_compatible '1'
config zone 'ns_lan'
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone 'ns_wan'
option name 'wan'
list network 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config zone 'ns_e2c5f479'
option name 'rwopenvpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list ns_tag 'automated'
option ns_link 'openvpn/ns_roadwarrior_noremove'
list device 'tunrw1'
config forwarding 'ns_lan2wan'
option src 'lan'
option dest 'wan'
config forwarding 'ns_fe43a03d'
option src 'rwopenvpn'
option dest 'lan'
list ns_tag 'automated'
option ns_link 'openvpn/ns_roadwarrior_noremove'
config forwarding 'ns_b38765cf'
option src 'lan'
option dest 'rwopenvpn'
list ns_tag 'automated'
option ns_link 'openvpn/ns_roadwarrior_noremove'
config forwarding 'ns_f615ac5a'
option src 'rwopenvpn'
option dest 'wan'
list ns_tag 'automated'
option ns_link 'openvpn/ns_roadwarrior_noremove'
config rule 'ns_allow_https'
option name 'Allow-HTTPS-from-WAN'
option proto 'tcp'
option src 'wan'
option dest_port '443'
option target 'ACCEPT'
config rule 'ns_allow_ui'
option name 'Allow-UI-from-WAN'
option proto 'tcp'
option src 'wan'
option dest_port '9090'
option target 'ACCEPT'
config rule 'ns_dhcp_wan'
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule 'ns_ping_wan'
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule 'ns_7776fb80'
option name 'Allow-SSH-from-WAN'
option src 'wan'
option target 'ACCEPT'
option ns_service 'ssh'
list proto 'tcp'
list proto 'udp'
option dest_port '22'
option enabled '1'
option log '0'
config rule 'ns_allow_OpenVPNRW1'
option name 'Allow-OpenVPNRW1'
option ns_service 'custom'
option src 'wan'
option dest_port '1194'
list proto 'tcp'
list proto 'udp'
option target 'ACCEPT'
option enabled '1'
list ns_tag 'automated'
option ns_link 'openvpn/ns_roadwarrior1'
NB: I’m fully aware that this is not a secure or recommended way to run a VPN server — especially exposing SSH to the public WAN. My goal is to understand what I’m missing and how to properly secure this setup while maintaining necessary access.
Would really appreciate any insights or best practices.
Thanks in advance!