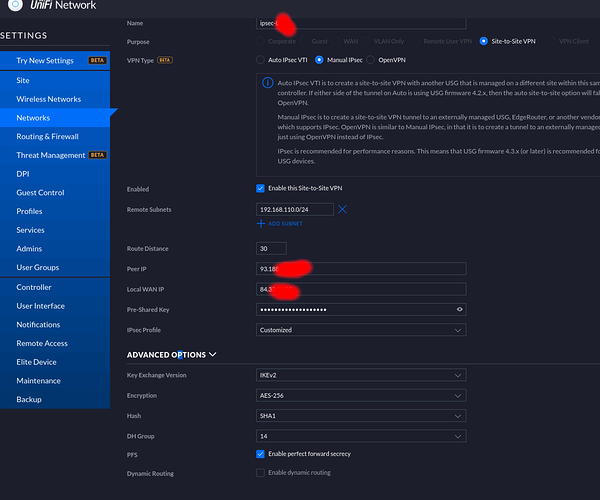
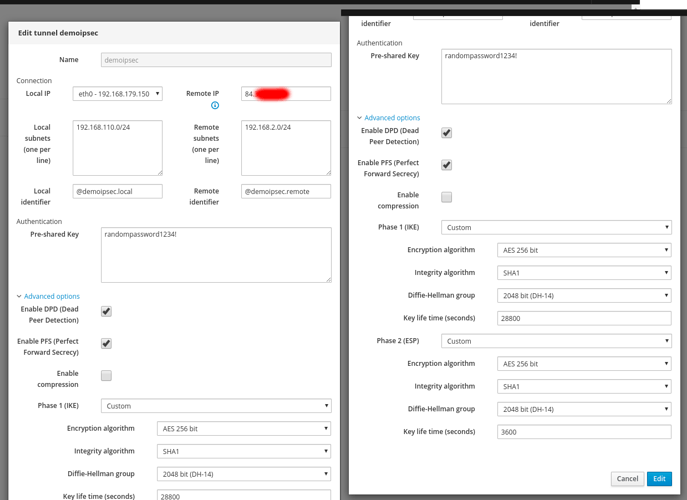
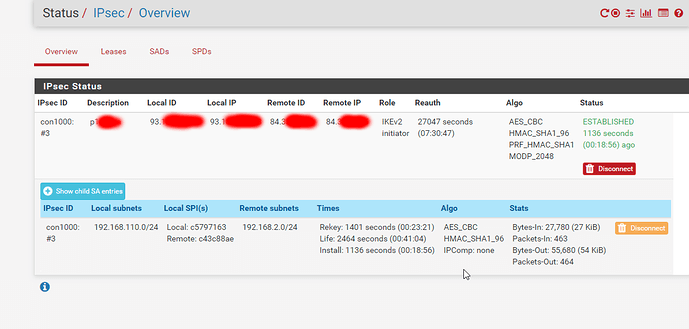
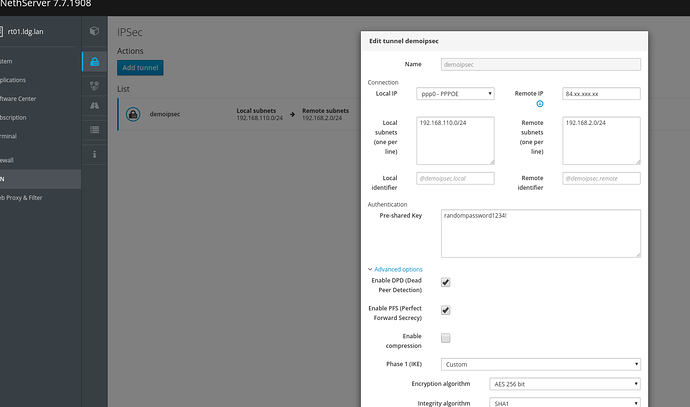
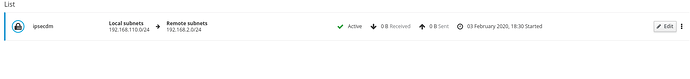
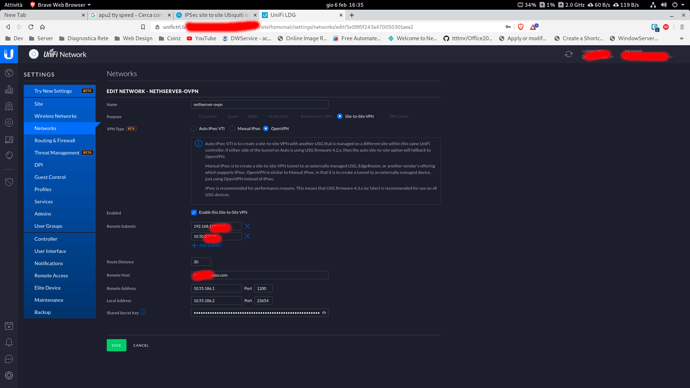
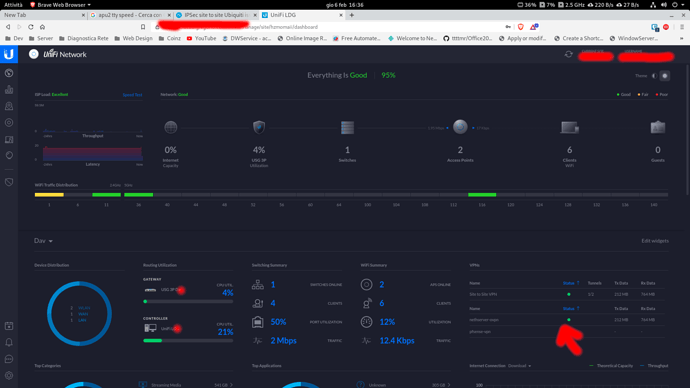
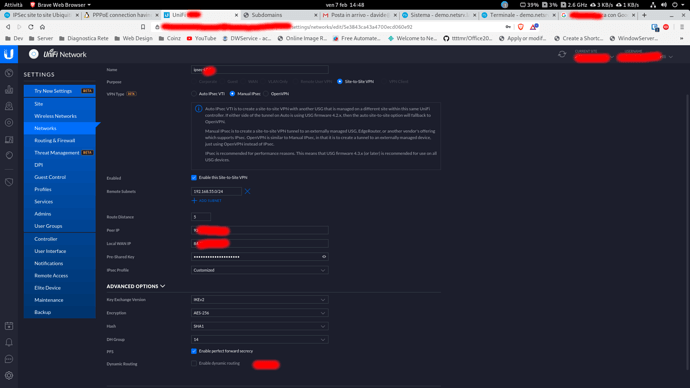
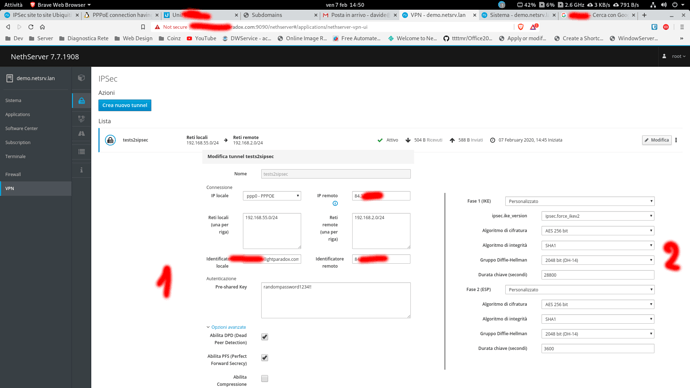
So, i’ve checked the cfg on the ubiquiti :
ipsec.conf ( ubiquiti )
conn peer-93.xxx.xxx.xx-tunnel-vti
left=84.xx.xx.xx
right=93.xxx.xxx.x9
leftsubnet=0.0.0.0/0
rightsubnet=0.0.0.0/0
ike=aes256-sha1-modp2048!
keyexchange=ikev2
reauth=no
ikelifetime=28800s
esp=aes256-sha1-modp2048!
keylife=3600s
rekeymargin=540s
type=tunnel
compress=no
authby=secret
mark=9437185
auto=route
keyingtries=%forever
#conn peer-93.xxx.xxx.x9-tunnel-vti
and i’ve tried to replicate the cfg on NS, using docs from here
btw, it’s the right format, just add Custom_key value ?
[root@rt01 ~]# db vpn setprop ipsecs2s Custom_ike aes256-sha1-modp2048!
[root@rt01 ~]# db vpn setprop ipsecs2s Custom_esp aes256-sha1-modp2048!
[root@rt01 ~]# db vpn setprop ipsecs2s Custom_keyexchange ikev2
[root@rt01 ~]# signal-event nethserver-ipsec-tunnels-save
[root@rt01 ~]# db vpn show ipsecs2s
ipsecs2s=ipsec-tunnel
Custom_esp=aes256-sha1-modp2048!
Custom_ike=aes256-sha1-modp2048!
Custom_keyexchange=ikev2
compress=no
dpdaction=restart
esp=auto
espcipher=aes256
esphash=sha1
esppfsgroup=modp2048
ike=auto
ikecipher=aes256
ikehash=sha1
ikelifetime=28800
ikepfsgroup=modp2048
left=%eth0
leftid=93.xxx.xxx.x9
leftsubnets=192.168.110.0/24
pfs=no
psk=randompassword1234!!randompassword1234!!
right=84.xx.xx.x5
rightid=84.xx.xx.x5
rightsubnets=192.168.2.0/24
salifetime=3600
status=enabled
but ofc, the ipsec process seems to just crash the log just report this:
Feb 4 17:43:36 rt01 pluto[23176]: FIPS Product: NO
Feb 4 17:43:36 rt01 pluto[23176]: FIPS Kernel: NO
Feb 4 17:43:36 rt01 pluto[23176]: FIPS Mode: NO
Feb 4 17:43:36 rt01 pluto[23176]: NSS DB directory: sql:/etc/ipsec.d
Feb 4 17:43:36 rt01 pluto[23176]: Initializing NSS
Feb 4 17:43:36 rt01 pluto[23176]: Opening NSS database "sql:/etc/ipsec.d" read-only
Feb 4 17:43:36 rt01 pluto[23176]: NSS initialized
Feb 4 17:43:36 rt01 pluto[23176]: NSS crypto library initialized
Feb 4 17:43:36 rt01 pluto[23176]: FIPS HMAC integrity support [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: FIPS mode disabled for pluto daemon
Feb 4 17:43:36 rt01 pluto[23176]: FIPS HMAC integrity verification self-test passed
Feb 4 17:43:36 rt01 pluto[23176]: libcap-ng support [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: Linux audit support [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: Linux audit activated
Feb 4 17:43:36 rt01 pluto[23176]: Starting Pluto (Libreswan Version 3.25 XFRM(netkey) KLIPS FORK PTHREAD_SETSCHEDPRIO GCC_EXCEPTIONS NSS (AVA copy) (IPsec profile) DNSSEC SYSTEMD_WATCHDOG FIPS_CHECK LABELED_IPSEC SECCOMP LIBCAP_NG LINUX_AUDIT XAUTH_PAM NETWORKMANAGER CURL(non-NSS) LDAP(non-NSS)) pid:23176
Feb 4 17:43:36 rt01 pluto[23176]: core dump dir: /run/pluto
Feb 4 17:43:36 rt01 pluto[23176]: secrets file: /etc/ipsec.secrets
Feb 4 17:43:36 rt01 pluto[23176]: leak-detective enabled
Feb 4 17:43:36 rt01 pluto[23176]: NSS crypto [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: XAUTH PAM support [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: NAT-Traversal support [enabled]
Feb 4 17:43:36 rt01 pluto[23176]: Initializing libevent in pthreads mode: headers: 2.0.21-stable (2001500); library: 2.0.21-stable (2001500)
Feb 4 17:43:36 rt01 pluto[23176]: Encryption algorithms:
Feb 4 17:43:36 rt01 pluto[23176]: AES_CCM_16 IKEv1: ESP IKEv2: ESP FIPS {256,192,*128} (aes_ccm aes_ccm_c)
Feb 4 17:43:36 rt01 pluto[23176]: AES_CCM_12 IKEv1: ESP IKEv2: ESP FIPS {256,192,*128} (aes_ccm_b)
Feb 4 17:43:36 rt01 pluto[23176]: AES_CCM_8 IKEv1: ESP IKEv2: ESP FIPS {256,192,*128} (aes_ccm_a)
Feb 4 17:43:36 rt01 pluto[23176]: 3DES_CBC IKEv1: IKE ESP IKEv2: IKE ESP FIPS [*192] (3des)
Feb 4 17:43:36 rt01 pluto[23176]: CAMELLIA_CTR IKEv1: ESP IKEv2: ESP {256,192,*128}
Feb 4 17:43:36 rt01 pluto[23176]: CAMELLIA_CBC IKEv1: IKE ESP IKEv2: IKE ESP {256,192,*128} (camellia)
Feb 4 17:43:36 rt01 pluto[23176]: AES_GCM_16 IKEv1: ESP IKEv2: IKE ESP FIPS {256,192,*128} (aes_gcm aes_gcm_c)
Feb 4 17:43:36 rt01 pluto[23176]: AES_GCM_12 IKEv1: ESP IKEv2: IKE ESP FIPS {256,192,*128} (aes_gcm_b)
Feb 4 17:43:36 rt01 pluto[23176]: AES_GCM_8 IKEv1: ESP IKEv2: IKE ESP FIPS {256,192,*128} (aes_gcm_a)
Feb 4 17:43:36 rt01 pluto[23176]: AES_CTR IKEv1: IKE ESP IKEv2: IKE ESP FIPS {256,192,*128} (aesctr)
Feb 4 17:43:36 rt01 pluto[23176]: AES_CBC IKEv1: IKE ESP IKEv2: IKE ESP FIPS {256,192,*128} (aes)
Feb 4 17:43:36 rt01 pluto[23176]: SERPENT_CBC IKEv1: IKE ESP IKEv2: IKE ESP {256,192,*128} (serpent)
Feb 4 17:43:36 rt01 pluto[23176]: TWOFISH_CBC IKEv1: IKE ESP IKEv2: IKE ESP {256,192,*128} (twofish)
Feb 4 17:43:36 rt01 pluto[23176]: TWOFISH_SSH IKEv1: IKE IKEv2: IKE ESP {256,192,*128} (twofish_cbc_ssh)
Feb 4 17:43:36 rt01 pluto[23176]: CAST_CBC IKEv1: ESP IKEv2: ESP {*128} (cast)
Feb 4 17:43:36 rt01 pluto[23176]: NULL_AUTH_AES_GMAC IKEv1: ESP IKEv2: ESP {256,192,*128} (aes_gmac)
Feb 4 17:43:36 rt01 pluto[23176]: NULL IKEv1: ESP IKEv2: ESP []
Feb 4 17:43:36 rt01 pluto[23176]: Hash algorithms:
Feb 4 17:43:36 rt01 pluto[23176]: MD5 IKEv1: IKE IKEv2:
Feb 4 17:43:36 rt01 pluto[23176]: SHA1 IKEv1: IKE IKEv2: FIPS (sha)
Feb 4 17:43:36 rt01 pluto[23176]: SHA2_256 IKEv1: IKE IKEv2: FIPS (sha2 sha256)
Feb 4 17:43:36 rt01 pluto[23176]: SHA2_384 IKEv1: IKE IKEv2: FIPS (sha384)
Feb 4 17:43:36 rt01 pluto[23176]: SHA2_512 IKEv1: IKE IKEv2: FIPS (sha512)
Feb 4 17:43:36 rt01 pluto[23176]: PRF algorithms:
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_MD5 IKEv1: IKE IKEv2: IKE (md5)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA1 IKEv1: IKE IKEv2: IKE FIPS (sha sha1)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_256 IKEv1: IKE IKEv2: IKE FIPS (sha2 sha256 sha2_256)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_384 IKEv1: IKE IKEv2: IKE FIPS (sha384 sha2_384)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_512 IKEv1: IKE IKEv2: IKE FIPS (sha512 sha2_512)
Feb 4 17:43:36 rt01 pluto[23176]: AES_XCBC IKEv1: IKEv2: IKE FIPS (aes128_xcbc)
Feb 4 17:43:36 rt01 pluto[23176]: Integrity algorithms:
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_MD5_96 IKEv1: IKE ESP AH IKEv2: IKE ESP AH (md5 hmac_md5)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA1_96 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (sha sha1 sha1_96 hmac_sha1)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_512_256 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (sha512 sha2_512 hmac_sha2_512)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_384_192 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (sha384 sha2_384 hmac_sha2_384)
Feb 4 17:43:36 rt01 pluto[23176]: HMAC_SHA2_256_128 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (sha2 sha256 sha2_256 hmac_sha2_256)
Feb 4 17:43:36 rt01 pluto[23176]: AES_XCBC_96 IKEv1: ESP AH IKEv2: IKE ESP AH FIPS (aes_xcbc aes128_xcbc aes128_xcbc_96)
Feb 4 17:43:36 rt01 pluto[23176]: AES_CMAC_96 IKEv1: ESP AH IKEv2: ESP AH FIPS (aes_cmac)
Feb 4 17:43:36 rt01 pluto[23176]: NONE IKEv1: ESP IKEv2: ESP FIPS (null)
Feb 4 17:43:36 rt01 pluto[23176]: DH algorithms:
Feb 4 17:43:36 rt01 pluto[23176]: NONE IKEv1: IKEv2: IKE ESP AH (null dh0)
Feb 4 17:43:36 rt01 pluto[23176]: MODP1024 IKEv1: IKE ESP AH IKEv2: IKE ESP AH (dh2)
Feb 4 17:43:36 rt01 pluto[23176]: MODP1536 IKEv1: IKE ESP AH IKEv2: IKE ESP AH (dh5)
Feb 4 17:43:36 rt01 pluto[23176]: MODP2048 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (dh14)
Feb 4 17:43:36 rt01 pluto[23176]: MODP3072 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (dh15)
Feb 4 17:43:36 rt01 pluto[23176]: MODP4096 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (dh16)
Feb 4 17:43:36 rt01 pluto[23176]: MODP6144 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (dh17)
Feb 4 17:43:36 rt01 pluto[23176]: MODP8192 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS (dh18)
Feb 4 17:43:36 rt01 pluto[23176]: DH19 IKEv1: IKE IKEv2: IKE ESP AH FIPS (ecp_256)
Feb 4 17:43:36 rt01 pluto[23176]: DH20 IKEv1: IKE IKEv2: IKE ESP AH FIPS (ecp_384)
Feb 4 17:43:36 rt01 pluto[23176]: DH21 IKEv1: IKE IKEv2: IKE ESP AH FIPS (ecp_521)
Feb 4 17:43:36 rt01 pluto[23176]: DH22 IKEv1: IKE ESP AH IKEv2: IKE ESP AH
Feb 4 17:43:36 rt01 pluto[23176]: DH23 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS
Feb 4 17:43:36 rt01 pluto[23176]: DH24 IKEv1: IKE ESP AH IKEv2: IKE ESP AH FIPS
Feb 4 17:43:36 rt01 pluto[23176]: starting up 5 crypto helpers
Feb 4 17:43:36 rt01 pluto[23176]: started thread for crypto helper 0
Feb 4 17:43:36 rt01 pluto[23176]: started thread for crypto helper 1
Feb 4 17:43:36 rt01 pluto[23176]: started thread for crypto helper 2
Feb 4 17:43:36 rt01 pluto[23176]: started thread for crypto helper 3
Feb 4 17:43:36 rt01 pluto[23176]: started thread for crypto helper 4
Feb 4 17:43:36 rt01 pluto[23176]: Using Linux XFRM/NETKEY IPsec interface code on 3.10.0-1062.9.1.el7.x86_64
Feb 4 17:43:36 rt01 pluto[23176]: | selinux support is NOT enabled.
Feb 4 17:43:36 rt01 pluto[23176]: systemd watchdog for ipsec service configured with timeout of 200000000 usecs
Feb 4 17:43:36 rt01 pluto[23176]: watchdog: sending probes every 100 secs
Feb 4 17:43:36 rt01 pluto[23176]: listening for IKE messages
Feb 4 17:43:36 rt01 pluto[23176]: adding interface tunrw/tunrw 10.123.22.1:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface tunrw/tunrw 10.123.22.1:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface tuns2s-dl/tuns2s-dl 10.55.186.1:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface tuns2s-dl/tuns2s-dl 10.55.186.1:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth1.50/eth1.50 10.50.0.1:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth1.50/eth1.50 10.50.0.1:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth1/eth1 192.168.110.1:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth1/eth1 192.168.110.1:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth0/eth0 192.168.179.150:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface eth0/eth0 192.168.179.150:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface lo/lo 127.0.0.1:500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface lo/lo 127.0.0.1:4500
Feb 4 17:43:36 rt01 pluto[23176]: adding interface lo/lo ::1:500
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface lo:500 fd 27
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface lo:4500 fd 26
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface lo:500 fd 25
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth0:4500 fd 24
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth0:500 fd 23
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth1:4500 fd 22
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth1:500 fd 21
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth1.50:4500 fd 20
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface eth1.50:500 fd 19
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface tuns2s-dl:4500 fd 18
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface tuns2s-dl:500 fd 17
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface tunrw:4500 fd 16
Feb 4 17:43:36 rt01 pluto[23176]: | setup callback for interface tunrw:500 fd 15
Feb 4 17:43:36 rt01 pluto[23176]: loading secrets from "/etc/ipsec.secrets"
Feb 4 17:43:36 rt01 pluto[23176]: loading secrets from "/etc/ipsec.d/tunnels.secrets"
Feb 4 17:43:40 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:43:40 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/ipsec/read
Feb 4 17:43:40 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:43:41 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:44:41 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/ipsec/update
Feb 4 17:44:41 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:44:42 rt01 pluto[23176]: shutting down
Feb 4 17:44:42 rt01 pluto[23176]: forgetting secrets
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface lo/lo ::1:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface lo/lo 127.0.0.1:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface lo/lo 127.0.0.1:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth0/eth0 192.168.179.150:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth0/eth0 192.168.179.150:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth1/eth1 192.168.110.1:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth1/eth1 192.168.110.1:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth1.50/eth1.50 10.50.0.1:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface eth1.50/eth1.50 10.50.0.1:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface tuns2s-dl/tuns2s-dl 10.55.186.1:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface tuns2s-dl/tuns2s-dl 10.55.186.1:500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface tunrw/tunrw 10.123.22.1:4500
Feb 4 17:44:42 rt01 pluto[23176]: shutting down interface tunrw/tunrw 10.123.22.1:500
Feb 4 17:44:42 rt01 pluto[23176]: leak detective found no leaks
Feb 4 17:44:46 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:44:46 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/ipsec/read
Feb 4 17:44:46 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:44:46 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:48:18 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:23 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/logs/read
Feb 4 17:51:23 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:24 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:24 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:51:24 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:24 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:25 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:51:25 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:25 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:54 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/dashboard/read
Feb 4 17:51:54 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:55 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:55 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/dashboard/read
Feb 4 17:51:55 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/dashboard/read
Feb 4 17:51:55 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:55 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:51:55 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:51:55 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:00 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/dashboard/read
Feb 4 17:52:00 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:00 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/dashboard/read
Feb 4 17:52:00 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:00 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:00 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:00 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/nethserver-vpn-ui/logs/read
Feb 4 17:52:00 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:01 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:01 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:52:01 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:01 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:01 rt01 polkitd[985]: Registered Authentication Agent for unix-process:30715:1738378 (system bus name :1.2282 [/usr/bin/pkttyagent --notify-fd 5 --fallback], object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_US.utf8)
Feb 4 17:52:01 rt01 polkitd[985]: Unregistered Authentication Agent for unix-process:30715:1738378 (system bus name :1.2282, object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_US.utf8) (disconnected from bus)
Feb 4 17:52:03 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:52:03 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:03 rt01 sudo: pam_unix(sudo:session): session closed for user root
Feb 4 17:52:05 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:52:05 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:09 rt01 sudo: root : TTY=unknown ; PWD=/run/user/0 ; USER=root ; COMMAND=/usr/libexec/nethserver/api/system-logs/execute
Feb 4 17:52:09 rt01 sudo: pam_unix(sudo:session): session opened for user root by root(uid=0)
Feb 4 17:52:09 rt01 sudo: pam_unix(sudo:session): session closed for user root
I’m totally lost… anyone has some ideas ?