NethServer Version: 7.9.2009
Module: Services
New to NethServer, I’m using it specifically as an active directory domain controller, not a firewall or router. As such, it’s only connected to the “green” network, which is a network I use specifically for servers. My active directory clients are on two other subnets, which are controlled by a separate firewall.
I added the client subnets to the “Trusted Networks” in NethServer, but I didn’t see any way to include these networks for “Access” to services such as dnsmasq. I ended up having to enable access to dnsmasq from both red and green networks, which works, but seems a bit clumsy. It seems silly to me that NethServer would assume that you would want your domain controller on the same subnet as your clients, but it seems like if it’s not “green” then it doesn’t exist. Am I missing something?
Hi Dan
And welcome to the Nethserver community!
If another router / firewall is handling routing (Like I use for my clients) AND you have a seperate subnet for clients (Set on that “other” router), then there’s no way NethServer can “know” about that network, unless you set stuff like “Trusted Networks”.
In a typical SME environment, there are usually No subnets for clients, clients and servers are usually in the same subnet. And larger environments are not really the scope of NethServer, which is dedicated to SME environments.
With 35+ years in the business, and operating in SME and in enterprise classs environments, I tend to agree. If less than 20 clients, additional subnets for clients are overkill. Sure, some specialized “service” companies may need more, but then the know-how is usually available to handle these. A typical SME will not have a dedicated IT department, and usually the know how level is lower than in an enterprise environment, where such departments are available.
My typical environment for my clients:
- All servers virtualized under Proxmox.
- Backup to NAS, additionally most clients use PBS for Proxmox Backups.
- Backups (including PBS) are also available Offsite
- Routing / Firewalling is done by a dedicated OPNsense box (not virtualized).
- NethServer provides: AD, File, Print, Mail, Nextcloud, Zabbix Monitoring (and more, sometimes…)
- Additional servers, eg ERP systems, are usually “Member Servers” in NethServers AD.
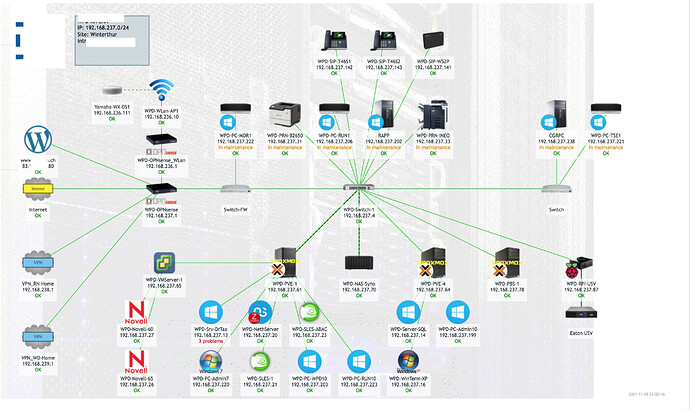
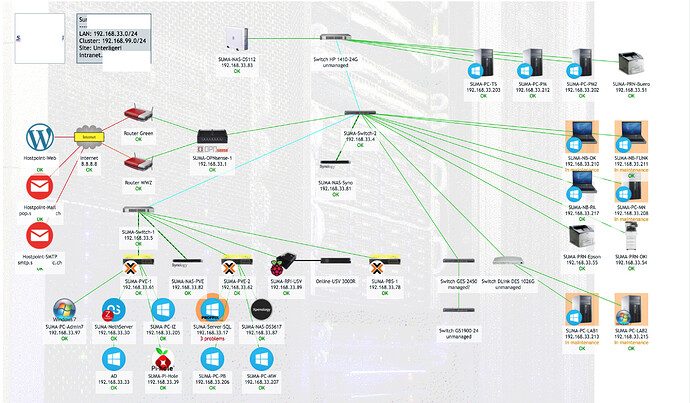
Some examples of actual clients:
Another last tip:
Please avoid using stupid, outdated concepts like using .local or .lan as your local domain. Even Microsoft, which did suggest such stupid stuff before 2000(!) has for at least 10 years now suggested using a subdomain of a “real” DNS Internet Domain.
The big advantage: Using a LetsEncrypt “valid” certificate for your AD becomes really easy!
And this makes using certain JAVA or PHP apps with AD authentification easy.
If you have further questions, don’t hesitate to ask here, our motto here is:
The only stupid questions are the ones not asked…

My 2 cents
Andy
1 Like
Thanks for the insights Andy. I chose to use separate subnets not because of the number of clients but simply for security purposes so I could control traffic between groups of users with the firewall (OPNsense). I’m generally ok with using NethServer with both red and green “open” since it’s not doing any actual routing, but now I’m curious: will the AD service accept domain joins from clients outside of NethServer’s green network?
Hi Dan
AFAIK, it should work with Win10, but the clients DNS must point to the NethServer (Either via DHCP or via hand) and Trusted Networks must be enabled.
If you’re using the OPNsense for routing, there’s actually no need for using a red and a green LAN on NethServer. That makes things a mite more difficult to get things to work in a multi LAN environment.
Any specific reason for this (Using red and green on NethServer despite having a seperate router)…?
My 2 cents
Andy
I am using NethServer for DNS and OPNsense for DHCP, so that should check out just fine.
To be clear: the NethServer machine only has one ethernet interface, which is on the green network, 192.168.4.0/24. I’ve added 192.168.1.0/24 as a Trusted Network, which is where my clients reside. However, while tested late last night I forgot that I was testing from a client on the VPN network, 10.0.0.0/24, which was not a trusted network. I just added the VPN subnet to the Trusted Networks and configured dnsmasq to only work on the green network, and it works - I can dig from my VPN client machine to the NethServer address.
tl;dr: don’t forget that VPN client’s aren’t actually on the client network 
2 Likes