NethServer Version: 7.9.2009
Module: EMail
Good day,
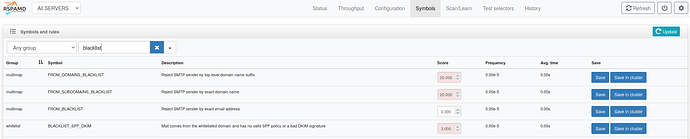
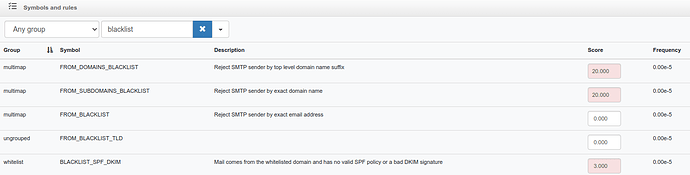
Thanks to the TLD level blocking I have managed to block a lot of malicious mail.
But I have an annoyance with the emails coming from amazon, of which some are valid and acceptable, except this example (and it is not the only one).
I have already tried to filter (Deny from) the whole address or just the shopology domain; although the mail comes in and is sent to spam, I would like to block this annoying sender completely.
Thanks in advance
Enrique
Return-Path: <01000183b33d9fa8-208679ee-af83-476d-810a-d34262a678d3-000000@amazonses.com>
Delivered-To: myuser@mydomain.com
Received: from mail.mydomain.com
by mail.mydomain.com with LMTP id 8MADAFJRQGOpUwAAoNHYhA
for <myuser@mydomain.com>; Fri, 07 Oct 2022 10:18:26 -0600
Received: from a48-94.smtp-out.amazonses.com (gateway [10.20.30.40])
by mail.mydomain.com (Postfix) with ESMTPS id 241DEE101D
for <email@mydomain.com>; Fri, 7 Oct 2022 10:18:25 -0600 (MDT)
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple;
s=2nqc2bjzivauveqgxqhyccbufufddfm3; d=shopology.com.mx;
t=1665159504;
h=Content-Type:MIME-Version:Message-Id:From:Subject:Reply-To:To:Date;
bh=qyKi4vG0TnGZ7Yqhmhm0RQ+hHz+uojhuebGonbSVVCo=;
b=WimombtyLf5mkagV7xgIzPzdy0XRZ7Q+X7PWnZsrnQ/0BuNSrYmmmsAcc5aKlAmR
a5mG2m8RhYr4yfPgpaENaOukTHtR2wNf54Twh46i7bKv2yAE5jWFZlRDQvLlIhaAil6
UJh2g4fGhzG51HS2JSkP7JBrFpGFDxZ8c7hNR2Q4=
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple;
s=6gbrjpgwjskckoa6a5zn6fwqkn67xbtw; d=amazonses.com; t=1665159504;
h=Content-Type:MIME-Version:Message-Id:From:Subject:Reply-To:To:Date:Feedback-ID;
bh=qyKi4vG0TnGZ7Yqhmhm0RQ+hHz+uojhuebGonbSVVCo=;
b=Xmqe0V5KtSjor2YVto/CFZZry0hHn+hTi2mK1inFXBLi8bXcxV1gk/mNHWAFsdfJ
Qoui7OtMl6a580h1Orgr64CX/flLzcLJJxGUJnT+RdPK2M51v/+tIUOpyf8/VeNtilH
/EIFpP0gDFgPQ8olMMTsJQhxO/3OhfdGdDzbJxUk=
Content-Type: multipart/mixed; boundary="===============5162931314022000922=="
MIME-Version: 1.0
Message-ID: <01000183b33d9fa8-208679ee-af83-476d-810a-d34262a678d3-000000@email.amazonses.com>
From: Annoying Sender <annoying.sender@shopology.com.mx>
Subject: =?UTF-8?Q?=7E_=E2=80=9CSe_ten=C3=ADa_que_dec?= =?UTF-8?Q?ir_y_se_dijo=E2=80=9D?=
Reply-To: Annoying Sender <annoying.sender@shopology.com.mx>
To: email@mydomain.com
Date: Fri, 7 Oct 2022 16:18:23 +0000
X-Odoo-Objects: mailing.contact-36871
Feedback-ID: 1.us-east-1.H1+7jaezTqdOsnvexYius9/W988VH1g7Oz4xpj84c9w=:AmazonSES
X-SES-Outgoing: 2022.10.07-54.240.48.94
X-Spamd-Result: default: False [8.65 / 13.00];
BAYES_SPAM(5.10)[100.00%];
VIOLATED_DIRECT_SPF(3.50)[];
R_SPF_FAIL(1.00)[-all];
CTYPE_MIXED_BOGUS(1.00)[];
DKIM_REPUTATION(-0.90)[-0.89941541696509];
DMARC_POLICY_ALLOW_WITH_FAILURES(-0.50)[];
FORGED_SENDER(0.30)[annoying.sender@shopology.com.mx,01000183b33d9fa8-208679ee-af83-476d-810a-d34262a678d3-000000@amazonses.com];
GENERIC_REPUTATION(-0.29)[-0.29021572412895];
R_DKIM_ALLOW(-0.29)[shopology.com.mx:s=2nqc2bjzivauveqgxqhyccbufufddfm3,amazonses.com:s=6gbrjpgwjskckoa6a5zn6fwqkn67xbtw];
IP_REPUTATION_HAM(-0.27)[ip: 10.20.30.40(-0.27)];
MIME_GOOD(-0.10)[multipart/mixed,multipart/alternative,text/plain];
MIME_BASE64_TEXT(0.10)[];
MX_GOOD(-0.01)[];
REPLYTO_EQ_FROM(0.00)[];
TO_MATCH_ENVRCPT_ALL(0.00)[];
FROM_HAS_DN(0.00)[];
RCPT_COUNT_ONE(0.00)[1];
HAS_REPLYTO(0.00)[annoying.sender@shopology.com.mx];
FROM_NEQ_ENVFROM(0.00)[annoying.sender@shopology.com.mx,01000183b33d9fa8-208679ee-af83-476d-810a-d34262a678d3-000000@amazonses.com];
DKIM_TRACE(0.00)[shopology.com.mx:+,amazonses.com:+];
TO_DN_NONE(0.00)[];
DWL_DNSWL_NONE(0.00)[amazonses.com:dkim];
DMARC_POLICY_ALLOW(0.00)[shopology.com.mx,none];
MIME_TRACE(0.00)[0:+,1:+,2:+,3:~];
RCVD_COUNT_ZERO(0.00)[0];
NEURAL_HAM(-0.00)[-0.991]
X-Spam-Flag: Yes
X-Rspamd-Queue-Id: 241DEE101D