Not having much knowledge about internet security feeling a bit shaky if my homebrew evebox for arm works.
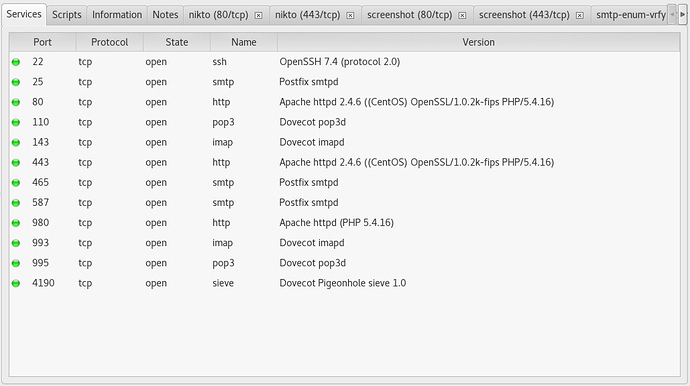
So started to find out how you could test and ids and could not find a lot I understand. The only tool found so far that makes to me besides NMAP is SPARTA.
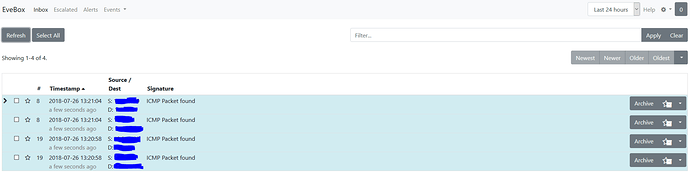
Started test trails on x86_64 without success. The ids is activated and all rules are set to alert accept scan its set to block. The red interface is not connected to the internet, it gets it’s IP (10.0.1.xxx) from the internet router.
#config getprop suricata AlertCategories
ET-botcc.portgrouped,ET-botcc,ET-ciarmy,ET-compromised,ET-drop,ET-dshield,ET-emerging-activex,ET-emerging-attack_response,ET-emerging-chat,ET-emerging-current_events,ET-emerging-deleted,ET-emerging-dns,ET-emerging-dos,ET-emerging-exploit,ET-emerging-ftp,ET-emerging-games,ET-emerging-inappropriate,ET-emerging-info,ET-emerging-malware,ET-emerging-misc,ET-emerging-mobile_malware,ET-emerging-netbios,ET-emerging-p2p,ET-emerging-policy,ET-emerging-scada,ET-emerging-shellcode,ET-emerging-smtp,ET-emerging-snmp,ET-emerging-sql,ET-emerging-telnet,ET-emerging-tftp,ET-emerging-trojan,ET-emerging-user_agents,ET-emerging-voip,ET-emerging-web_client,ET-emerging-web_server,ET-emerging-web_specific_apps,ET-emerging-worm,ET-tor
#
# config getprop suricata BlockCategories
ET-emerging-scan
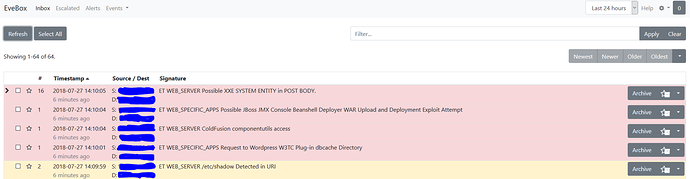
If the red interface is scanned ( nmap, nikto) nothing shows up in evebox nor in /var/log/suricata/fast.log.
What is my wrong thinking?
How can to conduct some tests?
Thanx Mark