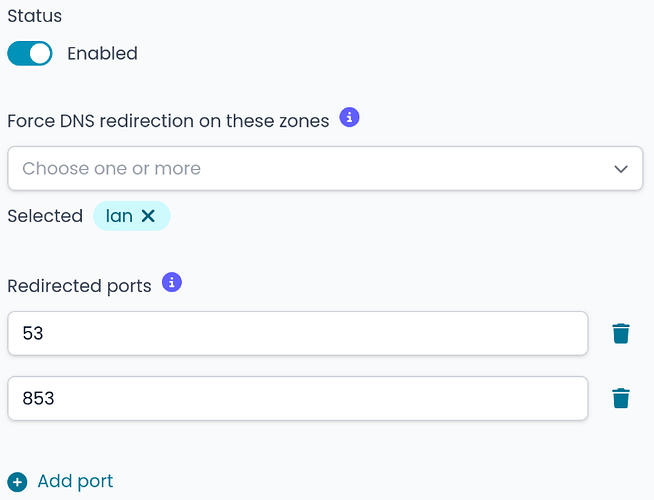
I thought that enabling force DNS redirection on the LAN zone would redirect the traffic from LAN to WAN for the ports 53 and 853 to the Threat shield DNS.
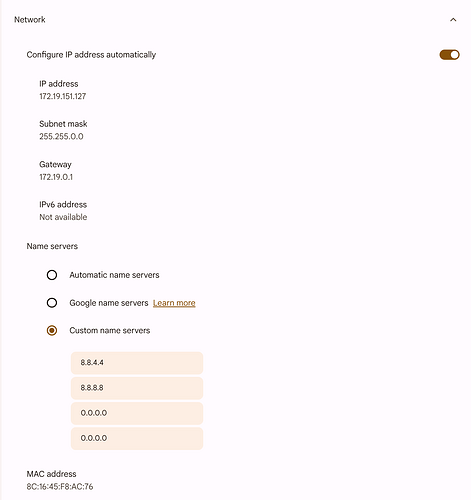
But setting a custom name server in the OS settings allows one to bypass the Threat shield DNS server.
ChromeOS for example:
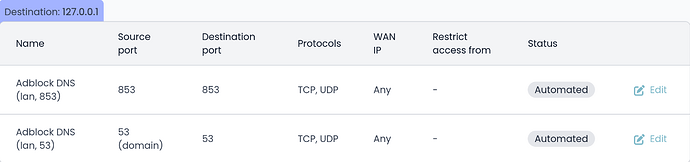
Afterward, the automatically generated port forward rules on Nethsecurity don’t seem to redirect DNS requests, and clients are not restricted by the Threat shield DNS.
Is this the expected behavior?
How should I debug this Issue? Thank you in advance.
I’m using a clean install with Threat shield DNS enabled, nothing else.
config defaults 'ns_defaults'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config include 'ns_user_include'
option path '/etc/firewall.user'
option fw4_compatible '1'
config include 'ns_hs_include'
option type 'script'
option path '/opt/icaro/dedalo/dedalo.user'
option fw4_compatible '1'
config redirect 'adblock_lan853'
option name 'Adblock DNS (lan, 853)'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
option family 'any'
option ipset '!tsdns_bypass'
list ns_tag 'automated'
config ipset 'tsdns_bypass'
option name 'tsdns_bypass'
option match 'src_net'
option enabled '1'
config zone 'ns_lan'
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone 'ns_wan'
option name 'wan'
list network 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding 'ns_lan2wan'
option src 'lan'
option dest 'wan'
config rule 'ns_ping_wan'
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule 'ns_allow_ui'
option name 'Allow-UI-from-WAN'
option src 'wan'
option dest_port '9090'
option target 'ACCEPT'
option ns_service 'custom'
list proto 'tcp'
option enabled '1'
option log '0'
config redirect 'adblock_lan53'
option name 'Adblock DNS (lan, 53)'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
option family 'any'
option ipset '!tsdns_bypass'
list ns_tag 'automated'