Finally, I would like to block internet use overnight for the children.
I wanted to approach the solution step by step and in the first step I wanted to prevent a client from using the internet (in my thinking traffic to RED or from RED???).
In a next step I would try to plan this time controlled. In a further step maybe more specific like “block everything but iTunes music”. So I wanted to get a solution step by step on the one hand and on the other hand I wanted to improve my understanding of the technique step by step.
you can try to use ndpi
Yes, I have installed nDPI. The docs says:
When the DPI module is active, new items for the Service field are available in the Edit rule form. Those items are labeled DPI protocol , among the usual network service and service object items.
But I don’t find any specific labeled services “DPI-Service” to address a rule.
In my understand should this rule…
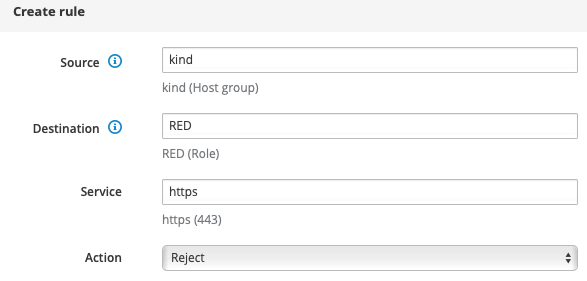
…block all traffic based on https-protocol for the clients inside the host group “kind”.
If not, what then is the deeper meaning behind such service-oriented roles?
inside the NtopNG Documentation I found a list ob nDPI-Protocols:
Zusammenfassung
We are continuously extending nDPI and so far many protocols are supported including
-
- FTP_CONTROL
- POP3
- SMTP
- IMAP
- DNS
- IPP
- HTTP
- MDNS
- NTP
- NetBIOS
- NFS
- SSDP
- BGP
- SNMP
- XDMCP
- SMBv1
- Syslog
- DHCP
- PostgreSQL
- MySQL
- Hotmail
- Direct_Download_Link
- POPS
- AppleJuice
- DirectConnect
- ntop
- COAP
- VMware
- SMTPS
- FacebookZero
- UBNTAC2
- Kontiki
- OpenFT
- FastTrack
- Gnutella
- eDonkey
- BitTorrent
- SkypeCall
- Signal
- Memcached
- SMBv23
- Mining
- NestLogSink
- Modbus
- Xbox
- TikTok
- RTSP
- IMAPS
- IceCast
- PPLive
- PPStream
- Zattoo
- ShoutCast
- Sopcast
- Tvants
- TVUplayer
- HTTP_Download
- QQLive
- Thunder
- Soulseek
- SSL_No_Cert
- IRC
- Ayiya
- Unencrypted_Jabber
- MSN
- Oscar
- Yahoo
- BattleField
- GooglePlus
- VRRP
- Steam
- HalfLife2
- WorldOfWarcraft
- Telnet
- STUN
- IPsec
- GRE
- ICMP
- IGMP
- EGP
- SCTP
- OSPF
- IP_in_IP
- RTP
- RDP
- VNC
- PcAnywhere
- SSL
- SSH
- Usenet
- MGCP
- IAX
- TFTP
- AFP
- Stealthnet
- Aimini
- SIP
- TruPhone
- ICMPV6
- DHCPV6
- Armagetron
- Crossfire
- Dofus
- Fiesta
- Florensia
- Guildwars
- HTTP_ActiveSync
- Kerberos
- LDAP
- MapleStory
- MsSQL-TDS
- PPTP
- Warcraft3
- WorldOfKungFu
- Slack
- Dropbox
- GMail
- GoogleMaps
- YouTube
- Skype
- DCE_RPC
- NetFlow
- sFlow
- HTTP_Connect
- HTTP_Proxy
- Citrix
- NetFlix
- LastFM
- Waze
- YouTubeUpload
- GenericProtocol
- CHECKMK
- AJP
- Apple
- Webex
- AppleiCloud
- Viber
- AppleiTunes
- Radius
- WindowsUpdate
- TeamViewer
- Tuenti
- LotusNotes
- SAP
- GTP
- UPnP
- LLMNR
- RemoteScan
- Spotify
- Messenger
- H323
- OpenVPN
- NOE
- CiscoVPN
- TeamSpeak
- Tor
- CiscoSkinny
- RTCP
- RSYNC
- Oracle
- Corba
- UbuntuONE
- Whois-DAS
- Collectd
- SOCKS
- Nintendo
- RTMP
- FTP_DATA
- Wikipedia
- ZeroMQ
- Amazon
- eBay
- CNN
- Megaco
- Redis
- Pando_Media_Booster
- VHUA
- Telegram
- Vevo
- Pandora
- QUIC
- WhatsAppVoice
- EAQ
- Ookla
- AMQP
- KakaoTalk
- KakaoTalk_Voice
- Twitch
- MPEG_TS
- Snapchat
- Sina(Weibo)
- GoogleHangout
- IFLIX
- Github
- BJNP
- SMPP
- DNScrypt
- TINC
- Deezer
- Microsoft
- Starcraft
- Teredo
- HotspotShield
- HEP
- GoogleDrive
- OCS
- Office365
- Cloudflare
- MS_OneDrive
- MQTT
- RX
- AppleStore
- OpenDNS
- Git
- DRDA
- PlayStore
- SOMEIP
- FIX
- Playstation
- Pastebin
- SoundCloud
- CSGO
- LISP
- Diameter
- ApplePush
- GoogleServices
- AmazonVideo
- GoogleDocs
- WhatsAppFiles
Which could I select? If I analyse the traffic from the targeted hosts, the most is TLS.
Shouldt block this rule youtube traffic?
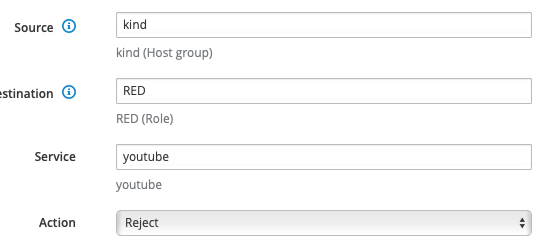
If I try to use this role - all traffic passes the firewall, no restricted access.