Hi,
first of all: I am really impressed of Nethserver. I have never seen it before, but it looks really great!
But now I have my first problem.
I installed Nethserver and setup the green and red interface. Green got the IP 10.0.0.1 during the installation. Red was configured with the public IP of my Rootserver. I installed the packages “Basic firewall”, “Bandwidth monitor”, “VPN” and “Intrusion Prevention System” because I want to use Nethserver primary as a Router, Firewall and VPN Gateway.
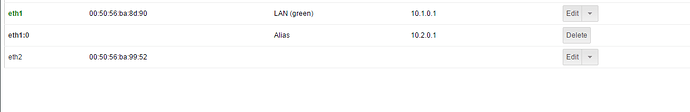
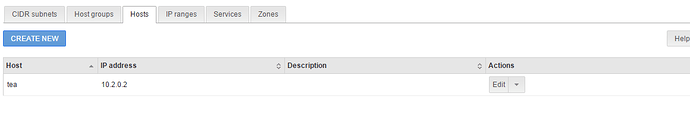
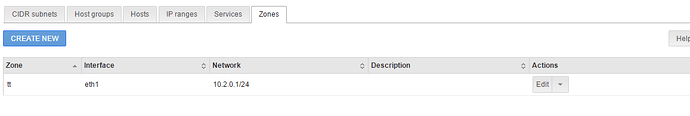
First I configured some Firewall Objects. By doing this, I recognized that I forgot to configure more IP-Addresses for Green Interface. So I added 10.1.0.1, 10.2.0.1 and 10.3.0.1 as an additional IP Alias for my Green eth1 interface.
After that I configured more Firewall Objects. The first thing I want to do is:
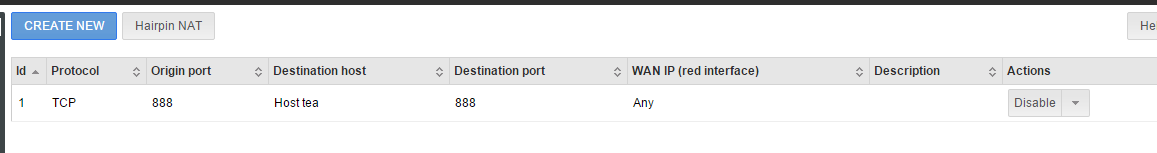
Forward HTTP-Traffic to Server 10.1.0.101 using a hostobject in the firewall rules configurator.
When I apply this, I get the following Error Message:
Task completed with error
Configuring shorewall #24 (exit status 1)
ERROR: Unknown destination zone (alias) /etc/shorewall/rules (line 121)
I tried to research about that error and found somebody that had problems with the IPS module. So I uninstalled it: no changes.
After that I realized, that there are Updates available for the Nethserver. I installed all Updates: No changes
After that I reinstalled the Firewall-Pack: No changes.
Now I don’t know what I can do to fix this issue.
When I change to the Network-Configuration, I get a hint, that the firewall is not running. When I click on this I get a page with this text:
Checking...
Processing /etc/shorewall/params ...
Processing /etc/shorewall/shorewall.conf...
Loading Modules...
Checking /etc/shorewall/zones...
Checking /etc/shorewall/interfaces...
Checking /etc/shorewall/hosts...
Determining Hosts in Zones...
Locating Action Files...
Checking /etc/shorewall/policy...
Running /etc/shorewall/initdone...
Adding Anti-smurf Rules
Adding rules for DHCP
Checking TCP Flags filtering...
Checking Kernel Route Filtering...
Checking Martian Logging...
Checking /etc/shorewall/masq...
Checking MAC Filtration -- Phase 1...
Checking /etc/shorewall/rules...
ERROR: Unknown destination zone (alias) /etc/shorewall/rules (line 121)
What do I have to do to get this running?
Finally the mentioned content of the file, that is mentioned in the error message:
# ================= DO NOT MODIFY THIS FILE =================
#
# Manual changes will be lost when this file is regenerated.
#
# Please read the developer's guide, which is available
# at https://dev.nethesis.it/projects/nethserver/wiki/NethServer
# original work from http://www.contribs.org/development/
#
# Copyright (C) 2013 Nethesis S.r.l.
# http://www.nethesis.it - support@nethesis.it
#
#
# Shorewall version 4 - Rules File
#
# For information on the settings in this file, type "man shorewall-rules"
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-rules.html
#
######################################################################################################################################################################################
#ACTION SOURCE DEST PROTO DEST SOURCE ORIGINAL RATE USER/ MARK CONNLIMIT TIME HEADERS SWITCH
# PORT PORT(S) DEST LIMIT GROUP
#SECTION ALL
#
#
# SECTION ESTABLISHED
#
?SECTION ESTABLISHED
#
# SECTION RELATED
#
?SECTION RELATED
#
# SECTION NEW
#
?SECTION NEW
#
# Accept Ping from the "bad" net zone.
#
Ping/ACCEPT net $FW
#
# Make ping work bi-directionally between the dmz, net, Firewall and local zone
# (assumes that the loc-> net policy is ACCEPT).
#
Ping/ACCEPT loc $FW
#
# Accept DNS connections from the firewall to the Internet
#
DNS/ACCEPT $FW net
#
# Service: httpd-admin Access: public
#
?COMMENT httpd-admin
ACCEPT loc $FW tcp 980
ACCEPT net $FW tcp 980
#
# Service: nmb Access: private
#
ACCEPT loc $FW udp 137
ACCEPT loc $FW udp 138
#
# Service: ntpd Access: private
#
ACCEPT loc $FW udp 123
#
# Service: openvpn Access: public
#
ACCEPT loc $FW udp 1194
ACCEPT net $FW udp 1194
#
# Service: redis-ntopng Access: NONE
#
#
# Service: slapd Access: private
#
?COMMENT slapd
ACCEPT loc $FW tcp 389
#
# Service: smb Access: private
#
?COMMENT smb
ACCEPT loc $FW tcp 139
?COMMENT smb
ACCEPT loc $FW tcp 445
#
# Service: sshd Access: public
#
?COMMENT sshd
ACCEPT loc $FW tcp 222
ACCEPT net $FW tcp 222
#
# 40l2tp -- accept L2TP nego from ivpn zone
#
?COMMENT l2tp
ACCEPT ivpn $FW udp 1701
#
# 50pf -- PORT FORWARDING
#
#
# 60rules
#
#
# RULE#3 any -> host;kappservertest
#
?COMMENT RULE#3
ACCEPT:none any alias:10.1.0.101 tcp 443
#
# RULE#1 any -> role;red
#
?COMMENT RULE#1 Allow outbound traffic
ACCEPT:none any net all
#
# RULE#2 iprange;knetwork -> iprange;hostnetwork
#
?COMMENT RULE#2 No Hostnetwork Access
DROP:none alias:10.1.0.0-10.1.0.255 loc:10.0.0.0-10.0.0.255 all
#
# 90dns_blue
#
Edit:
I started all over again but configuring all Interfaces including Aliases and doing updates first: Same issue.