Please elaborate on the above…
HAProxy? It’s OK, but nginx or even apache on NethServer may be a better choice…
So far, I’ve mainly used the NethServer for LetsEncrypt, even though the OPNsense could do that just as well.
The main reason for me is AD. A lot of Apps, especially Java and PHP programmed stuff require a valid SSL cert on the AD, if you want to use AD authentification. MeshCentral & Guacamole are two examples on the OpenSource/NethServer side which require a valid SSL cert for AD to work. EcoDMS, a commercial Java programmed software in common use in German speaking countries is another good example…
If using LetsEncrypt on NethServer, and NethServer is your AD, this is easily achieved.
You need to enter your AD (both name versions!) in your external DNS and - like your NethServer - point them to your firewalls external IP.
nano /etc/e-smith/events/certificate-update/S80push2ad
Contents:
cp -f -p /etc/pki/tls/certs/localhost.crt /var/lib/machines/nsdc/var/lib/samba/private/tls/cert.pem
cp -f -p /etc/pki/tls/private/localhost.key /var/lib/machines/nsdc/var/lib/samba/private/tls/key.pem
chmod 600 /var/lib/machines/nsdc/var/lib/samba/private/tls/key.pem
chmod 644 /var/lib/machines/nsdc/var/lib/samba/private/tls/cert.pem
systemctl -M nsdc restart samba
This will automatically copy the new certs to the NDSC container in NethServer, enabling your AD with a valid SSL cert.
Here’s a more complex problem, probably along the lines of what you’re trying to achieve later on with your containers…
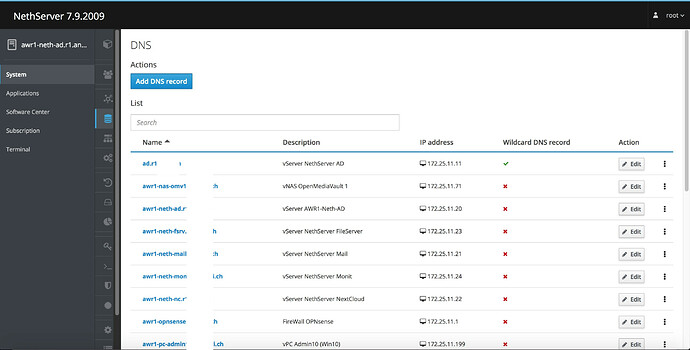
At home, I have a PI-Hole.
It’s real hostname is:
awr7-pi-hole.r7.anwi.ch
and has the internal IP 192.168.31.29, which is distributed to the DHCP clients from my DHCP server, my OPNsense firewall.
This PI-Hole only uses http, no https.
But if you like, try this:
https://pi-hole.r7.anwi.ch
My PI-Hole will be displayed correctly, with a correct SSL cert, even though I’m behind a dynamic IP address… What gives? 
Behind the scenes:
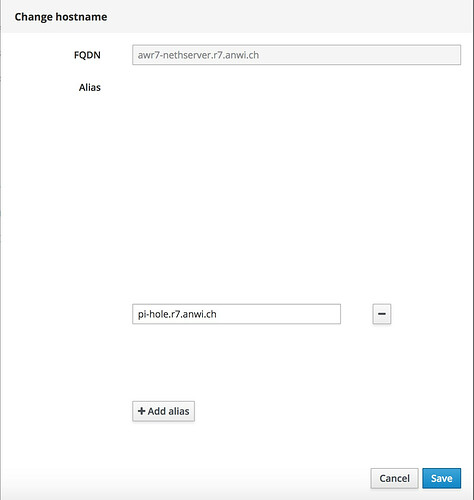
At home, in my LAN, my NethServer handles all LetsEncrypt SSL certs. It has the name “pi-hole.r7.anwi.ch” entered in as alias for the PI-Hole.
Note: This is NOT the real hostname of the PI-Hole!
Internally, pi-hole.r7.anwi.ch also points to the NethServer, as the external DNS. The external DNS can’t really resolve the real hostname of my PI-Hole.
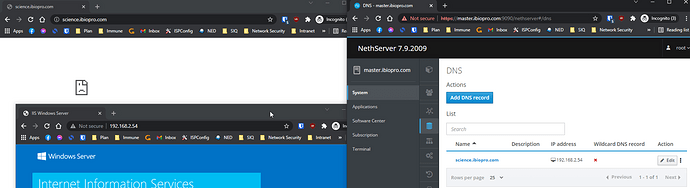
The NethServer acts as reverse Proxy, and adding in SSL protection at the same time. Externally, it “removes” the SSL layer before forwarding the traffic to my PI-Hole. The PI-Hole sees no SSL traffic and answers in normal http, which the reverse proxy attaches https encapsulation…
This gives me the best of both worlds.
Clean SSL protection and same access internally and externally, but also a seperate access via internal IP or real hostname if I need to eg update the PI-Hole or it’s OS.
Hope this is all somewhat understandable… 
My 2 cents
Andy