Im using ldap,roundcube,netxcloud. Its good. I’m trying change password inside configuration in roundcube but i can’t.
Hello @viniciogomez89,
Sorry, which password do you want to change? You can change passwords as admin from web UI users/groups or when you login to https://yournethserver:980 as user.
Thanks for answer me, Yes I can change the password from Web UI, but I need change this way, in roundcubemail with plugin password ldap_simple:
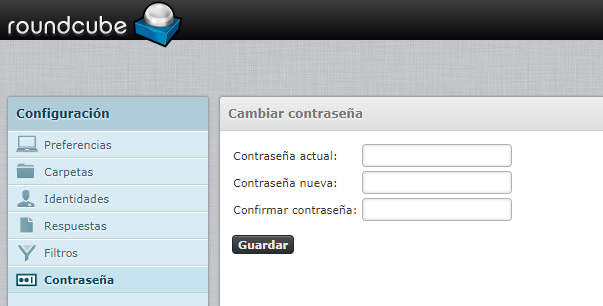
Nethserver 7 configuration domain:
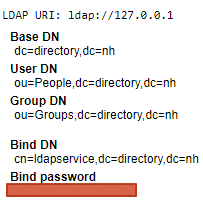
Directory dump:
# extended LDIF
#
# LDAPv3
# base <dc=directory,dc=nh> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# directory.nh
dn: dc=directory,dc=nh
objectClass: top
objectClass: dcObject
objectClass: organization
dc: directory
o: Example Org
# People, directory.nh
dn: ou=People,dc=directory,dc=nh
objectClass: top
objectClass: organizationalUnit
ou: People
# Groups, directory.nh
dn: ou=Groups,dc=directory,dc=nh
objectClass: top
objectClass: organizationalUnit
ou: Groups
# libuser, directory.nh
dn: cn=libuser,dc=directory,dc=nh
objectClass: device
objectClass: simpleSecurityObject
cn: libuser
description: libuser management account
# ldapservice, directory.nh
dn: cn=ldapservice,dc=directory,dc=nh
objectClass: device
objectClass: simpleSecurityObject
cn: ldapservice
description: ldapservice management account
# locals, Groups, directory.nh
dn: cn=locals,ou=Groups,dc=directory,dc=nh
gidNumber: 1000
cn: locals
objectClass: posixGroup
# admin, People, directory.nh
dn: uid=admin,ou=People,dc=directory,dc=nh
uidNumber: 1000
gidNumber: 1000
uid: admin
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/admin
shadowInactive: -1
shadowExpire: -1
gecos: admin
shadowFlag: -1
cn: admin
sn: admin
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: admin@megamaderas.com.ec
l: SANTO DOMINGO
ou: COMERCIAL
street: VIA QUEVEDO
telephoneNumber: 593991801748
o: Megamaderas
shadowLastChange: 17507
# domain admins, Groups, directory.nh
dn: cn=domain admins,ou=Groups,dc=directory,dc=nh
gidNumber: 1001
objectClass: posixGroup
memberUid: admin
cn: domain admins
# soporte, Groups, directory.nh
dn: cn=soporte,ou=Groups,dc=directory,dc=nh
gidNumber: 1002
cn: soporte
objectClass: posixGroup
memberUid: vinicio.gomez
# vinicio.gomez, People, directory.nh
dn: uid=vinicio.gomez,ou=People,dc=directory,dc=nh
uidNumber: 1001
gidNumber: 1000
uid: vinicio.gomez
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/vinicio.gomez
shadowInactive: -1
shadowExpire: -1
gecos: Vinicio Gomez
shadowLastChange: 17504
shadowFlag: -1
cn: Vinicio Gomez
sn: vinicio.gomez
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: vinicio.gomez@megamaderas.com.ec
l: SANTO DOMINGO
ou: COMERCIAL
street: VIA QUEVEDO
telephoneNumber: 593991801748
o: Megamaderas
# alex.lema, People, directory.nh
dn: uid=alex.lema,ou=People,dc=directory,dc=nh
uidNumber: 1003
gidNumber: 1000
uid: alex.lema
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/alex.lema
shadowInactive: -1
shadowExpire: -1
gecos: Alex Lema
shadowLastChange: 17505
shadowFlag: -1
cn: Alex Lema
sn: alex.lema
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: alex.lema@megamaderas.com.ec
# search result
search: 2
result: 0 Success
# numResponses: 12
# numEntries: 11
When try change password, i get this message:
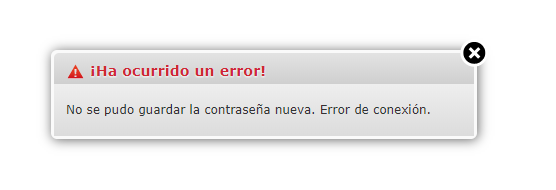
Can’t change the new password. Connection error.
Config roundcube:
/usr/share/roundcubemail/plugins/password/config.inc.php
// Password Plugin options
// -----------------------
// A driver to use for password change. Default: "sql".
// See README file for list of supported driver names.
$config['password_driver'] = 'ldap_simple';
// Determine whether current password is required to change password.
// Default: false.
$config['password_confirm_current'] = true;
// Require the new password to be a certain length.
// set to blank to allow passwords of any length
$config['password_minimum_length'] = 0;
// Require the new password to contain a letter and punctuation character
// Change to false to remove this check.
$config['password_require_nonalpha'] = false;
// Enables logging of password changes into logs/password
$config['password_log'] = false;
// Comma-separated list of login exceptions for which password change
// will be not available (no Password tab in Settings)
$config['password_login_exceptions'] = null;
// Array of hosts that support password changing. Default is NULL.
// Listed hosts will feature a Password option in Settings; others will not.
// Example:
//$config['password_hosts'] = array('mail.example.com', 'mail2.example.org');
$config['password_hosts'] = null;
// Enables saving the new password even if it matches the old password. Useful
// for upgrading the stored passwords after the encryption scheme has changed.
$config['password_force_save'] = true;
// Enables forcing new users to change their password at their first login.
$config['password_force_new_user'] = false;
// LDAP and LDAP_SIMPLE Driver options
// -----------------------------------
// LDAP server name to connect to.
// You can provide one or several hosts in an array in which case the hosts are tried from left to right.
// Exemple: array('ldap1.exemple.com', 'ldap2.exemple.com');
// Default: 'localhost'
$config['password_ldap_host'] = '127.0.0.1';
// LDAP server port to connect to
// Default: '389'
$config['password_ldap_port'] = '389';
// TLS is started after connecting
// Using TLS for password modification is recommanded.
// Default: false
$config['password_ldap_starttls'] = false;
// LDAP version
// Default: '3'
$config['password_ldap_version'] = '3';
// LDAP base name (root directory)
// Exemple: 'dc=exemple,dc=com'
$config['password_ldap_basedn'] = 'dc=directory,dc=nh';
// LDAP connection method
// There is two connection method for changing a user's LDAP password.
// 'user': use user credential (recommanded, require password_confirm_current=true)
// 'admin': use admin credential (this mode require password_ldap_adminDN and password_ldap_adminPW)
// Default: 'user'
$config['password_ldap_method'] = 'user';
// LDAP Admin DN
// Used only in admin connection mode
// Default: null
$config['password_ldap_adminDN'] = null;
// LDAP Admin Password
// Used only in admin connection mode
// Default: null
$config['password_ldap_adminPW'] = null;
// LDAP user DN mask
// The user's DN is mandatory and as we only have his login,
// we need to re-create his DN using a mask
// '%login' will be replaced by the current roundcube user's login
// '%name' will be replaced by the current roundcube user's name part
// '%domain' will be replaced by the current roundcube user's domain part
// '%dc' will be replaced by domain name hierarchal string e.g. "dc=test,dc=domain,dc=com"
// Exemple: 'uid=%login,ou=people,dc=exemple,dc=com'
$config['password_ldap_userDN_mask'] = 'uid=%login,ou=People,dc=directory,dc=nh';
// LDAP search DN
// The DN roundcube should bind with to find out user's DN
// based on his login. Note that you should comment out the default
// password_ldap_userDN_mask setting for this to take effect.
// Use this if you cannot specify a general template for user DN with
// password_ldap_userDN_mask. You need to perform a search based on
// users login to find his DN instead. A common reason might be that
// your users are placed under different ou's like engineering or
// sales which cannot be derived from their login only.
$config['password_ldap_searchDN'] = 'cn=roundcube,ou=services,dc=example,dc=com';
// LDAP search password
// If password_ldap_searchDN is set, the password to use for
// binding to search for user's DN. Note that you should comment out the default
// password_ldap_userDN_mask setting for this to take effect.
// Warning: Be sure to set approperiate permissions on this file so this password
// is only accesible to roundcube and don't forget to restrict roundcube's access to
// your directory as much as possible using ACLs. Should this password be compromised
// you want to minimize the damage.
$config['password_ldap_searchPW'] = 'WElImv6z7wQaXJ7y';
// LDAP search base
// If password_ldap_searchDN is set, the base to search in using the filter below.
// Note that you should comment out the default password_ldap_userDN_mask setting
// for this to take effect.
$config['password_ldap_search_base'] = 'ou=People,dc=directory,dc=nh';
// LDAP search filter
// If password_ldap_searchDN is set, the filter to use when
// searching for user's DN. Note that you should comment out the default
// password_ldap_userDN_mask setting for this to take effect.
// '%login' will be replaced by the current roundcube user's login
// '%name' will be replaced by the current roundcube user's name part
// '%domain' will be replaced by the current roundcube user's domain part
// '%dc' will be replaced by domain name hierarchal string e.g. "dc=test,dc=domain,dc=com"
// Example: '(uid=%login)'
// Example: '(&(objectClass=posixAccount)(uid=%login))'
$config['password_ldap_search_filter'] = '(uid=%login)';
// LDAP password hash type
// Standard LDAP encryption type which must be one of: crypt,
// ext_des, md5crypt, blowfish, md5, sha, smd5, ssha, ad, cram-md5 (dovecot style) or clear.
// Please note that most encodage types require external libraries
// to be included in your PHP installation, see function hashPassword in drivers/ldap.php for more info.
// Multiple password Values can be generated by concatenating encodings with a +. E.g. 'cram-md5+crypt'
// Default: 'crypt'.
$config['password_ldap_encodage'] = 'crypt';
// LDAP password attribute
// Name of the ldap's attribute used for storing user password
// Default: 'userPassword'
$config['password_ldap_pwattr'] = 'userPassword';
// LDAP password force replace
// Force LDAP replace in cases where ACL allows only replace not read
// See http://pear.php.net/package/Net_LDAP2/docs/latest/Net_LDAP2/Net_LDAP2_Entry.html#methodreplace
// Default: true
$config['password_ldap_force_replace'] = true;
// LDAP Password Last Change Date
// Some places use an attribute to store the date of the last password change
// The date is meassured in "days since epoch" (an integer value)
// Whenever the password is changed, the attribute will be updated if set (e.g. shadowLastChange)
$config['password_ldap_lchattr'] = '';
// LDAP Samba password attribute, e.g. sambaNTPassword
// Name of the LDAP's Samba attribute used for storing user password
$config['password_ldap_samba_pwattr'] = '';
// LDAP Samba Password Last Change Date attribute, e.g. sambaPwdLastSet
// Some places use an attribute to store the date of the last password change
// The date is meassured in "seconds since epoch" (an integer value)
// Whenever the password is changed, the attribute will be updated if set
$config['password_ldap_samba_lchattr'] = '';
I get log slapd:
/var/log/roundcubemail/errors
[08-Dec-2017 22:25:15 UTC] PHP Warning: ldap_bind(): Unable to bind to server: Invalid credentials in /usr/share/roundcubemail/plugins/password/drivers/ldap_simple.php on line 135
I need help for this.
I found this thread, server-manager is the way to go:
https://community.nethserver.org/t/users-change-password-remotely/8410
That is a bit of a no-go. There was recently a vulnerability in the servermanager that underlines why iirc.
There really should be an isolated webpage just for that single purpose and even then it is a security risk one should debate over before implementing it.
Server-manager is not the way to go, since that means the entire server-manager needs to be exposed to the Internet in order for remote users to change their passwords. That’s an unacceptable security risk. There needs to be a page that can be safely exposed to the 'net that will allow users to change their passwords. Code it so root/admin can’t change their password that way, so any vulnerability/attack there won’t result in the admin being locked out.
Sorry, I didn’t want to advice you to go server manager but after looking in your support thread and the answers I thought it’s the default way to do it via server manager. The splitting of admin and user page has some advantages I fully understand. Like SME or webmin/usermin does. What about changing your support topic to a feature request or open a new feature request?
I guess it’s correct to say that, as Neth is currently written, through the server manager is the only proper way to change a user’s password. I don’t think that’s a good answer (as described above and in my thread), but it’s apparently the only answer at this time. If editing my thread to add the Feature category will help in some way, why not?
yes the user page is an interesting feature, then after that the 980 could be closed to the wan if needed
As an alternative, fail2ban protects the server-manager
There are more ways to change your password. Password change on joined windows ws is propagated properly.
The conclusion would be that the webapps you use, do not support it.
+1 for feature request for chrooted user password change page.
New function request, is it possible? What is the application process?
Yes alternative change password without exposed server-manager by wan side
Feature → Howto (->wiki) → Development
If a feature is interesting, a howto should be written, so others can easily use and test the new feature. When it’s alright we may think about a module/package.
How can we setup this user page? I tried usermin, but way too much for just pw changing. A httpd-user with Nethgui for that? Would it be possible to provide access to cockpit apps from zones? Or yet another javascript framework login page with 3 fields for pw changing? Or something in between? Just some ideas…
I am just afraid it will not be recognized in support and a feature request may be the beginning of an installable module…
What I have in mind is simple, but not easy to do, at least I have not tried yet 
In short
close the 980 to green
do a reverse proxy /user to https:localhost:980
the only difficulty is that it is a ssl reverse proxy, it is a bit harder than a simple reverse proxy, but it should work
As I said, not tested yet
This solution is not perfect but much more simpler than rewrite a new server-manager for users. It is the case of the user-manager in SME Server. The user page is done by the old perl-cgi, and I’m even not sure it is really secured or maintained.
Absolutely agree. Simple way and reusing what’s already there is best approach here.
I’ll test a little and report…
Tried it on a local testmachine but had problems with SSL certificate (server certificate does NOT include an ID which matches the server name) so I tried on my VPS where I use letsencrypt cert with apache proxypass, which I just configured via web UI and it seems to correctly redirect, but:
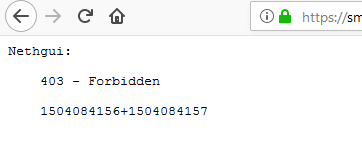
403 - Forbidden
1504084156+1504084157/var/log/messages:
Dec 10 20:42:41 nethserver httpd: [ERROR] Nethgui\Framework: Same origin assertion failed. The request must not be proxied.Well markuz, I changed my mind, Was probably a bit ill lastly 
The goal to create a ssl reverse proxy /user to the port 980 is good if we adapt to a particular name. If we don’t do this, then, once known it is the same thing, everybody will know it like the 980 port.
So I’m wondering if the best approach could not be to change the port 980 in the httpd-admin e-smith database.
Does it mean we have two ports, so firewall control would be given? Would it be possible to forbid root login from a zone via your delegation module?
I’d like to sum up my thoughts:
What do do:
- have some portal to login
- make it possible for users to login and change their passwords
- make it impossible for root or higher privileged users (delegation module) to login at the same portal
So we are flexible and have following solutions, fitting any needs:
- Default, as it is now, one httpd-admin
- Split, like httpd-admin and httpd-user, so it can be controlled and firewalled seperately.
- Paranoid, turning off everything completely