What do you think @Andy_Wismer
The green works nicely
The RED CARD IS ONLY FOR THE VPN NO OTHER USE.
the Modem forwards port 1194 directly to the RED IP,
the problem is probably routing from THE RED TO THE GREEN
Thank you
@stephdl
Sorry, was on the road visiting today…
NS7 can easily create and operate an OpenVPN network with only one Interface, using an existing router / firewall.
What’s needed:
- NS7 with only one NIC, but correctly entered Gateway (Your Fortinet LAN), this NIC is connected to your LAN.
- A Port Forward Internet → Fortinet WAN → NS7 LAN for port 1194 to NS7 from your Fortinet (Entered in Fortinet)
- A Routing for the IP Network of the used OpenVPN VPN Network (The OpenVPN Network in NS7) entered in your Fortinet, pointing to your NS7 LAN as “Gateway” to reach the VPN.
Easiest would be to remove the RED interface (NIC) from NS7, leaving only a LAN NIC on NS7.
This will work “out of the box”, if the correct external IP of the Fortinet is used as connection point.
My 2 cents
Andy
Dear Andy,
I have set the port forwarding on my modem to the Fortigate 60f and then forwarded the port 1194 on the 60f to the server 192.168.1.90
Hi Andy,
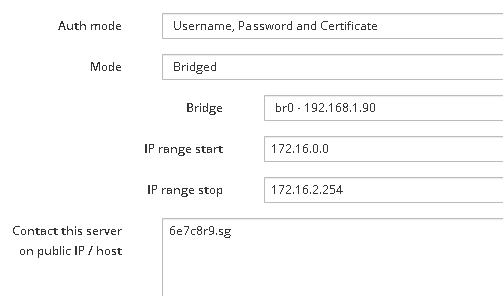
When I configure the OpenVPN like this it accepts it…

But when I change it to bridge
The openvpn client says
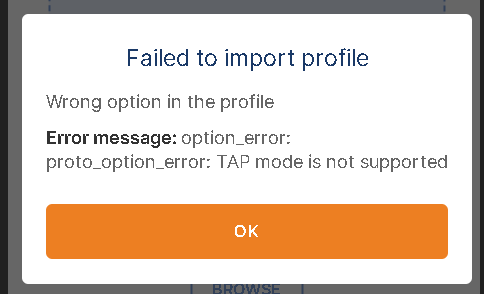
What do you think?
with the first connection i get the routing error… why. because it is a bridge …
It is a bridge because it is a AD/DC.
Sepp
Happy New Year @Sepp1945 ,
Would you mind stopping adding your commercial signature to every post please? This is not the place to advertise your commercial activities. It is distracting from topics at hand and hijacking a lot of screen space, nor is it a custom to do so on these forums.
Thanks!
Hi Andy,
Please let me introduce you to our project.
Hardware:
2 fiber modems ( 1x 800 Mbps … Master 1x 300 Mbps … Test)
1x Fortinet FortiGate 60F
1 x DELL EMC T 440
Intel(R) Xeon(R) Silver 4210R CPU @ 2.40GHz x 20
RAM 323GB
BOSS1 ( 2 x 440GB M.2 RAID 1 440 GB)
8 x 16 TB HDD (RAID 5 87TB)
QNAP NAS TS-431 P2
4 x 6TB HDD (RAID 5 16TB)
Software:
NethServer 7.9.2009
Project:
Provide VPN access for up to 1000 users with following services:
I apologize, my email is setup like that, I will remove it from now on.
Sorry again
Sepp
Thanks, much appreciated!
Hi @Sepp1945
I do have about 30 NethServers in VM (Proxmox) I maintain for my clients.
These all have hardware firewalls (OPNsense) and in these cases OPNsense handles the OpenVPN.
I also maintain a couple of NethServer7 in cloud installations, and here NethServer does VPN, besides other Tasks (AD, File, Mail, etc.)
All of these servers use AD, LDAP on NS doesn’t support authenticated file sharing, making LDAP useless for me.
All work!
This statement implies to me your so called “modem” is actually a “router”, creating a new network (NAT).
Your Fortinet does basically the same.
This means you have “double NAT”.
→ This is no issue for VPNs, it can work - if one gets the routing correctly.
The Fortinet, as a full sized Firewall, is VERY fussy about this. I’d say both your Fortinet and your “modem” are causing the problems with “routing”.
OpenVPN, and other VPNs nowadays do not use “Bridge” anymore, nowadays VPNs use Routing.
Bridge is crap for several reasons:
- External use of internal IPs mean less IPs in that subnet usable internally.
- Security is generally worse, as outside and inside is only verifiable, when checking against VPN clients.
- other caveats with bridging.
Being AD is NOT an issue for either routing or bridging, I have quite a few OpenVPNs running of a NethServer, whisch also runs AD, and all use Routing for VPN.
One example of a NethServer (Behind a OPNsense firewall) doing AD, but also doing OpenVPN - without issues!
Do note that the connection point for external VPNs is here a IPv4 adress, not IPv6. IPv6 isn’t an issue for OpenVPN as such, but is a major problem for NethServer, which can’t really handle IPv6.
I disable all IPv6 from my clients networks when running NS7, just to avoid problems.
I would strongly suggest that you use only IPv4 in this case!
My suggestions for a solution:
Provider-Side:
Ask if your provider modem can use pass-thru, meaning your Fortinet get’s a real, routable Internet IP, and not one from the so called Private IP pools (10.x.x.x, 172.16.x.x-172.31.254.254, 192.168.x.x).
This removes double NAT, but also makes your Fortinet into a real router, with real IPs.
And your provider should provide you with an IPv4 IP, not just an IPv6 adress!
I know this is not always possible!
Fortinet Side:
Here 3 things are needed:
Evade IPv6 use in the LAN network when possible!
Port Forwarding the used OpenVPN Port (here 1194) from Fortinet to LAN of NS7 (This is done, as I read).
The other, just as important is a “static route” for the VPN network.
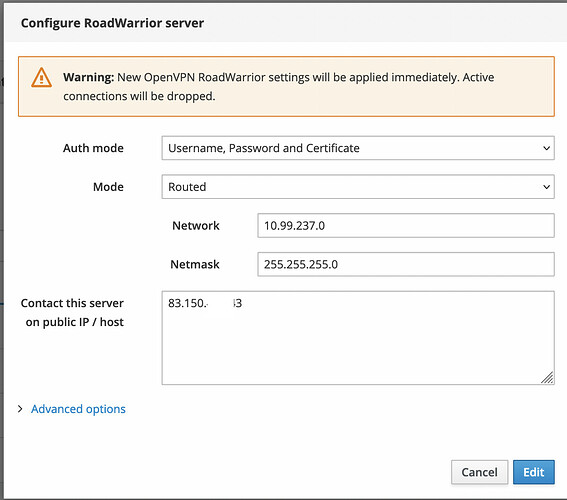
In my Screenshot, I’m using the network 10.99.237.0/24 for this.
Why this routing?
Your Fortinet is a firewall, with at least two NICs, WAN (Internet side) and LAN.
As it begins with a 10, the network 10.99.237.0/24 is “internal”, but as your Fortinet does not “know” this, and this IP is not part of the Fortinets “LAN”, it will forward any client replies to the VPN (including from NS7) to the Internet, not to the VPN (VPN Gateway)! And your provider does what he must do: throws away these internal IP packets (drop) BEFORE reaching the internet…
→ The “routing” problem you’re getting.
NethServer side:
Evade IPv6 use in the LAN network when possible!
Set the OpenVPN as per my example, using routing!
You also need to make sure this VPN Network, in my example the 10.99.237.0/24, is entered in the “trusted networks” of NethServer 7! Without this, even a authenticated VPN client would not be able to access any resources on NS7 (Samba, AD, etc…).
NS7 normally does this automatically, when set to routing, but still, check it!
All the above points should help you to get a working VPN!
I can help with generic VPN issues, but not specific Fortinet configurations. While I do consider Fortinet as a usable, secure firewall, it’s like Cisco a “PITA” to configure…
But the Fortinet Forum should be able to help, else contact Fortinet directly for help.
I know they (Fortinet) prefer you using Fortinets pay-per VPN for this!
Also thanks for removing the optical distractions, aka advertising signature…
I hope all the above is “understandable”, and helps to solve the issues.
A steep challenge, considering NethServer 7 is optimized as a SME server, and SME (Small, Medium enterprises) is usually defined as 2-500 users…
Note: It’s still doable and stable, but does need quite a few specific considerations!
Your available hardware should be sufficient. Planning and Configuration is the real challenge here.
Considering the size, I would strongly suggest using Proxmox virtualization underneath, just to give you higher availability and hardware independance for disaster recovery situations, but also backups, etc.
All my clients use Proxmox as Hypervisor, I do not install “native” servers for about 5 years now (only special cases like Cloud, but even there, I prefer virtualization!).
And with all larger IT projects: Good Luck!
Sure, know-how helps, but as is well known: “sh*t happens”, and if it comes from “Murphy”…
(Murphy = If it can fail, it will!).
My 2 cents
Andy
PS:
If you need more / specific assistance for this project, contact me using PM on this forum.
Click on my Name/Photo top left of every post, and click on “Message”…
This can keep IPs and other confidential stuff “confidential” from the “masses”.
Please see below
Thanks
Sepp
Hi @Sepp1945
It might be easier if you used the Web Interface, instead of mail.
It does allow for a few more options!
My 2 cents
Andy
Dear Andy,
i have sent you emails to your info address,
Sepp