Hi everybody! Thanks for responding!
Some more information;
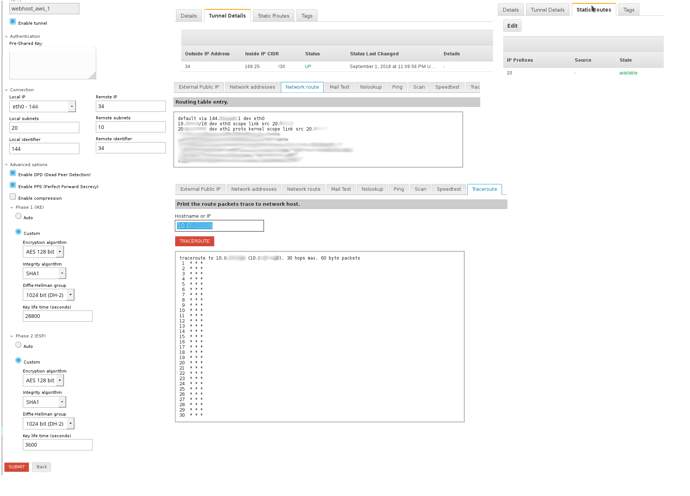
Yes, my NethServer does have a public IP, and that is the interface I’m using to connect.
Here are some screenshots of my configuration.
The 144 is my public IP address.
the 34 is the address I need to connect to.
The 20 is my local network
The 10 is the remote network
On the 10 network there is a machine I’m trying to connect to, but cannot because there is no pathway.
Here are some of the instructions that Amazon sent me:
IPSec Tunnel #1
================================================================================
#1: Internet Key Exchange Configuration
Configure the IKE SA as follows:
Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
The address of the external interface for your customer gateway must be a static address.
Your customer gateway may reside behind a device performing network address translation (NAT).
To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500. If not behind NAT, we recommend disabling NAT-T.
- IKE version : IKEv1
- Authentication Method : Pre-Shared Key
- Pre-Shared Key : *******
- Authentication Algorithm : sha1
- Encryption Algorithm : aes-128-cbc
- Lifetime : 28800 seconds
- Phase 1 Negotiation Mode : main
- Diffie-Hellman : Group 2
#2: IPSec Configuration
Configure the IPSec SA as follows:
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
- Protocol : esp
- Authentication Algorithm : hmac-sha1-96
- Encryption Algorithm : aes-128-cbc
- Lifetime : 3600 seconds
- Mode : tunnel
- Perfect Forward Secrecy : Diffie-Hellman Group 2
IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We
recommend configuring DPD on your endpoint as follows:
- DPD Interval : 10
- DPD Retries : 3
IPSec ESP (Encapsulating Security Payload) inserts additional
headers to transmit packets. These headers require additional space,
which reduces the amount of space available to transmit application data.
To limit the impact of this behavior, we recommend the following
configuration on your Customer Gateway:
- TCP MSS Adjustment : 1379 bytes
- Clear Don't Fragment Bit : enabled
- Fragmentation : Before encryption
#3: Tunnel Interface Configuration
Your Customer Gateway must be configured with a tunnel interface that is
associated with the IPSec tunnel. All traffic transmitted to the tunnel
interface is encrypted and transmitted to the Virtual Private Gateway.
The Customer Gateway and Virtual Private Gateway each have two addresses that relate
to this IPSec tunnel. Each contains an outside address, upon which encrypted
traffic is exchanged. Each also contain an inside address associated with
the tunnel interface.
The Customer Gateway outside IP address was provided when the Customer Gateway
was created. Changing the IP address requires the creation of a new
Customer Gateway.
The Customer Gateway inside IP address should be configured on your tunnel
interface.
Outside IP Addresses:
- Customer Gateway : 144*******
- Virtual Private Gateway : 34*********
Inside IP Addresses
- Customer Gateway : 169.254.**.***/30
- Virtual Private Gateway : 169.254.**.***/30
Configure your tunnel to fragment at the optimal size:
- Tunnel interface MTU : 1436 bytes
#4: Static Routing Configuration:
To route traffic between your internal network and your VPC,
you will need a static route added to your router.
Static Route Configuration Options:
- Next hop : 169.254.**.***
You should add static routes towards your internal network on the VGW.
The VGW will then send traffic towards your internal network over
the tunnels.