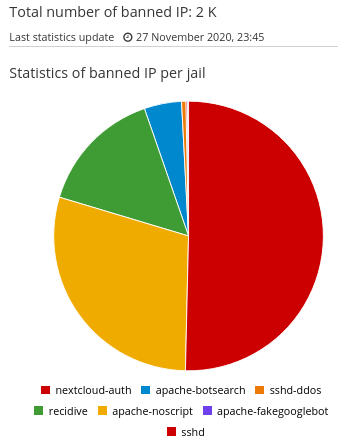
It must be this time of year because this morning I woke up with over 60 mails from fail2ban on SSH connect attempts. Do you guys notice an increase in attempts to log in with SSH lately? Since I have a 3 x failed = block policy, the number of attempts is around 200 in just one night. That’s quite a lot more than normal for my server.
This is a fire period, but nice weather and bad wheater not during all time 
Holy Kamoly…
At the beginning of September received between 30 and 100ish sshd fail2ban e-mails per day (increased time span + ban time, blocked some of the offending network IP ranges…) Attack lasted about 2 weeks.
I’m increasingly becoming a fan of geo IP white listing and dealing with any potential routing issues down the road - reduces noise and attack surface but isn’t as fool proof.
Hi Rob,
Try changing the port for ssh other than 22.
Also, I disabled the messages from F2Ban: too many of them…
Michel-André
SSH is running on an alternative port. I have no worries. Fail2ban is doing a great job.
Little trick that may help: the port of SSH should not contain 22. I think that some “conditionated” portscan looks for the combination of numbers with 22 inside.
Same again here for the past days. In a period of about 2 days I got almost 650 fail2ban emails related to sshd bans, then stopped.
Annoying non the least, but on the bright side it is reassuring knowing Stéphane’s “baby” is doing its job: