Hello, i tested joining Nethserver/NSDC to a Windows Server 2003 R2 Standard and at least the joins worked.
I used https://wiki.samba.org/index.php/Joining_a_Samba_DC_to_an_Existing_Active_Directory as a starting point.
I setup a new domain admin called superuser to make the joins.
I did:
systemd-run -M nsdc -t /bin/bash
On the NSDC:
echo domain cmb.local > /etc/resolv.conf
Added my Windows Server as nameserver
echo nameserver 192.168.1.20 >> /etc/resolv.conf
Joining:
samba-tool domain join cmb DC -U"CMB\superuser" --dns-backend=NONE --simple-bind-dn=CN=superuser,CN=Users,DC=cmb,DC=local
Result of joining:
Finding a writeable DC for domain ‘cmb’
Found DC zeus.cmb.local
Password for [CN=superuser,CN=Users,DC=cmb,DC=local]:
workgroup is CMB
realm is cmb.local
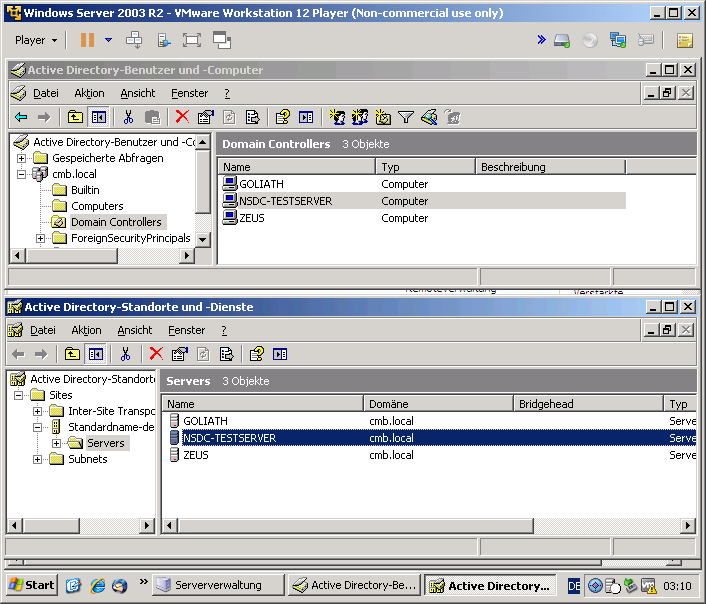
Adding CN=NSDC-TESTSERVER,OU=Domain Controllers,DC=cmb,DC=local
Adding CN=NSDC-TESTSERVER,CN=Servers,CN=Standardname-des-ersten-Standorts,CN=Sites,CN=Configuration,DC=cmb,DC=local
Adding CN=NTDS Settings,CN=NSDC-TESTSERVER,CN=Servers,CN=Standardname-des-ersten-Standorts,CN=Sites,CN=Configuration,DC=cmb,DC=local
Adding SPNs to CN=NSDC-TESTSERVER,OU=Domain Controllers,DC=cmb,DC=local
Setting account password for NSDC-TESTSERVER$
Enabling account
Calling bare provision
Looking up IPv4 addresses
Looking up IPv6 addresses
Setting up secrets.ldb
Setting up the registry
Setting up the privileges database
Setting up idmap db
Setting up SAM db
Setting up sam.ldb partitions and settings
Setting up sam.ldb rootDSE
Pre-loading the Samba 4 and AD schema
A Kerberos configuration suitable for Samba AD has been generated at /var/lib/samba/private/krb5.conf
Provision OK for domain DN DC=cmb,DC=local
Starting replication
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[402/1677] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[804/1677] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[1206/1677] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[1553/1677] linked_values[0/0]
Analyze and apply schema objects
Partition[CN=Configuration,DC=cmb,DC=local] objects[402/4808] linked_values[0/0]
Partition[CN=Configuration,DC=cmb,DC=local] objects[804/4808] linked_values[0/0]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1206/4808] linked_values[0/0]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1608/4808] linked_values[0/0]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1703/4808] linked_values[0/0]
Replicating critical objects from the base DN of the domain
Partition[DC=cmb,DC=local] objects[94/94] linked_values[0/0]
Partition[DC=cmb,DC=local] objects[326/3469] linked_values[0/0]
Done with always replicated NC (base, config, schema)
Exop on[CN=RID Manager$,CN=System,DC=cmb,DC=local] objects[3] linked_values[0]
Committing SAM database
Sending DsReplicaUpdateRefs for all the replicated partitions
Setting isSynchronized and dsServiceName
Setting up secrets database
Joined domain CMB (SID S-1-5-21-2773429375-1845033767-2786721901) as a DC
Replication test looks good:
bash-4.2# samba-tool drs showrepl
Standardname-des-ersten-Standorts\NSDC-TESTSERVER
DSA Options: 0x00000001
DSA object GUID: 1cb522fe-8296-4bb2-8fc6-688d0fd8779a
DSA invocationId: 73102b65-96ed-42ba-bbbc-79d7c097209d
==== INBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:20:34 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:20:34 2017 CEST
CN=Configuration,DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:20:34 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:20:34 2017 CEST
DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:20:37 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:20:37 2017 CEST
==== OUTBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:04:41 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:04:41 2017 CEST
CN=Configuration,DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:04:41 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:04:41 2017 CEST
DC=cmb,DC=local
Standardname-des-ersten-Standorts\ZEUS via RPC
DSA object GUID: 2a3fbf55-751c-48e5-af46-e478727bd509
Last attempt @ Mon Aug 28 03:04:41 2017 CEST was successful
0 consecutive failure(s).
Last success @ Mon Aug 28 03:04:41 2017 CEST
==== KCC CONNECTION OBJECTS ====
Joining the nethserver to AD worked after few tries and reboots. I think, the DNS update error is because of selecting dns-backend=NONE when joining.
[root@testserver ~]# net ads join -Usuperuser
Enter superuser’s password:
Using short domain name – CMB
Joined ‘TESTSERVER’ to dns domain ‘cmb.local’
DNS update failed: NT_STATUS_IO_TIMEOUT
Not working joins looked like:
[root@testserver ~]# net ads join -Usuperuser
Enter superuser’s password:
gss_init_sec_context failed with [Unspecified GSS failure. Minor code may provide more information: Server not found in Kerberos database]
kinit succeeded but ads_sasl_spnego_gensec_bind(KRB5) failed: An internal error occurred.
Failed to join domain: failed to connect to AD: An internal error occurred.
I created a user named testuser1 with “samba-tool user create testuser1” and it was replicated after hours so I could see it on the Windows Server, what made me really happy.
But still having problems with Kerberos
[root@testserver ~]# kinit
kinit: Cannot find KDC for realm “CMB.LOCAL” while getting initial credentials
[root@testserver ~]# net domain -k -S192.168.1.20 -Uadministrator
Enter administrator’s password:
Kinit for administrator to access (null) failed: Cannot find KDC for requested realm
Enumerating domains:
Domain name Server name of Browse Master ------------- ---------------------------- CMB ZEUS WORKGROUP LIBREELEC
/var/log/messages is full of:
Aug 28 04:00:33 testserver dnsmasq[943]: Maximum number of concurrent DNS queries reached (max: 150)
Giving up for today…
Unfortunately I saw this thread and the instructions in the wiki after trying these things on my own. I’ll give it another try with the help of the wiki and report back my experiences to this thread…