I respect your expertise in OPNsense,
I’ve been installing and maintaining NethSecurity firewalls for 5 years now, across nearly 200 diverse environments, so I feel my experience gives me a solid foundation to express an informed opinion on this product.
From version 1.5.0 to 6, 7, and now 8, I’ve seen it all.
Like you, I am not paid by Nethesis, OPNsense, or any other vendor. My opinions are my own.
I also read the other thread where you were talking about system stability.
I can guarantee that in terms of system stability, I have never had any problems other than hardware.
The APU Alix boxes that you also use, it happened in some models that one of the network cards would burn out or the power supply, but I never had a system crash.
One of the many firewalls:
NICs Bridge:
If you try to install the system on a server rather than in a box, you will realize that the order of the network cards (previously CentOS, now OpenWRT) is not always correct. So you find yourself searching for the correct network card at first startup. With all the cards in a bridge, you connect the cable to any port, log in, and identify them by their MAC addresses. Next you can delete the bridge easly.
I find this very useful.
Domain .lan:
You are absolutely right; I agree, they should change the default domain. It’s also true that changing it takes half a second, but if it had a different name by default, maybe less experienced users would leave it as is. (But do newbies really install firewalls? I hope not.)
Threat Shield:
Community lists do not have confidence levels. But excuse me, how can you give a confidence level to a community list? It seems more than risky to do so. Would you trust a list of public IPs made by third parties for free?
If you subscribe to the paid lists, there is indeed a confidence level.
This is to say that if you want free lists, obviously they can never tell you if they will be well maintained or not. If you buy them, there are companies paid to do this job. Who would bother to do it otherwise?
Wireguard:
They have added WireGuard to the image, but if you read in the “to do” it is under development the GUI to support it.
LetsEncrypt
Let’s Encrypt doesn’t work on .lan?
If you register a subdomain that points to the public IP of the firewall and request the certificate, it works perfectly. I don’t understand the connection to the FQDN."
LDAP o AD
Am I missing something, or are you perhaps judging without knowing the product?
DNS
You’re talking about split-DNS. But in large companies, do you really entrust this task to the firewall? I don’t work with any large companies that need split-DNS and don’t have Active Directory.
And no, they don’t use the firewall as a DNS server.
Or, since you mention TXT, CNAME, etc., are you perhaps talking about hosting infrastructures?
Forgive me, but Nethsecurity may not be the right product for these kinds of infrastructures, but neither is OPNsense… We’re talking about different levels here. I sincerely hope they use truly serious products, like Palo Alto (look at who Google NGFW or Amazon NGFW rely on… Palo Alto, of course).
Security by Obscurity
I don’t understand the example of changing the ssh port.
They give you the possibility to change the port but this does not mean that they are telling you to do it for security reasons.
In fact you can set a key or set the 2fa.
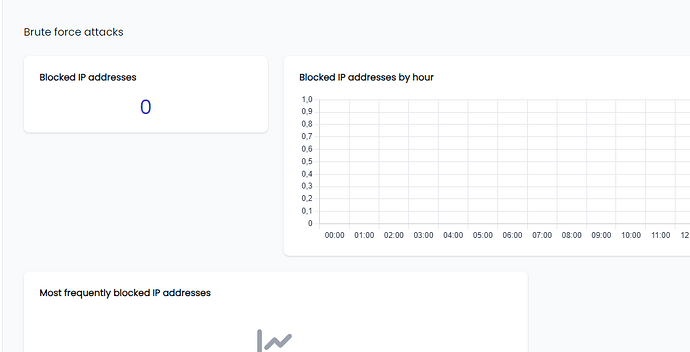
Also, the threat shield module monitors bruteforce requests to the ssh service as you can see:
I’ll stop here because the conversation would become a debate and that’s not what I want to do. Do you want to know what I think instead?
I think what is really MISSING, and as far as I’m concerned I consider it fundamental for a firewall distro are:
-
The possibility to configure 2fa ALSO for ssh (I would not leave it open from the outside anyway but in very particular situations it might be necessary, for example for an ssh tunnel)
-
Threatshield control (ex failban in NS7) also for the Nethesis UI, not just for luci or ssh
-
A LOCAL IPS, which does not depend on external services such as the threat shield, a package which in my opinion is fundamental. From what I understand they are implementing it
-
keepalived or ucarp. I know that keepalived is in development and will be released soon. For me it is essential to be able to make a physical firewall redundant in critical installations