Which Windows 10 build version do you use? You may check with winver.exe.
EDIT:
Working here with Firefox 74 on Windows 10 1903…
Edge not working with cockpit at all - I am going to update to Win 10 1909 now and recheck…
Which Windows 10 build version do you use? You may check with winver.exe.
EDIT:
Working here with Firefox 74 on Windows 10 1903…
Edge not working with cockpit at all - I am going to update to Win 10 1909 now and recheck…
I am working with Win 10 Version 1909 Build 18363.720
This is the latest Patchlevel from last Thuesday. Edge and FF are also on the latest Patchlevel.
Hm, I can’t reproduce.
It’s working here with actual versions. Edge 80.0.361.66 64bit and Firefox 74.0 64bit on Win 10 1909 18363.720.
I left windows since light years now, really not confident nor expert, but do some antivirus/script blocker or no javascript module for browser could do this ?
merged 









please could you verify the work
We are proud to announce that the One time password feature to protect the login to cockpit is released…you simply have to update nethserver-cockpit and enable it for each user under the user’s settings page
https://docs.nethserver.org/en/v7/base_system2.html#two-factor-authentication-2fa
Kudos to @stephdl which did a tremendous job!!
@stephdl already implemented 2FA also for SSH with password authentication!
Kudos again!
it is possible to show the secret code too, not just the QRCode image ?
It is very practical with BitWarden and/or for freak who think it is possible to spoof QR Code.
Here an example from Nextcloud
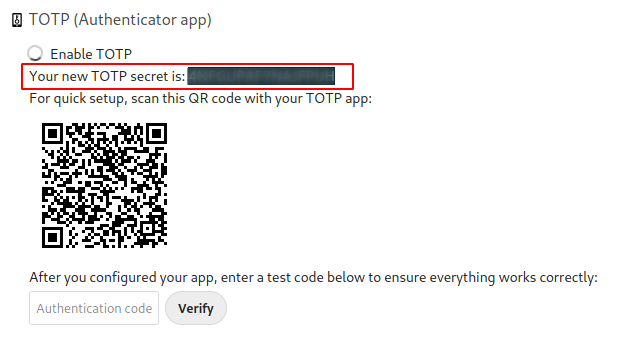
I think we could write the base32 secret, it is what we use to generate the url
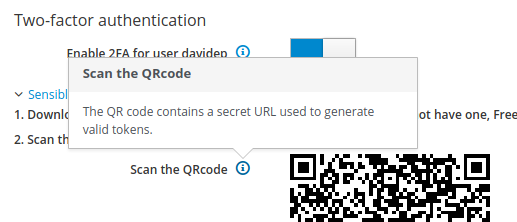
IIUC TOTP key is an equivalent of the QRcode… In this case I’d expect it has the same style of QRcode and Backup codes fields, with a circled “i” that briefly explains what to do.
sometimes less is more, isn’t it 
And not implementing it at all: it is even better! 
Joke apart, I use the TOTP key to make a wrapper in my terminal
/usr/bin/oathtool --totp -b JSLB2WRJAEU5I5TYUHUG4W2QWZQHNBL4
So I am not sure we need a lot more works.
People would like also a way to save the key, but in that case we need to save the hex key because it is what we use in .2fa.secret
So maybe it would make more sense to display the hex key
I installed BitWarden: it has the QR scan function too. Isn’t that simpler than typing the secret?
I still don’t get the purpose of showing that complex secret in a human-readable form… Can you explain?
Sometimes it is true ![]() In this sense and only if the raw TOTP secret is really needed we could list it (or maybe multiple formats of it) in the “popover” text description:
In this sense and only if the raw TOTP secret is really needed we could list it (or maybe multiple formats of it) in the “popover” text description:
/cc @edoardo_spadoni
Actually the otp key can be found in the user’s home: Find the OTP pin in your terminal
Yes I know, sadly on my, what we call a phone (Note4), when BitWarden open the QRCode reader it result in an impromptu error 239
Personally I’m fine with if the secret code is accessible only via CLI
@stephdl I probably misunderstood but I can’t find any .2fa.secret since 2fa is not activated yet.
True, the key is saved only when enabled