I’d like to change the behavior of the Transparent HTTPS proxy dropping the MITM (Man In The Middle) feature that inspects all the encrypted traffic, substituting it with a new implementation that sniffs only the beginning of the connection to discover the destination website (for filtering purposes).
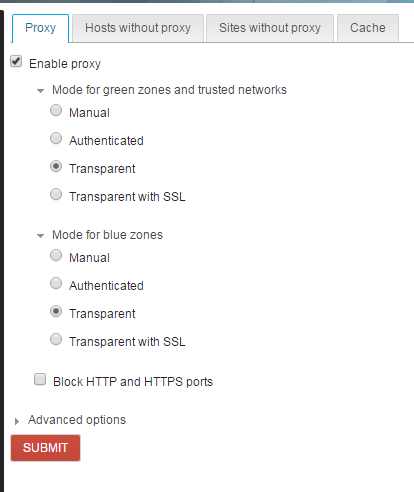
Brief recap: now, when the Web proxy is set to Transparent with SSL, NethServer intercepts traffic on port 443 (HTTPS), connects to the secure web server impersonating the client and decrypts all traffic for inspection before sending it back to the client browser.
This feature is primarily used to discover where a user is going and filter web access. There’s usually no need to look at the whole content of the connection to filter unwanted websites.
This feature can only be used in specific environments because all client browsers need to have a special certificate installed (the biggest drawback). Personally, I will never activate this feature and I will never connect to my bank website through such a proxy.
Finally, all web browser, today, are giving really visible warnings about untrusted certificates and sometimes they block browsing if spoofing is detected.
CentOS 7.3 will soon introduce squid 3.5 which has a new function to intercept an HTTPS connection, called peek and splice.
Basically, it means that we will peek at the beginning of the connection to discover the destination website (and block it if desired) and then let the traffic flow unaltered from the client pc to the secure website.
- No certificate to install on all browsers
- No untrusted certificate warning
- No sniffing on bank account

- Seamless filter of unwanted websites, both HTTP and HTTPS
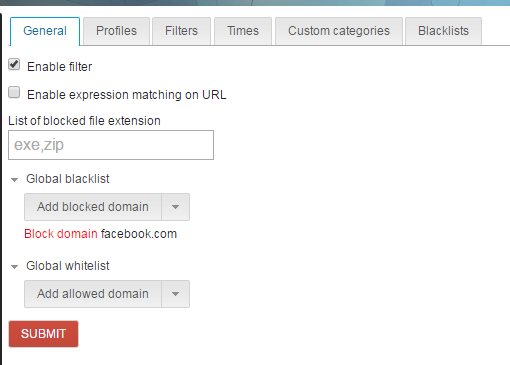
The web UI will not change (only the certificate download button will be removed), the behavior will change under the hood.
Keeping the MITM features as is now plus adding the new peek and splice will need a considerable development effort. Changing the transparent MITM to peek and splice is relatively easy, I plan to release it next week if CentOS releases 7.3.
We will loose a hard-to-use feature, with a lot of limitations (i.e. you can’t install the certificate on smartphones) and that poses privacy problems in exchange for a really transparent feature.
If you think I’ve forgotten a scenario where you absolutely need to be a MITM, please speak up now (unless you’re the NSA). 






 )
)