So, ran a factory reset, and DO get new packages. So this might have been something that is now resolved. I swear to my sanity (for as far as I got it) that I used to get an sssd error about the realm already existing.
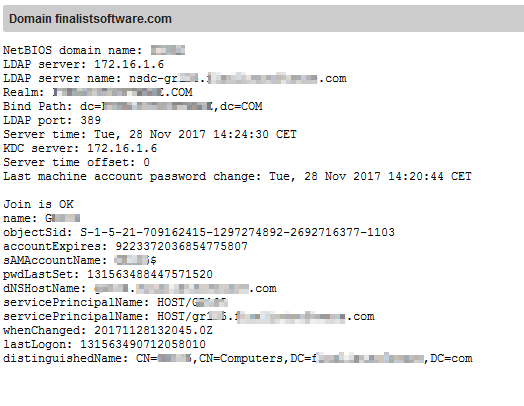
Thanks for the suggestion, it worked wonders … and I feel a bit embarassed that I just days ago said the fine manual contained more then you would expect … only to be referred to it … sorry for not doing my own homework better.
Anyhow, scratch that irritation off my list … now the real issue:
Let’s rejoin the fileserver to the new domain … but wait … what ?? Ah, sanity preserved:
…but by now I’m stubborn, so I just click ‘join’ again:
…whatever … on we go …
[root@fileserver ~]# klist -k
Keytab name: FILE:/etc/krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
2 host/fileserver.mydomain.com@MYDOMAIN.COM
2 host/fileserver@MYDOMAIN.COM
2 host/fileserver.mydomain.com@MYDOMAIN.COM
2 host/fileserver@MYDOMAIN.COM
2 host/fileserver.mydomain.com@MYDOMAIN.COM
2 host/fileserver@MYDOMAIN.COM
2 host/fileserver.mydomain.com@MYDOMAIN.COM
2 host/fileserver@MYDOMAIN.COM
2 host/fileserver.mydomain.com@MYDOMAIN.COM
2 host/fileserver@MYDOMAIN.COM
2 fileserver$@MYDOMAIN.COM
2 fileserver$@MYDOMAIN.COM
2 fileserver$@MYDOMAIN.COM
2 fileserver$@MYDOMAIN.COM
2 fileserver$@MYDOMAIN.COM
3 host/fileserver.mydomain.com@MYDOMAIN.COM
3 host/fileserver@MYDOMAIN.COM
3 host/fileserver.mydomain.com@MYDOMAIN.COM
3 host/fileserver@MYDOMAIN.COM
3 host/fileserver.mydomain.com@MYDOMAIN.COM
3 host/fileserver@MYDOMAIN.COM
3 host/fileserver.mydomain.com@MYDOMAIN.COM
3 host/fileserver@MYDOMAIN.COM
3 host/fileserver.mydomain.com@MYDOMAIN.COM
3 host/fileserver@MYDOMAIN.COM
3 fileserver$@MYDOMAIN.COM
3 fileserver$@MYDOMAIN.COM
3 fileserver$@MYDOMAIN.COM
3 fileserver$@MYDOMAIN.COM
3 fileserver$@MYDOMAIN.COM
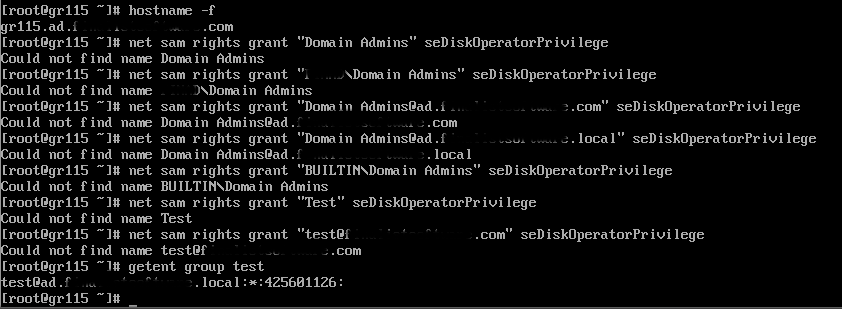
Allas, no luck on setting seDiskOperatorPrivilege yet
[root@fileserver ~]# hostname -f
fileserver.mydomain.com
[root@fileserver ~]# hostname -d
mydomain.com
[root@fileserver ~]# getent group "domain admins"
domain admins@mydomain.com:*:1262600512:administrator@mydomain.com,admin@mydomain.com
[root@fileserver ~]# net sam rights grant "Domain Admins" seDiskOperatorPrivilege
Could not find name Domain Admins
[root@fileserver ~]# net sam rights grant "mydom\Domain Admins" seDiskOperatorPrivilege
Could not find name mydom\Domain Admins
[root@fileserver ~]# net sam rights grant "mydom\\Domain Admins" seDiskOperatorPrivilege
Could not find name mydom\Domain Admins
[root@fileserver ~]# net sam rights grant "MYDOM\domain admins" seDiskOperatorPrivilege
Could not find name MYDOM\domain admins
[root@fileserver ~]# net sam rights grant "domain admins@mydomain.com" seDiskOperatorPrivilege
Could not find name domain admins@mydomain.com
[root@fileserver ~]# net sam rights list seDiskOperatorPrivilege
BUILTIN\Administrators
I can confirm that we can set rights to BUILTIN groups, but these are server-local and for some reason rights do not propogate correctly. When joining a domain, the domain admins should become member of the local server admins. They are not.
What is worse:
[root@domainserver~]# net sam list groups
…yeah, nothing returned.
However:
[root@domainserver~]# net ads group -Uadministrator
Enter administrator's password:
Allowed RODC Password Replication Group
Enterprise Read-Only Domain Controllers
Denied RODC Password Replication Group
Pre-Windows 2000 Compatible Access
Windows Authorization Access Group
Certificate Service DCOM Access
Network Configuration Operators
Terminal Server License Servers
Incoming Forest Trust Builders
Read-Only Domain Controllers
Group Policy Creator Owners
Performance Monitor Users
Cryptographic Operators
Distributed COM Users
Performance Log Users
Remote Desktop Users
Account Operators
Event Log Readers
RAS and IAS Servers
Backup Operators
Domain Controllers
Server Operators
Enterprise Admins
Print Operators
Administrators
Domain Computers
Cert Publishers
DnsUpdateProxy
Domain Admins
Domain Guests
Schema Admins
Domain Users
Replicator
IIS_IUSRS
DnsAdmins
Guests
Users
support
[root@domainserver ~]#
So, that might be a clue as to why I can not use net rpc rights grant on groups it can not find … my knowledge is lacking tho, so I have no clue how samba normally would get these domaingroups. I’m still reading up. Thanks so far!
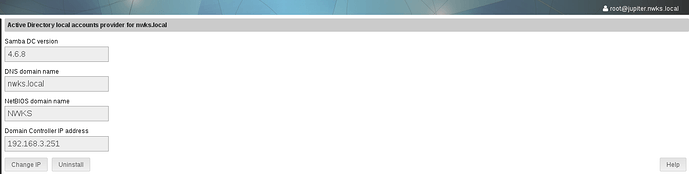
 ), nothing changed from ad perspective.
), nothing changed from ad perspective.