Hi,
downloaded FreeNAS 11 U3 fully motivated at first.
Tried to join FreeNAS to Nethserver again, but no luck.
Via GUI I get certificate error:
error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed (unable to get local issuer certificate), Connect error
Played around with certs for hours importing from Nethserver, tried CSR, tried self-signed cert from FreeNAS on Nethserver with no luck. Tried CA with and without keys, nothing helped.
Then I just tried joining Nethserver AD via samba-tool on FreeNAS cli and it WORKED as member ánd as DC, without any certificate  but I can’t see users or groups from my domain, so I am giving up at this point. My solution for FreeNAS at the moment is disabling strong auth as described earlier in this thread:
but I can’t see users or groups from my domain, so I am giving up at this point. My solution for FreeNAS at the moment is disabling strong auth as described earlier in this thread:
root@freenas:~ # samba-tool domain join cmb.local DC -U admin -W CMB
Finding a writeable DC for domain 'cmb.local'
Found DC nsdc-server.cmb.local
Password for [CMB\admin]:
workgroup is CMB
realm is cmb.local
Adding CN=FREENAS,OU=Domain Controllers,DC=cmb,DC=local
Adding CN=FREENAS,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=cmb,DC=local
Adding CN=NTDS Settings,CN=FREENAS,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=cmb,DC=local
Adding SPNs to CN=FREENAS,OU=Domain Controllers,DC=cmb,DC=local
Setting account password for FREENAS$
Enabling account
Calling bare provision
Looking up IPv4 addresses
Looking up IPv6 addresses
No IPv6 address will be assigned
Setting up secrets.ldb
Setting up the registry
Setting up the privileges database
Setting up idmap db
Setting up SAM db
Setting up sam.ldb partitions and settings
Setting up sam.ldb rootDSE
Pre-loading the Samba 4 and AD schema
A Kerberos configuration suitable for Samba AD has been generated at /var/db/samba4/private/krb5.conf
Provision OK for domain DN DC=cmb,DC=local
Starting replication
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[402/1550] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[804/1550] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[1206/1550] linked_values[0/0]
Schema-DN[CN=Schema,CN=Configuration,DC=cmb,DC=local] objects[1550/1550] linked_values[0/0]
Analyze and apply schema objects
Partition[CN=Configuration,DC=cmb,DC=local] objects[402/1616] linked_values[0/1]
Partition[CN=Configuration,DC=cmb,DC=local] objects[804/1616] linked_values[0/1]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1206/1616] linked_values[0/1]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1608/1616] linked_values[0/1]
Partition[CN=Configuration,DC=cmb,DC=local] objects[1616/1616] linked_values[32/32]
Replicating critical objects from the base DN of the domain
Partition[DC=cmb,DC=local] objects[97/97] linked_values[25/25]
Partition[DC=cmb,DC=local] objects[314/217] linked_values[25/25]
Done with always replicated NC (base, config, schema)
Replicating DC=DomainDnsZones,DC=cmb,DC=local
Partition[DC=DomainDnsZones,DC=cmb,DC=local] objects[41/41] linked_values[0/0]
Replicating DC=ForestDnsZones,DC=cmb,DC=local
Partition[DC=ForestDnsZones,DC=cmb,DC=local] objects[18/18] linked_values[0/0]
Exop on[CN=RID Manager$,CN=System,DC=cmb,DC=local] objects[3] linked_values[0]
Committing SAM database
Sending DsReplicaUpdateRefs for all the replicated partitions
Setting isSynchronized and dsServiceName
Setting up secrets database
Joined domain CMB (SID S-1-5-21-890086496-3770272300-3508276966) as a DC
Then I tried to list the AD users but no luck again, so time to say good night!
root@freenas:~ # wbinfo -u
Error looking up domain users
root@freenas:~ # wbinfo -g
failed to call wbcListGroups: WBC_ERR_DOMAIN_NOT_FOUND
Error looking up domain groups
To delete FreeNAS member computer:
ldbdel --url=/var/lib/samba/private/sam.ldb CN=FREENAS,CN=Computers,DC=cmb,DC=local
To delete FreeNAS DC
ldbdel --url=/var/lib/samba/private/sam.ldb “CN=RID Set,CN=FREENAS,OU=Domain Controllers,DC=cmb,DC=local”
Both commands have to be executed on the NSDC, to get into NSDC do:
systemd-run -M nsdc -t /bin/bash
My sources:
https://doc.freenas.org/11/directoryservice.html
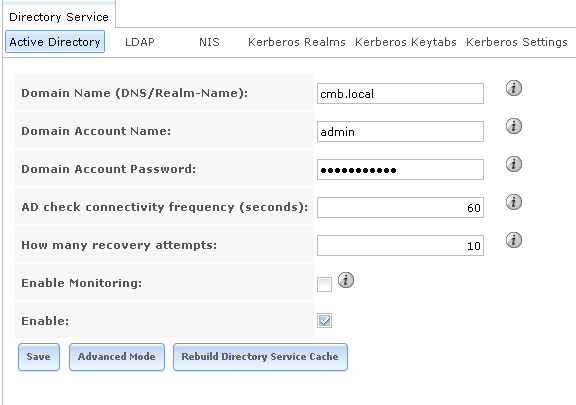
 with this test i can join my freenas to nethserver. now to figure out how to actually enable strong auth for production
with this test i can join my freenas to nethserver. now to figure out how to actually enable strong auth for production 
