I don’t have a lot of experience, but your system may have been compromised through wordpress.
I just found this:
Good Morning!
after I did not find the file that tore down my system, but closed the port in the DSL modem and on the NS, the performance figures are in order again.
After the file “J” but was in the tmp directory and has been diligently trying to receive data and distribute.
I completely deleted the directory and recreated it.
Since then, it’s quiet 
Unfortunately I could not find the file and secure it.
ls - l no indication
even with mc Kommander I saw nothing …
The curious thing, however, was that as soon as the amavisd was switched on and off, everything worked normally, every hour the system load increased by a factor of 1.5 until after about 36 hours the system stopped.
If you turn off the service after a day and turned it on again …
Although it was related to the web server in the aftermath.
My (external) network traffic is now back to normal.
I hope that was it! Thank you all who helped.
Gerald
PS: All give out in beer that helped me, Cheers!
bad news, it continues - aaarrgggg
root@openzwo tmp]# lsof -p 8005
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
j 8005 apache cwd DIR 8,1 125 9166464 /tmp/logs/.skg
j 8005 apache rtd DIR 8,1 4096 64 /
j 8005 apache txt REG 8,1 3876568 9166474 /tmp/logs/.skg/j
j 8005 apache mem REG 8,1 111080 26293471 /usr/lib64/libresolv-2.17.so
j 8005 apache mem REG 8,1 27776 25864019 /usr/lib64/libnss_dns-2.17.so
j 8005 apache mem REG 8,1 2127336 25166636 /usr/lib64/libc-2.17.so
j 8005 apache mem REG 8,1 164112 25752629 /usr/lib64/ld-2.17.so
j 8005 apache mem REG 8,1 62184 26293453 /usr/lib64/libnss_files-2.17.so
j 8005 apache 0r CHR 1,3 0t0 1028 /dev/null
j 8005 apache 1w CHR 1,3 0t0 1028 /dev/null
j 8005 apache 2w CHR 1,3 0t0 1028 /dev/null
j 8005 apache 3u a_inode 0,9 0 5901 [eventfd]
j 8005 apache 4u a_inode 0,9 0 5901 [eventpoll]
j 8005 apache 5u a_inode 0,9 0 5901 [timerfd]
j 8005 apache 6r FIFO 0,8 0t0 1010306 pipe
j 8005 apache 7w FIFO 0,8 0t0 1010306 pipe
j 8005 apache 8u IPv4 1203214 0t0 TCP openzwo.fritz.box:51692->static.12.31.201.138.clients.your-server.de:dec-notes (ESTABLISHED)
j 8005 apache 14u sock 0,7 0t0 1379991 protocol: TCP
[root@openzwo tmp]#
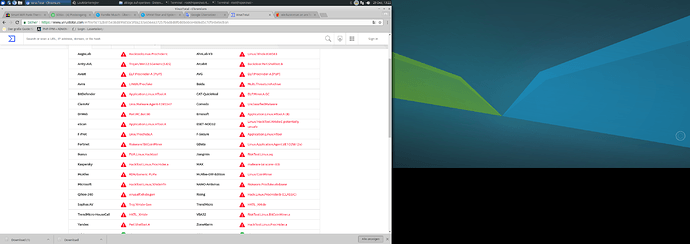
So I saved the directory and let it analyze at virusTotal.
Looks very bad …
Now the question of all questions what can I do to get rid of these things?
and it runs a crontab of the thing starts …
[root@openzwo etc]# for user in $(cut -f1 -d: /etc/passwd); do crontab -u $user -l; done
no crontab for root
no crontab for bin
no crontab for daemon
no crontab for adm
no crontab for lp
no crontab for sync
no crontab for shutdown
no crontab for halt
no crontab for mail
no crontab for operator
no crontab for games
no crontab for ftp
no crontab for nobody
no crontab for systemd-bus-proxy
no crontab for systemd-network
no crontab for dbus
no crontab for polkitd
* * * * * /tmp/logs/.skg/upd >/dev/null 2>&1
no crontab for postfix
no crontab for sshd
no crontab for tss
no crontab for chrony
no crontab for sssd
no crontab for srvmgr
no crontab for tcpdump
no crontab for memcached
no crontab for clamupdate
no crontab for rpc
no crontab for unbound
no crontab for ejabberd
no crontab for mysql
no crontab for dovecot
no crontab for dovenull
no crontab for sogo
no crontab for openvpn
no crontab for rpcuser
no crontab for nfsnobody
no crontab for amavis
no crontab for vmail
no crontab for spfd
no crontab for ddclient
no crontab for shellinabox
no crontab for colord
no crontab for avahi
no crontab for saslauth
no crontab for radvd
no crontab for qemu
no crontab for urbackup
no crontab for davfs2
no crontab for squid
no crontab for ufdb
no crontab for postgres
no crontab for tomcat
no crontab for radiusd
no crontab for redis
no crontab for c-icap
[root@openzwo etc]#There are 2 approaches, trying to clean your system or complete reinstall. In your case, having much threats, I tend more to reinstall to be sure to have a clean system.
EDIT:
Ooops, I just recognized, it’s only one threat, so you may google the virus names and find some info about the malware and hopefully how to get rid of it.
This means apache’s crontab. Unless you fix your website you will be infected again.
OK, such a nice gift!
I have now deleted the crontab “Apache” and disabled the two virtual hosts.
What options are there to check the system?
Currently I have carried out the following steps:
- deleted the data and directories in tmp / …
- Crontab “Apache” deleted
- reboot
- (all) virtual host disabled
- reboot
The Wordpress directory packs and orignale deleted.
Virus scanner ran through again but as always no result.
So far, everything looks good now.
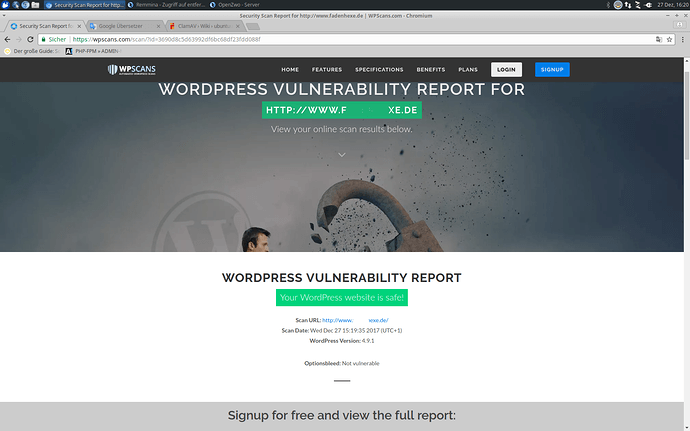
It seems a Monero miner, with similarities with the one used in a Massive Cryptomining Campaign Targeting WordPress Sites.
More info about this mining server at Threatminer, Threatcrowd, herdProtect
Some open ports: 22 (OpenSSH_6.7p1 Debian-5+deb8u3), 80, 443, 3333, 3334, 3335, 3336, 5555, 8080.
IP associated to mine.moneropool.com
The malware could have gone through due to vulnerable/misconfigured wordpress plugins, redis, apache struts, tomcat. In your case maybe just WordPress…
There are malware versions for Windows and Linux systems, at least.
ClamAV with unofficial signatures would have detected the malware files on disk but not on memory.
Analysis of some of the malware found (check also external references):
- 63210b24f42c05b2c5f8fd62e98dba6de45c7d751a2e55700d22983772886017
- d9791f4dfd903bf3c7c5258ac4ae92df11fc37c3b1749e15f173c1aeb6fafb67
Some tips (like finding recently modified files, inspect database and httpd access_log logs…):
- How to Tell if Your PHP Site has been Hacked or Compromised and Steps to Take When you Know your PHP Site has been Hacked
- Repair a hacked wordpress (beware of malformed code/commands)
- Investigating Compromised Servers
General information about WordPress security measures:
- An Introduction to WordPress Security
- Hardening WordPress
- WPHardening (python script to automate it)