Before:
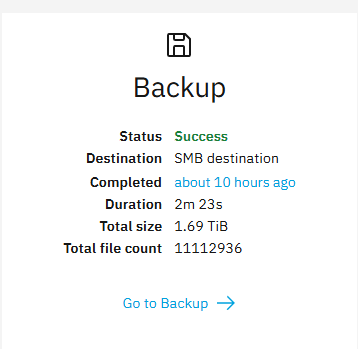
After:
Based on the time taken and only a very small increase in the number of files, I’d like to say it’s working.
Let me see if I can take a look at the backed up data to confirm.
Cheers.
Before:

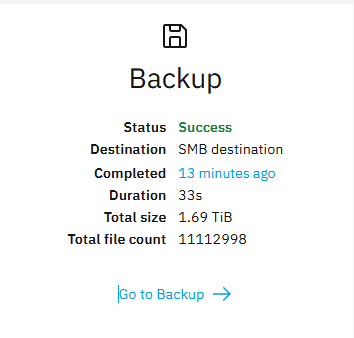
After:

Based on the time taken and only a very small increase in the number of files, I’d like to say it’s working.
Let me see if I can take a look at the backed up data to confirm.
Cheers.
You can test also that only the administrator of ldap is the admin any other ldap user is a simple user
I mean in the cgi user interface of backuppc
Not quite sure what you’re asking. I have this setting:
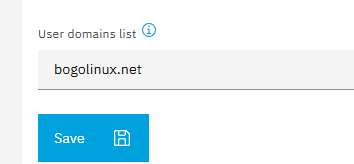
Only users declared to NS8 can login to the BackupPC interface. And all users have full control.
I see this in BackupPC:

But I can’t use backuppc as the user to login with as I don’t have a password for it.
Cheers.
Use the stable version. Not the testing version
Version 1.0.2
I don’t know how to switch back.
But previous to installing your new version, it was the same as I described above. I could only log in via the UI with an NS8 defined user and they had full control.
Cheers.
Go to about page in the module and display the version you use ![]()
In the upgrade you should have 1.0.2 offered if not
api-cli run update-module --data ‘{“module_url”:“ghcr.io/stephdl/backuppc:1.0.2",“instances”:[“backuppc1”],"force”:true}’
It includes the ldap and the no data backup fix
Nope, no update offered.
[root@ns8 ~]# api-cli run update-module --data ‘{“module_url”:“ghcr.io/stephdl/backuppc:1.0.2",“instances”:[“backuppc2”],"force”:true}’
Warning: using user "cluster" credentials from the environment
Traceback (most recent call last):
File "/usr/local/bin/api-cli", line 246, in <module>
exit_code = command(args)
^^^^^^^^^^^^^
File "/usr/local/bin/api-cli", line 122, in run_command
data = json.loads(args.data)
^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib64/python3.11/json/__init__.py", line 346, in loads
return _default_decoder.decode(s)
^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib64/python3.11/json/decoder.py", line 337, in decode
obj, end = self.raw_decode(s, idx=_w(s, 0).end())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib64/python3.11/json/decoder.py", line 355, in raw_decode
raise JSONDecodeError("Expecting value", s, err.value) from None
json.decoder.JSONDecodeError: Expecting value: line 1 column 1 (char 0)
[root@ns8 ~]#
Cheers.
api-cli run update-module --data '{"module_url":"ghcr.io/stephdl/backuppc:1.0.2","instances":["backuppc1"],"force":true}'
badly formatted by discourse, try again
Using LDAP authentication, you have to create a user called “backuppc” and use that to gain administrative privileges, otherwise you are a “normal” user who doesn’t see anything unless the BackupPC administrator has authorised you. The LDAP user “admin” is still treated as a “normal” user.
Using Basic Authentication, any user name you use is granted Administrator rights in BackupPC.
Cheers.
OffTopic: Chrome is a PiA to use to test this as it’s not a simple matter to delete cookies for a single site anymore and BackupPC doesn’t have a logoff function.
Normally by upgrading to 1.0.2 you should see also the administrator in the field of the cgi admin ?
You mean as an option here:
Then no.
If not, exactly where. To logon to the UI is a simple user/password prompt.
Cheers.

Normally administrator is also listed
OK, yes it appears to have done that now:

But that’s locking the keys inside the safe.
You can’t see that until you have logged in, which requires either an LDAP user called backuppc or any simple user/password name. OK, maybe administrator would work now (if it was documented), except the built in administrator account is capitalised and disabled, so won’t have a password set.
Cheers.
Well a bit lost. When you create an account provider the administrator user is the default and unique member, so use it ![]()
Ha, you mean the one I set waaaay back in NS7.x (or maybe even before that) and haven’t had to use/touch since then.
OK, after updating it’s password it appears to work.
But then why only the LDAP administrator. Why not the NS8 administrator that’s already an account in LDAP as well. That would make more sense (at least to me).
Cheers.
Please test to create a samba ad and an openldap account provider. The first admin user and member of domain admins is administrator.
If you want more admin for backuppc, create them in the ldap and add them to backuppc in the cgiadmin field