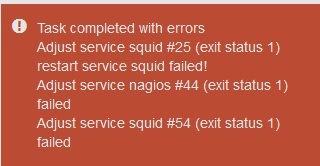
hi,
squid.conf
# Uncomment this to enable debug
#debug_options ALL,1 33,2 28,9
# Sites not cached
acl no_cache dstdomain "/etc/squid/acls/no_cache.acl"
no_cache deny no_cache
# Allow access from green and trusted networks.
acl localnet src 10.39.x.x/21
acl localnet_dst src 10.39.x.x/21
# Safe ports
acl SSL_ports port 443
acl SSL_ports port 980 # httpd-admin (server-manager)
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl Safe_ports port 980 # httpd-admin (server-manager)
acl CONNECT method CONNECT
#
# 20acl_00_portscustom
#
# Authentication required
# GSSAPI auth in ADS mode
auth_param negotiate program /usr/lib64/squid/negotiate_kerberos_auth -i
auth_param negotiate children 10
auth_param negotiate keep_alive on
# BASIC PAM auth (fallback)
auth_param basic program /usr/lib64/squid/basic_pam_auth
auth_param basic children 5
auth_param basic realm xxx
auth_param basic credentialsttl 1 hours
auth_param basic casesensitive on
acl authenticated proxy_auth REQUIRED
# Allow access from localhost
http_access allow localhost
# Deny requests to certain unsafe ports
http_access deny !Safe_ports
# Deny CONNECT to other than secure SSL ports
http_access deny CONNECT !SSL_ports
# Only allow cachemgr access from localhost
http_access allow localhost manager
http_access deny manager
#
# Skip URL rewriter for local addresses
#
acl self dst 10.39.x.xx
acl self_port port 80
acl self_port port 443
url_rewrite_access deny self localnet self_port
# Authentication required on green and trusted networks
http_access allow localnet authenticated
# And finally deny all other access to this proxy
http_access deny all
cache_mem 256 MB
# Enable disk cache
minimum_object_size 0 KB
maximum_object_size 4096 KB
cache_dir aufs /var/spool/squid 200 16 256
# Leave coredumps in the first cache dir
coredump_dir /var/spool/squid
#
# Add any of your own refresh_pattern entries above these.
#
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
refresh_pattern ([^.]+.|)(download|(windows|)update|).(microsoft.|)com/.*\.(cab|exe|msi|msp) 4320 100% 43200 reload-into-ims
# Always enable manual proxy
http_port 3128
# Enable squidGuard
url_rewrite_program /usr/sbin/ufdbgclient -l /var/log/squid
url_rewrite_children 20 startup=5 idle=5 concurrency=0
url_rewrite_extras "%>a/%>A %un %>rm bump_mode=%ssl::bump_mode sni=\"%ssl::>sni\" referer=\"%{Referer}>h\""
# Hide client ip #
forwarded_for delete
# Turn off via header #
via off
# Deny request for original source of a request
follow_x_forwarded_for deny all
# privacy experience
request_header_access X-Forwarded-For deny all
request_header_access From deny all
request_header_access Referer deny all
request_header_access User-Agent deny all
#
# 90options
#
forward_max_tries 25
shutdown_lifetime 1 seconds
buffered_logs on
max_filedesc 16384
logfile_rotate 0
#
# 90squidclamav
#
and ufdbGuard.conf
logdir "/var/ufdbguard/logs"
dbhome "/var/squidGuard/blacklists"
squid-version "3.5"
analyse-uncategorised-urls off
upload-crash-reports off
# slow replies when reloading db to decrease the number of passed urls
url-lookup-delay-during-database-reload on
logblock on
# Always strip domain from squid username
strip-domain-from-username on
redirect-https "10.39.x.x:443"
category "clothing" {
domainlist /var/squidGuard/blacklists/clothing/domains
}
category "files" {
expressionlist /var/squidGuard/blacklists/custom/files/expressions
}
category "pets" {
domainlist /var/squidGuard/blacklists/pets/domains
}
category "aggressive" {
domainlist /var/squidGuard/blacklists/aggressive/domains
}
category "violence" {
domainlist /var/squidGuard/blacklists/violence/domains
}
category "onlineauctions" {
domainlist /var/squidGuard/blacklists/onlineauctions/domains
}
category "mixed_adult" {
domainlist /var/squidGuard/blacklists/mixed_adult/domains
}
category "adult" {
domainlist /var/squidGuard/blacklists/adult/domains
}
category "gambling" {
domainlist /var/squidGuard/blacklists/gambling/domains
}
category "kidstimewasting" {
domainlist /var/squidGuard/blacklists/kidstimewasting/domains
}
category "ringtones" {
domainlist /var/squidGuard/blacklists/ringtones/domains
}
category "ger_ok" {
domainlist /var/squidGuard/blacklists/custom/ger_ok/domains
}
category "dating" {
domainlist /var/squidGuard/blacklists/dating/domains
}
category "reaffected" {
domainlist /var/squidGuard/blacklists/reaffected/domains
}
category "personalfinance" {
domainlist /var/squidGuard/blacklists/personalfinance/domains
}
category "gardening" {
domainlist /var/squidGuard/blacklists/gardening/domains
}
category "socialnetworking" {
domainlist /var/squidGuard/blacklists/socialnetworking/domains
}
category "hacking" {
domainlist /var/squidGuard/blacklists/hacking/domains
}
category "games" {
domainlist /var/squidGuard/blacklists/games/domains
}
category "updatesites" {
domainlist /var/squidGuard/blacklists/updatesites/domains
}
category "ecommerce" {
domainlist /var/squidGuard/blacklists/ecommerce/domains
}
category "shopping" {
domainlist /var/squidGuard/blacklists/shopping/domains
}
category "whitelist" {
domainlist /var/squidGuard/blacklists/whitelist/domains
}
category "onlinepayment" {
domainlist /var/squidGuard/blacklists/onlinepayment/domains
}
category "mobile-phone" {
domainlist /var/squidGuard/blacklists/mobile-phone/domains
}
category "weather" {
domainlist /var/squidGuard/blacklists/weather/domains
}
category "weapons" {
domainlist /var/squidGuard/blacklists/weapons/domains
}
category "sexuality" {
domainlist /var/squidGuard/blacklists/sexuality/domains
}
category "sports" {
domainlist /var/squidGuard/blacklists/sports/domains
}
category "sexual_education" {
domainlist /var/squidGuard/blacklists/sexual_education/domains
}
category "webmail" {
domainlist /var/squidGuard/blacklists/webmail/domains
}
category "childcare" {
domainlist /var/squidGuard/blacklists/childcare/domains
}
category "radio" {
domainlist /var/squidGuard/blacklists/radio/domains
}
category "dialers" {
domainlist /var/squidGuard/blacklists/dialers/domains
}
category "financial" {
domainlist /var/squidGuard/blacklists/financial/domains
}
category "vacation" {
domainlist /var/squidGuard/blacklists/vacation/domains
}
category "searchengines" {
domainlist /var/squidGuard/blacklists/searchengines/domains
}
category "audio-video" {
domainlist /var/squidGuard/blacklists/audio-video/domains
}
category "ads" {
domainlist /var/squidGuard/blacklists/ads/domains
expressionlist /var/squidGuard/blacklists/ads/expressions
}
category "frencheducation" {
domainlist /var/squidGuard/blacklists/frencheducation/domains
}
category "spyware" {
domainlist /var/squidGuard/blacklists/spyware/domains
}
category "medical" {
domainlist /var/squidGuard/blacklists/medical/domains
}
category "drugs" {
domainlist /var/squidGuard/blacklists/drugs/domains
}
category "virusinfected" {
domainlist /var/squidGuard/blacklists/virusinfected/domains
}
category "jewelry" {
domainlist /var/squidGuard/blacklists/jewelry/domains
}
category "government" {
domainlist /var/squidGuard/blacklists/government/domains
}
category "builtin" {
domainlist /var/squidGuard/blacklists/custom/builtin/domains
expressionlist /var/squidGuard/blacklists/custom/builtin/expressions
}
category "instantmessaging" {
domainlist /var/squidGuard/blacklists/instantmessaging/domains
}
category "filehosting" {
domainlist /var/squidGuard/blacklists/filehosting/domains
}
category "onlinegames" {
domainlist /var/squidGuard/blacklists/onlinegames/domains
}
category "beerliquorsale" {
domainlist /var/squidGuard/blacklists/beerliquorsale/domains
}
category "sportnews" {
domainlist /var/squidGuard/blacklists/sportnews/domains
}
category "warez" {
domainlist /var/squidGuard/blacklists/warez/domains
}
category "naturism" {
domainlist /var/squidGuard/blacklists/naturism/domains
}
category "phishing" {
domainlist /var/squidGuard/blacklists/phishing/domains
}
category "nh_blacklist" {
domainlist /var/squidGuard/blacklists/custom/blacklist/domains
}
category "artnudes" {
domainlist /var/squidGuard/blacklists/artnudes/domains
}
category "beerliquorinfo" {
domainlist /var/squidGuard/blacklists/beerliquorinfo/domains
}
category "proxy" {
domainlist /var/squidGuard/blacklists/proxy/domains
}
category "culinary" {
domainlist /var/squidGuard/blacklists/culinary/domains
}
category "entertainment" {
domainlist /var/squidGuard/blacklists/entertainment/domains
}
category "antispyware" {
domainlist /var/squidGuard/blacklists/antispyware/domains
}
category "jobsearch" {
domainlist /var/squidGuard/blacklists/jobsearch/domains
}
category "marketingware" {
domainlist /var/squidGuard/blacklists/marketingware/domains
}
category "mail" {
domainlist /var/squidGuard/blacklists/mail/domains
}
category "porn" {
domainlist /var/squidGuard/blacklists/porn/domains
expressionlist /var/squidGuard/blacklists/porn/expressions
}
category "religion" {
domainlist /var/squidGuard/blacklists/religion/domains
}
category "ad-block" {
domainlist /var/squidGuard/blacklists/custom/ad-block/domains
}
category "hygiene" {
domainlist /var/squidGuard/blacklists/hygiene/domains
}
category "blog" {
domainlist /var/squidGuard/blacklists/blog/domains
}
category "chat" {
domainlist /var/squidGuard/blacklists/chat/domains
}
category "nh_whitelist" {
domainlist /var/squidGuard/blacklists/custom/whitelist/domains
}
category "banking" {
domainlist /var/squidGuard/blacklists/banking/domains
}
category "cellphones" {
domainlist /var/squidGuard/blacklists/cellphones/domains
}
category "verisign" {
domainlist /var/squidGuard/blacklists/verisign/domains
}
category "cleaning" {
domainlist /var/squidGuard/blacklists/cleaning/domains
}
category "homerepair" {
domainlist /var/squidGuard/blacklists/homerepair/domains
}
category "news" {
domainlist /var/squidGuard/blacklists/news/domains
}
category "security" {
cacerts "/var/ufdbguard/blacklists/security/cacerts"
option enforce-https-with-hostname off
option enforce-https-official-certificate off
option allow-skype-over-https on
option allow-gtalk-over-https on
option allow-yahoomsg-over-https on
option allow-aim-over-https on
option allow-fb-chat-over-https on
option allow-citrixonline-over-https on
option allow-anydesk-over-https on
option allow-teamviewer-over-https on
option allow-unknown-protocol-over-https on
option https-prohibit-insecure-sslv2 off
option https-prohibit-insecure-sslv3 off
}
src src_pippo {
user "it_user1"
}
acl {
# Profile: pippo
src_pippo {
pass !security nh_whitelist !nh_blacklist !in-addr !files !builtin all
}
default {
pass !security nh_whitelist !nh_blacklist !in-addr !files !builtin "ger_ok" none
redirect http://10.39.x.x/cgi-bin/nethserver-block.cgi?clientaddr=%a&clientname=%n&clientident=%i&srcclass=%s&targetgroup=%t&url=%u
}
}
thanks
bye
Andrea