Here are some infos about shorewall and PPTP:
Hi @filippo_carletti, thanks for your reply, this command is only for eth0, right?
Nethserver have this config:
green: eth0 ip 192.168.0.1
red: eth1 ip 127.0.0.1
the commands FOR GREEN is:
iptables -t nat -A PREROUTING -i eth0 -p gre -j DNAT --to-destination 192.168.0.1
the commands FOR RED is:
iptables -t nat -A PREROUTING -i eth1 -p gre -j DNAT --to-destination 127.0.0.1
something is missing, for example, the inverse command, du u understand?
Regards,
Sgolastra.Hi @LayLow thank you for your reply, in the past have tried configuration suggested by you, but it does not work like that, however, thanks for your help, thank very much.
Sgolastra
Hi @mrmarkuz, thank you for reply ;-), i have read and test with a ref. of page by the PPTP Server Running Behind your Firewall.
My net area is an example:
green eth0 as ip andress 192.1.1.1 with alias ip 192.3.3.1
red eth1 192.0.0.1
winzoz pptp server test is: 192.3.3.100
external ip: 127.0.0.1
I have setup in this mode:
/etc/shorewall/rules:
######################################################################################################################################################################################
#ACTION SOURCE DEST PROTO DEST SOURCE ORIGINAL RATE USER/ MARK CONNLIMIT TIME HEADERS SWITCH
PORT PORT(S) DEST LIMIT GROUP
#SECTION ALL
SECTION ESTABLISHED
?SECTION ESTABLISHED
DNAT net loc:192.3.3.100 tcp 1723 - 127.0.0.1
DNAT net loc:192.3.3.100 47 - - 127.0.0.1
SECTION RELATED
?SECTION RELATED
SECTION NEW
?SECTION NEW
…
when i restart service shorewall the error is:
Starting shorewall: ERROR: NAT rules are only allowed in the NEW section /etc/shorewall/rules (line 29)
[FAILED]
can u help me please?
Thanks in advance,
Sgolastra.
Opss  when i post i celebrate the error and now understand , now i test
when i post i celebrate the error and now understand , now i test 
Hi @mrmarkuz i just tested in this mode…
Scenario:
green eth0 as ip andress 192.1.1.1 with alias ip 192.3.3.1
red eth1 192.0.0.1
winzoz pptp server test is: 192.3.3.100
external ip: 127.0.0.1
/etc/shorewall/rules :
#ACTION SOURCE DEST PROTO DEST PORT(S)
DNAT net loc:192.3.3.100 tcp 1723
DNAT net loc:192.3.3.100 47
in – etc/shorewall/masq:
#INTERFACE SUBNET ADDRESS PROTO
eth0 192.3.3.0/24 192.0.0.1 47
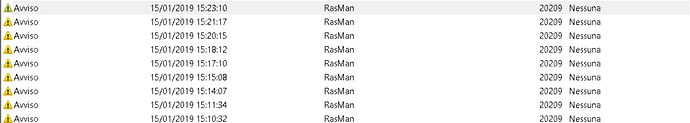
the service restart correctly, but when i try to connect by pptp vpn client, the error is:
2019-01-15 15:20:50 Using interface ppp0
2019-01-15 15:20:50 Connect: ppp0 <–> socket[34:17]
2019-01-15 15:20:54 PPTP port-mapping for en1, interfaceIndex: 0, Protocol: None, Private Port: 0, Public Address: 0, Public Port: 0, TTL: 0.
2019-01-15 15:20:54 PPTP port-mapping for en1 inconsistent. is Connected: 1, Previous interface: 4, Current interface 0
**19-01-15 15:21:22 LCP: timeout sending Config-Requests
2019-01-15 15:21:22 Connection terminated.
2019-01-15 15:21:22 PPTP disconnecting…
2019-01-15 15:21:22 PPTP clearing port-mapping for en1
2019-01-15 15:21:22 PPTP disconnected
where I wrong?
Thanks,
Regard,
Daniele
Is there a typo, you commented out the eth0 line?
Could it be that you need a static route on your nethserver for network 192.3.3.0 to your internal pptp server address?
Did you mask the addresses to keep them secret? External IP is 127.0.0.1?
Hi @mrmarkuz no the error is the same in my previous post:
the service restart correctly, but when i try to connect by pptp vpn client, the error is:
2019-01-15 15:20:50 Using interface ppp0
2019-01-15 15:20:50 Connect: ppp0 <–> socket[34:17]
2019-01-15 15:20:54 PPTP port-mapping for en1, interfaceIndex: 0, Protocol: None, Private Port: 0, Public Address: 0, Public Port: 0, TTL: 0.
2019-01-15 15:20:54 PPTP port-mapping for en1 inconsistent. is Connected: 1, Previous interface: 4, Current interface 0
**19-01-15 15:21:22 LCP: timeout sending Config-Requests
2019-01-15 15:21:22 Connection terminated.
2019-01-15 15:21:22 PPTP disconnecting…
2019-01-15 15:21:22 PPTP clearing port-mapping for en1
2019-01-15 15:21:22 PPTP disconnected

Thanks,
regards,
SGOLASTRA
Here are some informations for diagnosing the problem, it seems GRE is not handled correctly:
FYI http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/868-cisco-router-gre-ipsec.html
L2TP or OpenVPN could not be used as alternatives for Windows?
I could reproduce this issue by connecting to a server that does not exist. Please check if the VPN host is set correctly and the VPN port 1723 is open/reachable.
I used Nethserver 7 as firewall router and just forwarded port 1723 to my Windows server 2016 that provides a PPTP VPN server. I had to set VPN security to MSCHAPv2 only on the Windows server and on the Ubuntu 18.04 client I had to activate “MPPE”. Now VPN connection via mobile phone hotspot from outside is working.
No GRE forwarding or changes in shorewall are needed because a PPTP and GRE firewall helper module should be loaded.
I am not using any alias IP, maybe this is a problem?
NS6 should support GRE too:
[root@neth69 ~]# lsmod | grep pptp
nf_nat_pptp 4365 0
nf_nat_proto_gre 2772 1 nf_nat_pptp
nf_conntrack_pptp 11462 1 nf_nat_pptp
nf_conntrack_proto_gre 6619 1 nf_conntrack_pptp
nf_nat 22708 12 ipt_REDIRECT,ipt_NETMAP,ipt_MASQUERADE,nf_nat_tftp,nf_nat_sip,nf_nat_pptp,nf_nat_proto_gre,nf_nat_irc,nf_nat_h323,nf_nat_ftp,nf_nat_amanda,iptable_nat
nf_conntrack 79601 35 xt_connlimit,ipt_MASQUERADE,ipt_CLUSTERIP,nf_nat_tftp,nf_nat_snmp_basic,nf_conntrack_snmp,nf_nat_sip,nf_nat_pptp,nf_nat_irc,nf_nat_h323,nf_nat_ftp,nf_nat_amanda,nf_conntrack_amanda,nf_conntrack_sane,nf_conntrack_tftp,nf_conntrack_sip,nf_conntrack_proto_udplite,nf_conntrack_proto_sctp,nf_conntrack_pptp,nf_conntrack_proto_gre,nf_conntrack_netlink,nf_conntrack_netbios_ns,nf_conntrack_broadcast,nf_conntrack_irc,nf_conntrack_h323,nf_conntrack_ftp,xt_helper,xt_conntrack,xt_CONNMARK,xt_connmark,iptable_nat,nf_nat,nf_conntrack_ipv4,nf_conntrack_ipv6,xt_state
Hi @mrmarkuz thanks for your support, before this post i have test in lan vpn pptp client (mac osx) and server (winzoz 2016), in this case i can connect correctly, up and running, the problems is wan to lan.
When i read the your last message, i see the winzoz log files, the error is:
"A connection has been established between the server and the VPN client 127.0.0.1, but the VPN connection can not be completed. The most common cause of this problem is a firewall or a router between the server and the VPN client that is not configured to allow the transmission of Generic Routing Encapsulation (GRE) packets (protocol 47)."
I’m no using nethserver 7.0, maybe this is a problem? 
Thanks,
SGOLASTRA
Anyone of team manager can suggest me solutions?
Do you have another router in front of your Nethserver? Maybe it’s blocking the GRE protocol. In my router I set the Nethserver as DMZ host.
I am going to test it with NS6 but I assume it will work…
EDIT:
Tested following scenario:
Ubuntu PPTP VPN client -> WWW -> Cable router (using NS 7.6 as DMZ host) -> 192.168.0.0/24 -> NS7 (with port 1723 forwarded to NS 6.10) -> 192.168.1.0/24 -> NS6 (with port 1723 forwarded to Windows Server 2016) -> 192.168.2.0/24 -> Windows Server 2016 PPTP VPN server -> 192.168.11.0/24 (PPTP VPN network)
I can ping the Windows Server 2016 PPTP VPN IP 192.168.11.1 from the Ubuntu client via PPTP VPN.
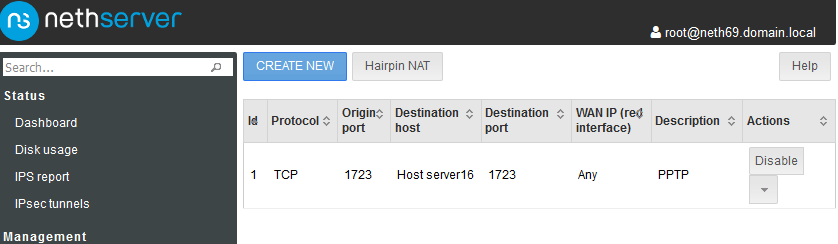
GRE is definitely working on Nethserver 6 & 7. Only configuration to do is forwarding port 1723:
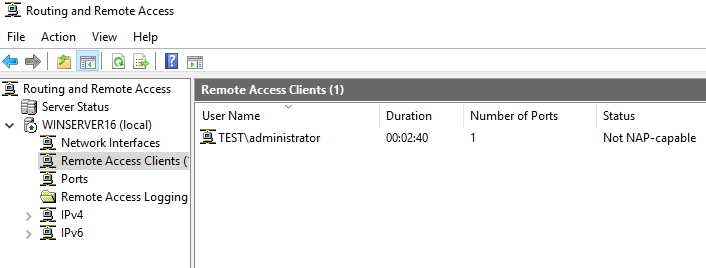
Windows Server notices the client:
Maybe ask the provider if GRE is supported?