I’m going to guess that the answer lies in attribute mapping–that the right user attributes need to be presented to Nextcloud, with the appropriate contents. sAMAccountName is one that is probably going to be relevant.
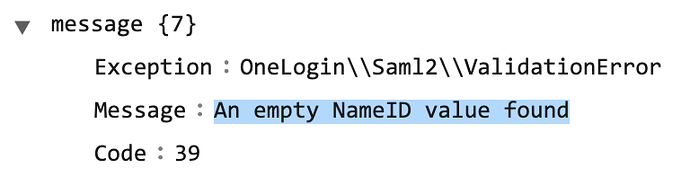
heres the logfile from nextcloud incase it helps anyone else
{“reqId”:“YNpuuHPaOBCYzmeBuQkdEwAAABU”,“level”:2,“time”:“2021-06-29T00:52:08+00:00”,“remoteAddr”:“10.1.1.1”,“user”:"–",“app”:“filesystem”,“method”:“POST”,“url”:"/index.php/apps/user_saml/saml/acs",“message”:“Storage wrapper ‘sharepermissions’ was not registered via the ‘OC_Filesystem - preSetup’ hook which could cause potential problems.”,“userAgent”:“Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36”,“version”:“21.0.2.1”}
{“reqId”:“YNpuuHPaOBCYzmeBuQkdEwAAABU”,“level”:3,“time”:“2021-06-29T00:52:08+00:00”,“remoteAddr”:“10.1.1.1”,“user”:"–",“app”:“index”,“method”:“POST”,“url”:"/index.php/apps/user_saml/saml/acs",“message”:{“Exception”:“OneLogin\Saml2\ValidationError”,“Message”:“An empty NameID value found”,“Code”:39,“Trace”:[{“file”:"/usr/share/nextcloud/apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Response.php",“line”:678,“function”:“getNameIdData”,“class”:“OneLogin\Saml2\Response”,“type”:"->",“args”:[]},{“file”:"/usr/share/nextcloud/apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Auth.php",“line”:240,“function”:“getNameId”,“class”:“OneLogin\Saml2\Response”,“type”:"->",“args”:[]},{“file”:"/usr/share/nextcloud/apps/user_saml/lib/Controller/SAMLController.php",“line”:311,“function”:“processResponse”,“class”:“OneLogin\Saml2\Auth”,“type”:"->",“args”:[“ONELOGIN_120245401ec1f1a46cef9131e31943410ebc912b”]},{“file”:"/usr/share/nextcloud/lib/private/AppFramework/Http/Dispatcher.php",“line”:218,“function”:“assertionConsumerService”,“class”:“OCA\User_SAML\Controller\SAMLController”,“type”:"->",“args”:[]},{“file”:"/usr/share/nextcloud/lib/private/AppFramework/Http/Dispatcher.php",“line”:127,“function”:“executeController”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:"->",“args”:[{“class”:“OCA\User_SAML\Controller\SAMLController”},“assertionConsumerService”]},{“file”:"/usr/share/nextcloud/lib/private/AppFramework/App.php",“line”:157,“function”:“dispatch”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:"->",“args”:[{“class”:“OCA\User_SAML\Controller\SAMLController”},“assertionConsumerService”]},{“file”:"/usr/share/nextcloud/lib/private/Route/Router.php",“line”:302,“function”:“main”,“class”:“OC\AppFramework\App”,“type”:"::",“args”:[“OCA\User_SAML\Controller\SAMLController”,“assertionConsumerService”,{“class”:“OC\AppFramework\DependencyInjection\DIContainer”},{"_route":“user_saml.SAML.assertionConsumerService”}]},{“file”:"/usr/share/nextcloud/lib/base.php",“line”:993,“function”:“match”,“class”:“OC\Route\Router”,“type”:"->",“args”:["/apps/user_saml/saml/acs"]},{“file”:"/usr/share/nextcloud/index.php",“line”:37,“function”:“handleRequest”,“class”:“OC”,“type”:"::",“args”:[]}],“File”:"/usr/share/nextcloud/apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Response.php",“Line”:641,“CustomMessage”:"–"},“userAgent”:“Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36”,“version”:“21.0.2.1”}
i agree im guessing its not pushing the correct mapping as you said which hopefully should be easy to fix with the correct mapping im also getting a similar error with Education Perfect which i think seems to support that
I don’t have a Neth system with AD up to test right now, but instead of using uid as the attribute, try cn.
Sorry but for clarification which attribute section are you suggesting to change
I’m suggesting, in this step, to replace uid with cn.
See also:
a tool one of the integration teams over at ep told me about called saml message decoder
@Shane_Treweek, I was able to make it work with Nextcloud under AD by setting these Exported Variables (under General Parameters, Authentication parameters, LDAP parameters, Exported variables):
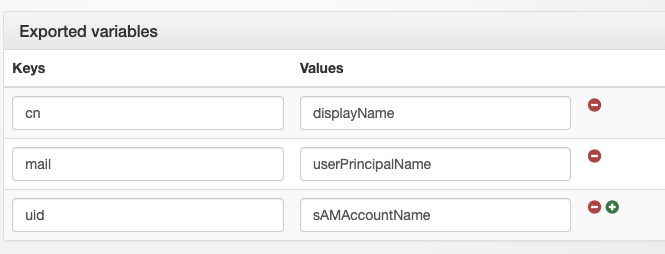
And where I’d told you to make the change from uid to cn, change it back to uid.
Let me know if this works for you–if it does, I’ll push out an update including this mapping as part of the config script.
It Works this is great
Ive got the steps for what i did to get education perfect working with sso incase it helps anyone trying to use the sso with other apps
here are the steps to setup ep
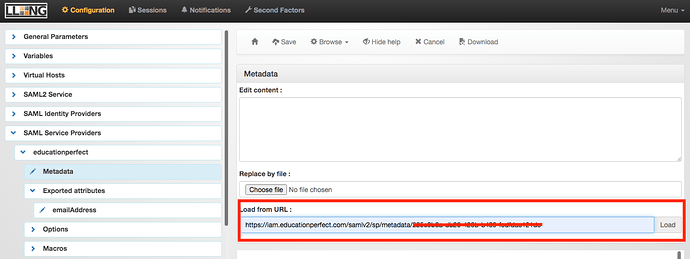
- Provide EP (support@educationperfect.com) with the url for the metadata (https://auth.yourdomain/saml/metadata)
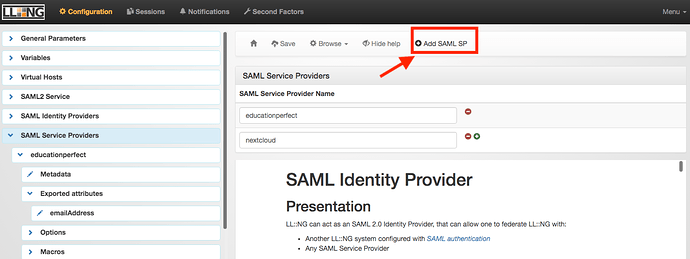
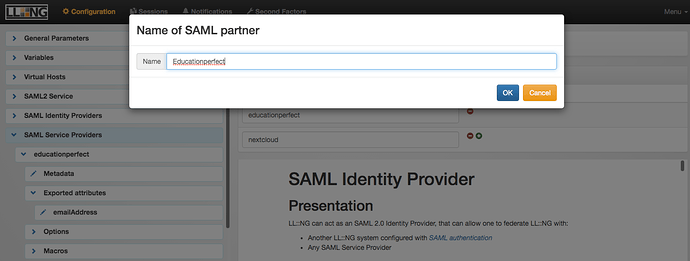
- In the LLNG Manager. In the left gutter, click on SAML Service Providers , then click Add SAML SP at the top. Give it a descriptive name (like “Educationperfect”) and click OK .
- Below SAML Service Providers , expand the new entry for Educationperfect , and click on Metadata . In the Load from URL : box enter the URL for “Issuer” that you receive from Intergrations team and click Load
-
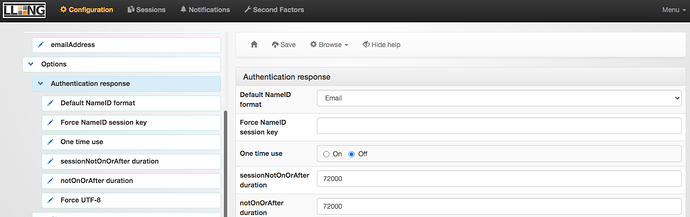
Back in the left gutter, below Options , click on Authentication Response . Select EMAIL in the dropdown box for Default NameID format
-
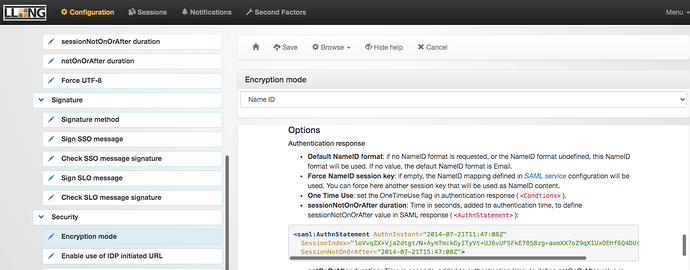
Back in the left gutter, below Options , click on Security . Under Encryption mode select Name ID from the dropdown box
-
Back in the left gutter, below Options , click on Security . Make sure Enable use of IDP initiated URL is enabled
-
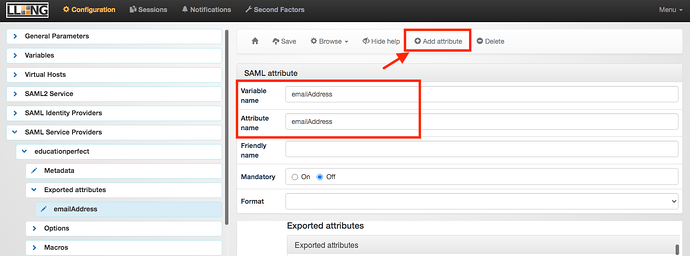
Back in the left gutter, below Metadata , click on Exported attributes . At the top, click on Add attribute , and add 1 attribute. In the attribute box both the Variable name and Attribute name should be emailAddress
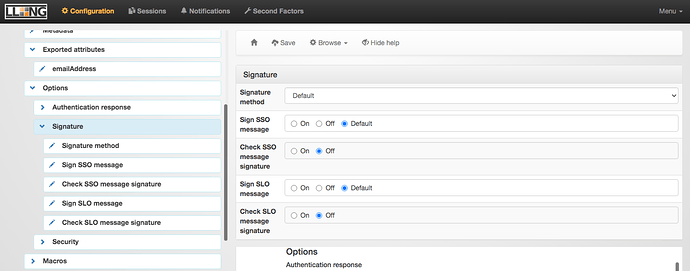
- Back in the left gutter, two lines down, expand Options , then click on Signature . Set both Check SSO message signature and Check SLO message signature to Off .
- Save your work.
also when adding web apps be sure to add the icons to /usr/share/lemonldap-ng/portal/htdocs/static/common/apps/
I’ve updated the config script templates to remove the Create an account button from the portal, but not sure that’s worth a new release on its own. Any other noted issues or desired updates to the lemon_config.sh script?
In my opinion I think it works well I can’t think of any other changes I also can confirm it works without issue if you setup with ldap then change to ad (obviously it should work but as we all know sometimes remenents of an old configuration can cause issues) I’d go as far as saying it should be made apart of the main software centre install
That’s probably a little premature at this point, but I’m glad it’s working well for you. It seems to be working well on my end too. I’d still like to see some other testing to make sure (or at least “more sure”) I’m not missing an edge case in the configuration I’m scripting.
There’s a pretty significant remaining issue with Nextcloud, and that’s that the user IDs are passed as the actual usernames, not the lengthy UUIDs that are used in a standard Nethserver installation. While I tend to favor this (it means the users’ directories are their usernames, not something like 0497e5fa-9937-103a-8784-d398046b9779), it’d be a disaster if SAML were implemented on a Nextcloud installation with existing data–a user would log in and no longer have access to their data.
I’m not quite sure the best way to deal with this. LDAP has a field for entryUUID, which I’m sure I could map to work with Nextcloud–but I don’t see any equivalent field in AD. And while it’s nice to have the directory names match the usernames, I’m not aware of any automated way to transfer existing data. I might have to leave this one at “don’t do this on a Nextcloud installation with existing user data”.
Meanwhile, I’m making significant progress on the “SSO for SSH” project, which is what got me interested in this in the first place–I hope to update the how-to with that information shortly.
I realized that in my attempt to introduce a reduced-size logo, I inadvertently built the RPM with a larger one. I’ve rebuilt it, adding the change to lemon_config.sh to remove the Register button.
I didn’t think of the issue with user id in existing system. When I get some time I’ll see if there’s a way to fix even maybe with a seperate tool or script, I’ll also try to get SSO/SLO signing working.
I’m glad you’re making progress on SSO for SSH I know how exciting it gets when things are on a roll (probably why I got a bit carried away thinking with a narrow scope of my environment rather than other scenarios).
Either way you’ve made great progress on this, my original reason for wanting SSO was not based on my needs per say but when looking at the cost of integrating systems for use with online learning platforms costs are prohibitive for small schools, community groups and group tutoring and thought this could be a solution interns of user licence costs (when they usually have a minimum of 500 users) and the eventual ability to run on raspberry pi.
Just saw these maybe helpful or at least a start https://central.owncloud.org/t/moving-ldap-accounts-from-uid-to-username/26620/3 https://social.technet.microsoft.com/Forums/en-US/fff4fe28-761d-4039-8aa4-847c449a171e/how-to-import-entryuuid-attribute-into-adlds-as-objectguid?forum=winserverDS
also just a thought would entryUUID be the equivalent of GUID or objectGUID
It would doubtless serve the same function, but it isn’t the same value. You can try this out on a test Nethserver system with AD and Nextcloud (but without SSO)–log into Nextcloud as a user, upload some files, and then find them on the hard drive. You’ll see that the user’s directory is named something like c0bda50a-924d-1038-8e72-73918c4fbff5. Now examine that user using phpLDAPAdmin. Unless I’m mistaken, you won’t find any attribute that matches that value. When I checked, I even downloaded the GUID and objectGUID and did hexdump on them–still no match. It’s obviously there somewhere, but it seems to be somewhat buried.
So there’s the conundrum. I like this behavior better. I have no idea why Nethserver is using these UUIDs as usernames rather than the actual usernames. And yes, it’s possible to move the files over for Nextcloud; I’ve done it before. It’s tedious, but possible.
That part of the suggestion in one of those links about copping the files over i didn’t agree with i mean yes it works but its not a solution especially if your talking many hundreds to thousands of gigs.
I admit im a bit rusty with my ad schema knowledge as its been a long time since i moved to linux from windows (im talking server 2003) but this has been a great refresher course for me 
I’ll do some testing and post what i find