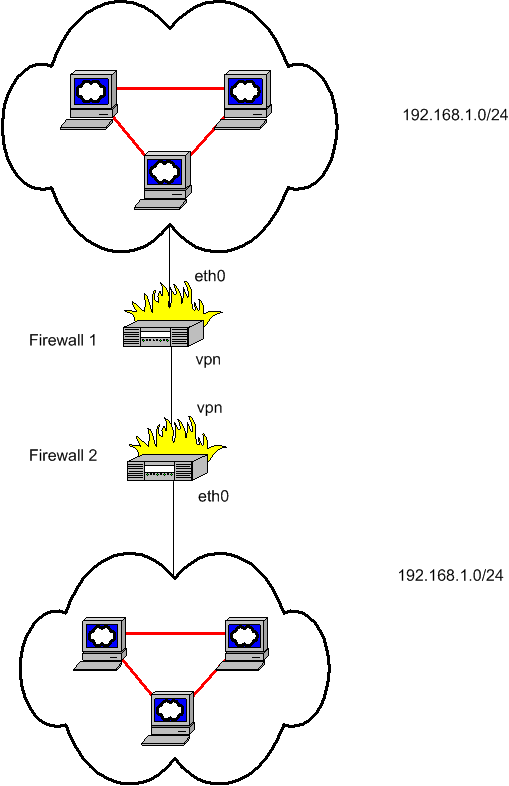
Therefore, a little “link” for people…
This is the example…
LongStoryShort solution should be SNAT+DNAT and DNAT+SNAT.
and these are the rules for ShoreWall 4.4.22 or earlier
The entries in /etc/shorewall/netmap in firewall1 would be as follows:
#TYPE NET1 INTERFACE NET2
SNAT 192.168.1.0/24 vpn 10.10.11.0/24 #RULE 1A
DNAT 10.10.11.0/24 vpn 192.168.1.0/24 #RULE 1B
The entry in /etc/shorewall/netmap in firewall2 would be:
#TYPE NET1 INTERFACE NET2
DNAT 10.10.10.0/24 vpn 192.168.1.0/24 #RULE 2A
SNAT 192.168.1.0/24 vpn 10.10.10.0/24 #RULE 2B
And these are for ShoreWall 4.4.23 or later; according to the link…
Beginning with Shorewall 4.4.23, you can bridge two duplicate networks with one router, provided that your kernel and iptables include Rawpost Table Support. That support is used to implement Stateless NAT which allows for performing DNAT in the rawpost table POSTROUTING and OUTPUT chains and for performing SNAT in the raw table PREROUTING chain. Using this support, only firewall1 requires /etc/shorewall/netmap. Two additional entries are added.
#TYPE NET1 INTERFACE NET2
SNAT 192.168.1.0/24 vpn 10.10.11.0/24
DNAT 10.10.11.0/24 vpn 192.168.1.0/24
SNAT:P 192.168.1.0/24 vpn 10.10.10.0/24
DNAT:T 10.10.10.0/24 vpn 192.168.1.0/24
I’ll try to get some fun with these settings into my enviroment. I’m quite sure that it will be really a mess during tests…