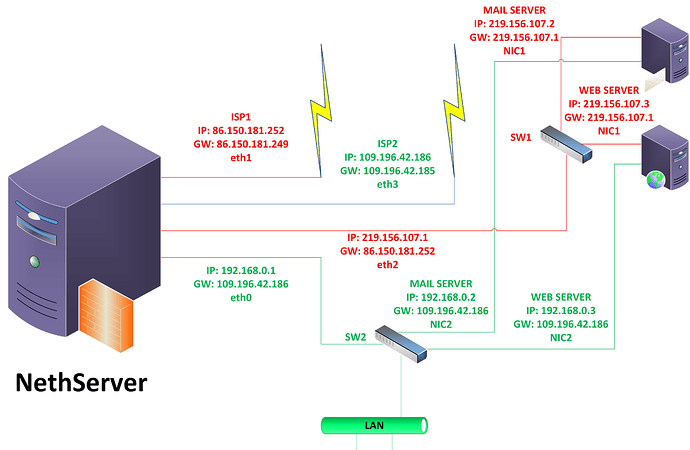
as seen from output of iptables command eth2 does not appear in the list with MASQUERADE this happens when in DMZ (ORANGE) if I put in the RED ZONE eth2 on output of iptables i have.
iptables -L -vn -t nat
Chain PREROUTING (policy ACCEPT 6 packets, 456 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 1 packets, 84 bytes)
pkts bytes target prot opt in out source destination
8 555 eth1_masq all – * eth1 0.0.0.0/0 0.0.0.0/0
0 0 eth2_masq all – * eth2 0.0.0.0/0 0.0.0.0/0
2 160 eth3_masq all – * eth3 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 6 packets, 508 bytes)
pkts bytes target prot opt in out source destination
Chain eth1_masq (1 references)
pkts bytes target prot opt in out source destination
8 555 MASQUERADE all – * * 0.0.0.0/0 0.0.0.0/0 policy match dir out pol none
Chain eth2_masq (1 references)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all – * * 0.0.0.0/0 0.0.0.0/0 policy match dir out pol none
Chain eth3_masq (1 references)
pkts bytes target prot opt in out source destination
2 160 MASQUERADE all – * * 0.0.0.0/0 0.0.0.0/0 policy match dir out pol non
GREEN MORE
45 3289 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
75 20657 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
114 23690 r1_frwd all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
29 4203 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
0 0 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
29 4203 r12fw all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
16 2575 fw2r1 all – * * 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ivpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 loc2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 lvpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
78 33377 net2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ovpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
ORANGE MODE
24 1550 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
86 26729 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
101 27823 r1_frwd all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
6 695 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
0 0 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
6 695 r12fw all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
0 0 fw2r1 all – * * 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ivpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 loc2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 lvpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
74 42411 net2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 orang2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ovpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
RED MODE
20 1336 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
51 18995 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
65 20019 r1_frwd all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
2 232 smurfs all – * * 219.156.107.0/25 0.0.0.0/0 ctstate INVALID,NEW,UNTRACKED policy match dir in pol none
0 0 tcpflags tcp – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
2 232 r12fw all – * * 219.156.107.0/25 0.0.0.0/0 policy match dir in pol none
0 0 fw2r1 all – * * 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ivpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 loc2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 lvpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
42 29457 net2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none
0 0 ovpn2r1 all – * eth2 0.0.0.0/0 219.156.107.0/25 policy match dir out pol none