@fausp I am with you 100% on having problems with some other items needing a valid cert for authentication and honestly it is very easy & arbitrary to do. So much so I made a feature request here you should bump up to let them know you have an active interest in a 1 click cert import for AD.
@mrmarkuz helped me understand the logic of some of the scripts posted around the forum and it comes down to four basic steps:
-
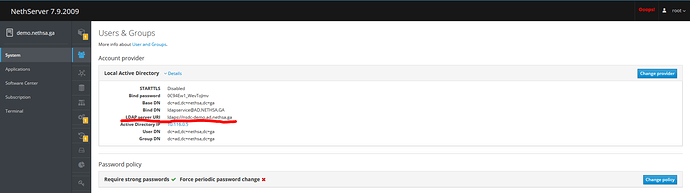
- Request & obtain a valid LE cert for your AD container on NS.
Done via the GUI and can be found under System → User & Groups → Account Provider → Details
- Request & obtain a valid LE cert for your AD container on NS.
-
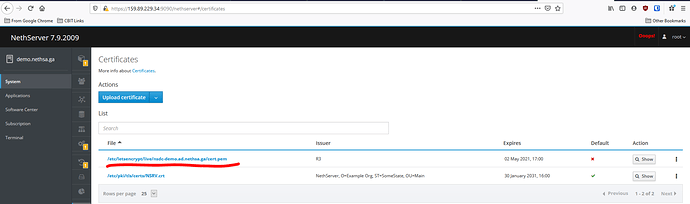
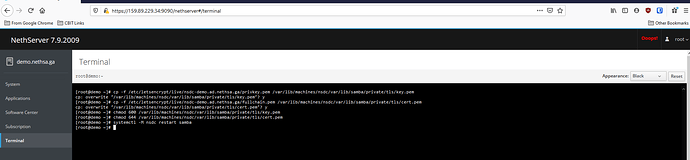
Copy the valid LE cert to the NS AD container
cp -f /etc/letsencrypt/live/nsdc-demo.ad.example.com/privkey.pem /var/lib/machines/nsdc/var/lib/samba/private/tls/key.pem
cp -f /etc/letsencrypt/live/nsdc-demo.ad.example.com/fullchain.pem /var/lib/machines/nsdc/var/lib/samba/private/tls/cert.pem
-
Change permissions of newly copied LE cert
chmod 600 /var/lib/machines/nsdc/var/lib/samba/private/tls/key.pem
chmod 644 /var/lib/machines/nsdc/var/lib/samba/private/tls/cert.pem -
Restart NS AD container
systemctl -M nsdc restart samba
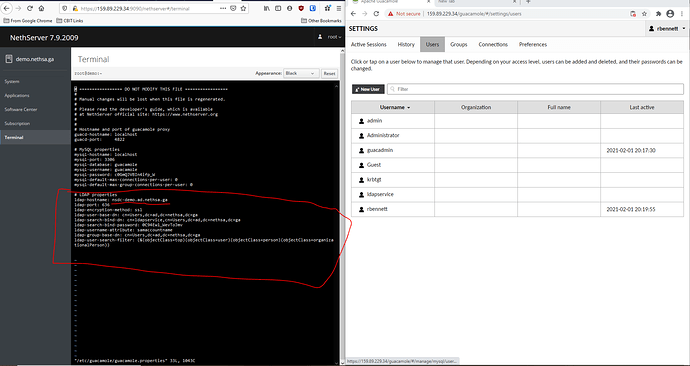
Now you can automate all of this to your hearts delight like @Andy_Wismer suggested but it is dependent on how you want to renew & hook in your LE cert. I verified that this above solution worked for my Guacamole AD users because I just can’t think disabling strong authentication in 2021 is gonna be a sustainable thing. This took me literally 10 minutes to do manually but would be horrible to keep track of for 3 month renewals or scale out.