Hi syntaxerrormmm,
Thank you very much for your reply.
No problem for admin to login to Server Manager.
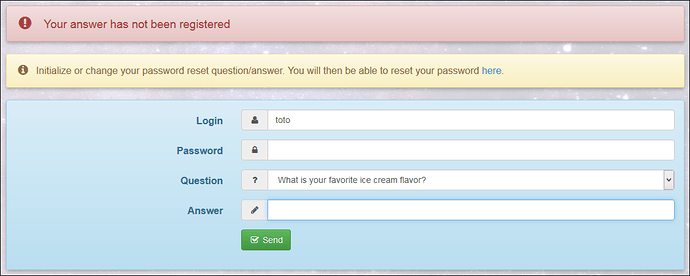
Standard users cannot login to Server Manager as they don’t know their new AD passwords.
If they use their old password, they get: “Invalid credentials”
The AD installation have changed: uid, gid, password, shell and I don’t know what else.
Before AD installation:
# cd /var/lib/nethserver/home/
# getent passwd *
michelandre@micronator-dev.org:*:1001:1000:Michel-Andre:/var/lib/nethserver/home/michelandre:/bin/bash
titi@micronator-dev.org:*:1003:1000:Titi Deuxime:/var/lib/nethserver/home/titi:/bin/bash
toto@micronator-dev.org:*:1002:1000:Toto Premier:/var/lib/nethserver/home/toto:/bin/bash
#
After AD installation:
I enabled “Remote shell” and gave password to user admin and only to the standard user toto.
# cd /var/lib/nethserver/home/
# getent passwd *
admin@micronator-dev.org:*:1268801105:1268800513:admin:/var/lib/nethserver/home/admin:/bin/bash
michelandre@micronator-dev.org:*:1268801107:1268800513:michelandre:/var/lib/nethserver/home/michelandre:/usr/libexec/openssh/sftp-server
titi@micronator-dev.org:*:1268801106:1268800513:titi:/var/lib/nethserver/home/titi:/usr/libexec/openssh/sftp-server
toto@micronator-dev.org:*:1268801108:1268800513:toto:/var/lib/nethserver/home/toto:/bin/bash
#
Only user toto can login to Server Manager and change his password because I gave him a new one. michelandre and titi can not do that.
Michel-André