Beyond my understanding, but could this 2FA become a module that ties in with other parts of Nethserver authentication such as SoGo, Nextcloud, OpenVPN, Cockpit much like how Fail2ban interfaces with them?
2fa with SOGo is unavailable, not implemented
Webtop has implemented it
Roundcubemail also
In fact it must be implemented application per application , probably with different keys, if one is compromissed, others applications are safe.
For now I am studying to protect ssh and cockpit
…which is the real advantage of the LDAP proxy method cited above, no client application support is needed. If there’s a F/OSS way to do that, it would be worth investigating.
There is https://www.privacyidea.org (ldap-proxy). Here are some #2fa related discussions mentioning other options (http://dynalogin.org/, https://www.linotp.org/…)
Although deviating from the OT but somehow related, #sso and IAM solutions:
- Comparison of open-source SSO implementations (Keycloak, WSO2, Gluu, CAS…)
- List of single sign-on implementations
- https://lemonldap-ng.org
- https://www.pomerium.io/ (no AD support at the moment)
- https://aerobase.io/
- https://github.com/clems4ever/authelia
- https://github.com/buzzfeed/sso
- https://forgerock.org/
- https://www.wikidsystems.com/community-edition/
I made it at hands:
yum install google-authenticator.x86_64
/etc/pam.d/sshd
auth required pam_google_authenticator.so
/etc/ssh/sshd_config
ChallengeResponseAuthentication yes
sudo service sshd restart
google-authenticator
But will be great make this via cockpit
Thanks!
It is possible no?
-> https://fedoramagazine.org/two-factor-authentication-ssh-fedora/
A ticket on SOGo BT: https://sogo.nu/bugs/view.php?id=2722
Yes, It is still in development, I need to release a previous related work, then we could think on it
It is under development now, there’s a wiki page too!
https://github.com/NethServer/dev/wiki/One-Time-Password-(OTP)-authentication
Steph has also drafted a prototype
@stephdl are you teasing us?

Anyway, maybe this has been asked elsewhere… OTP works ONLY for WebTop via HTTPS.
No “application specific” password are currently on roadmap.
got something workable for testing purpose
- Install freeOTP on your mobile
- install nethserver-cockpit
yum install http://packages.nethserver.org/nethserver/7.7.1908/autobuild/x86_64/Packages/nethserver-cockpit-1.4.6-1.20.pr191.g436be27.ns7.noarch.rpm http://packages.nethserver.org/nethserver/7.7.1908/autobuild/x86_64/Packages/nethserver-cockpit-lib-1.4.6-1.20.pr191.g436be27.ns7.noarch.rpm
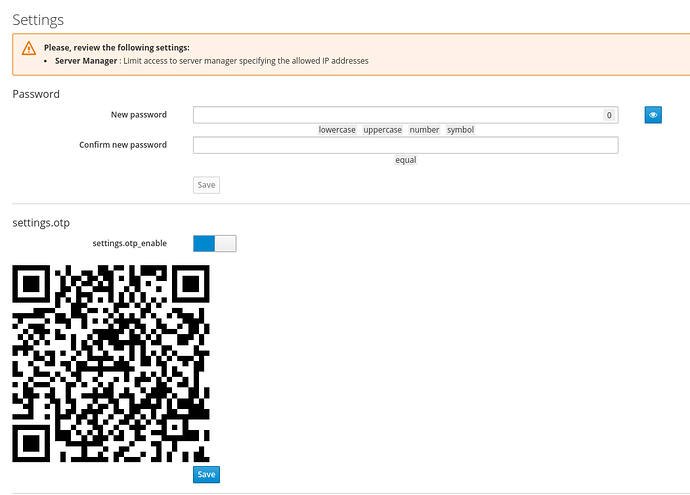
then go to settings pages
- enable OTP, flash the QR code with freeOTP, logout, and login again, use login+password+OTP pin (on your mobile)
Works perfectly! Thanks for this very welcome extra layer of security.
The improvement that maybe can be made is, that after logging in with the username and the password, the browser loses the focus on the OTP input box. It would be nice that after entering the username/password the browser would get the focus on the OTP input box (flashing cursor, as it does with the username/password)
The otp input form is out of the scope of our new feature, indeed it is provided by the cockpit project.
However we want to provide other features
Recovery password if you have lost your mobile
A test to validate your token before to use it in real
Provide otp for sshd also with the same token
Is there a “remember this device” feature so you don’t have to enter the OTP credential between logins?
no the goal is to be sure you are the good guy who wants to authenticate, so you need your mobile or one of the 5 recovery code
Dang, maybe at another time. I’m thinking of scale (for instance I jump between small businesses all the time) & pulling up a 2fa every single login would probably make that a non starter for me except for those VM’s that require that extra step.
security is sometime not negotiable, security is often a loss of time, security will save your time to avoid a recovery after a hack
Just for understanding: what happens if you losse your phone or it gets stolen? Is there any way to revoke the OTP QR code without getting locked out?
if you lose your phone you have to use the recovery code, but it is a double authentication, you still need your login+password