I used NethServer as a firewall/UTM/VPN appliance to setup a multi-site network today. The documentation seemed to be lacking a bit, so I thought I’d fill in the gaps with a howto. It’s more of a list of screenshots per site rather than a step-by-step how to.
In this test setup, I used the 192.168.99.0 subnet as the WAN. I have about 150 available public IPs left on my fiber connection, but they’re all on the same subnet too, so there’s really no difference in using the 99.0 subnet and actual public IPs… plus I don’t have the blur things out this way. 
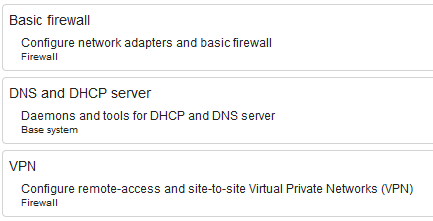
I had these packages installed on all three NethServer instances to accomplish this setup:
Test network/site #1:
This is the “main site” aka corporate headquarters.
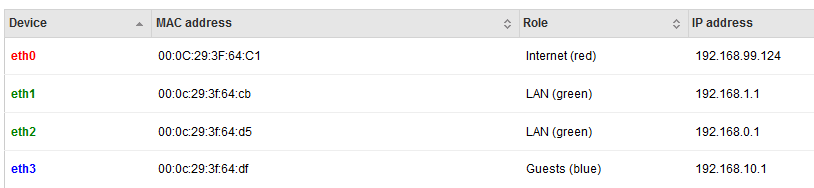
eth0: WAN
eth1: LAN for AD DC, desktops, etc
eth2: LAN for PBX and phones
eth3: public wifi
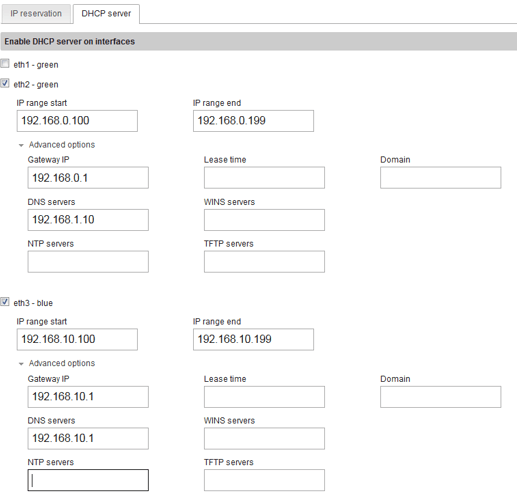
DHCP setup for network/site #1:
The AD DC is handling DHCP and DNS for eth1, which is why it’s disabled for that adapter. You can see its IP listed as the DNS server for eth2.
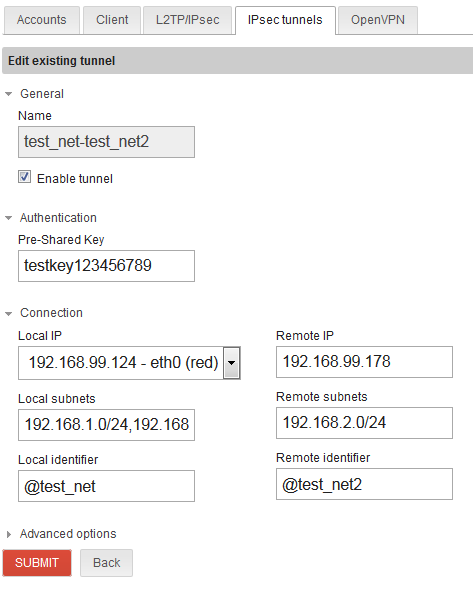
IPsec setup for network/site #1 to network/site #2:
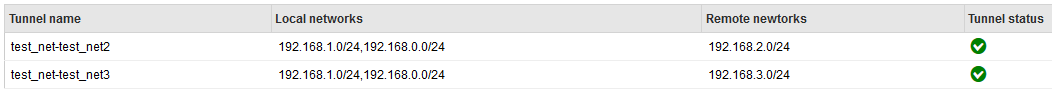
Local subnets field is cut off, but says 192.168.1.0/24,192.168.0.0/24
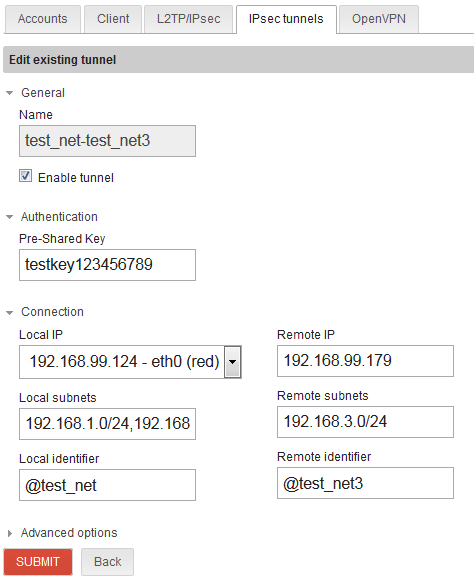
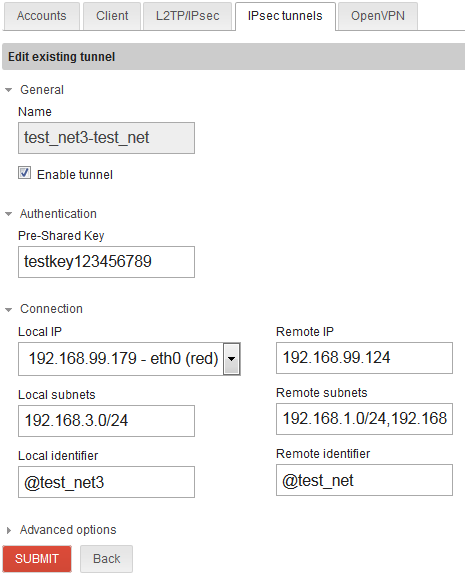
IPsec setup for network/site #1 to network/site #3:
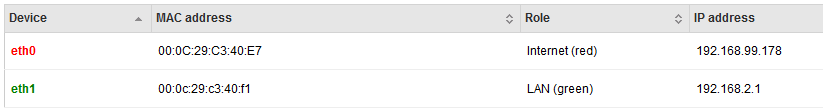
Test network/site #2:
Remote site #1 is a small office with only 1 green zone and 2 red zone
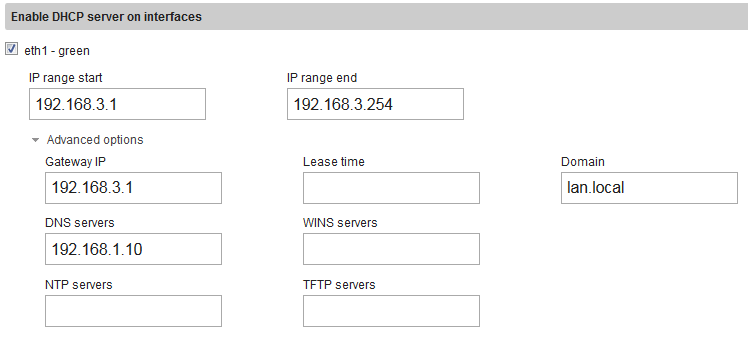
DHCP for network/site #2:
My test domain at the corporate headquarters is “lan.local” I had to fill that in for DNS to resolve properly.
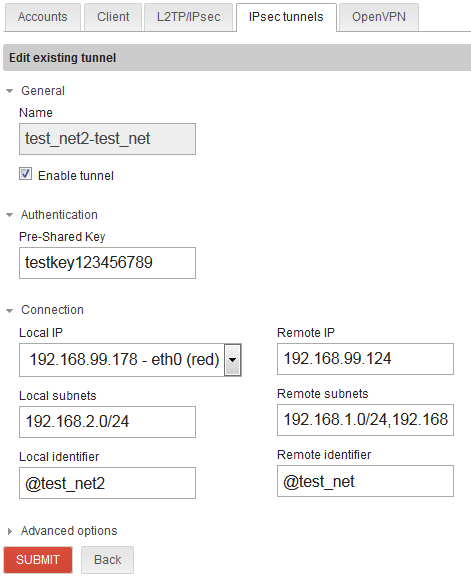
IPsec for network/site #2 to network/site #1:
I noticed the VPN would not establish connection until after rebooting this NethServer instance. The log was producing an error that it could not authenticate.
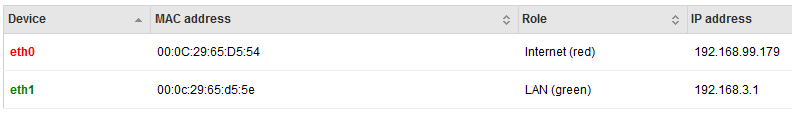
Test network/site #3 is another small remote office:
DHCP for network/site #3:
IPsec for network/site #3 to network/site #1:
Had to reboot this instance too before the vpn would connect. Then everything worked great!
PCs in remote locations can join the domain, map drives, place phone calls, etc… all using the server and PBX in the main location.