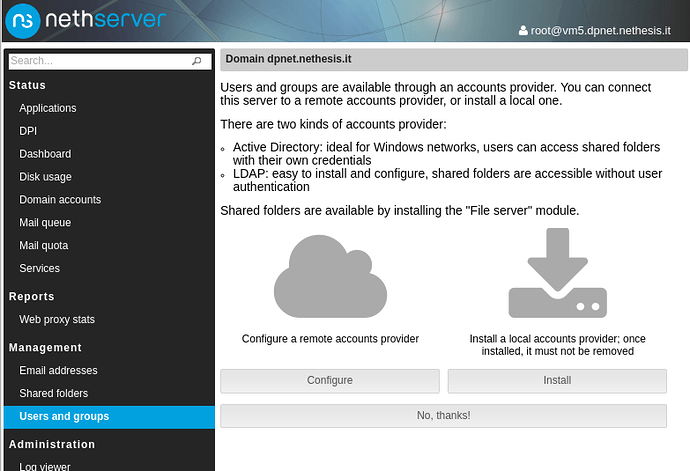
@robb and others, I’d like to resume this discussion with a small enhancement proposal. We could easily add more information about the accounts provider concept to the Users&Groups page.
If an account provider has not been configured this could be the new layout (instead of the current standalone “Configure” button):
What happens when the buttons are clicked?
- “Configure” points to “Configuration > Accounts provider”
- “Install” points to “Software center”
- “No, thanks!” point to “Dashboard”
What do you think? Is it a good idea? Is the text clear enough?
/edit: added shared folder explanation
//edit: if you find some English mistakes, please comment directly on my PR here: https://github.com/NethServer/nethserver-sssd/pull/48/files
///edit: @flatspin’s clarification