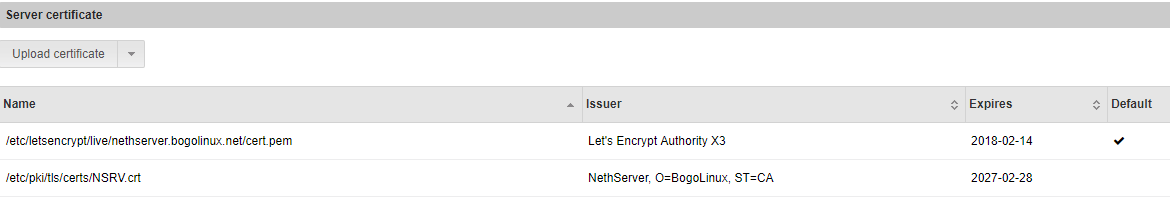
Tried to log on to my local Admin UI today and Chrome threw a certificate error. Hmmmm.
Looking into it, it looks like after the automatic renew of the certificates on July 19th the new certificates weren’t propagated though to the files in the /etc/pki tree, which is where the https and Admin UI servers grab the certs from:
[root@Nethserver ~]# ls -lrt /etc/letsencrypt/live/nethserver.bogolinux.net/
total 4
-rw-r--r-- 1 root root 543 Mar 19 18:26 README
lrwxrwxrwx 1 root root 51 Jul 19 03:33 privkey.pem -> ../../archive/nethserver.bogolinux.net/privkey5.pem
lrwxrwxrwx 1 root root 53 Jul 19 03:33 fullchain.pem -> ../../archive/nethserver.bogolinux.net/fullchain5.pem
lrwxrwxrwx 1 root root 49 Jul 19 03:33 chain.pem -> ../../archive/nethserver.bogolinux.net/chain5.pem
lrwxrwxrwx 1 root root 48 Jul 19 03:33 cert.pem -> ../../archive/nethserver.bogolinux.net/cert5.pem
[root@Nethserver ~]#
[root@Nethserver ~]# ls -lrt /etc/letsencrypt/archive/nethserver.bogolinux.net/
total 80
-rw-r--r-- 1 root root 1708 Mar 19 18:26 privkey1.pem
-rw-r--r-- 1 root root 3469 Mar 19 18:26 fullchain1.pem
-rw-r--r-- 1 root root 1647 Mar 19 18:26 chain1.pem
-rw-r--r-- 1 root root 1822 Mar 19 18:26 cert1.pem
-rw-r--r-- 1 root root 1704 Mar 20 10:21 privkey2.pem
-rw-r--r-- 1 root root 3489 Mar 20 10:21 fullchain2.pem
-rw-r--r-- 1 root root 1647 Mar 20 10:21 chain2.pem
-rw-r--r-- 1 root root 1842 Mar 20 10:21 cert2.pem
-rw-r--r-- 1 root root 1708 Mar 20 12:00 privkey3.pem
-rw-r--r-- 1 root root 3526 Mar 20 12:00 fullchain3.pem
-rw-r--r-- 1 root root 1647 Mar 20 12:00 chain3.pem
-rw-r--r-- 1 root root 1879 Mar 20 12:00 cert3.pem
-rw-r--r-- 1 root root 1708 May 20 03:38 privkey4.pem
-rw-r--r-- 1 root root 1879 May 20 03:38 cert4.pem
-rw-r--r-- 1 root root 3526 May 20 03:38 fullchain4.pem
-rw-r--r-- 1 root root 1647 May 20 03:38 chain4.pem
-rw-r--r-- 1 root root 1704 Jul 19 03:33 privkey5.pem
-rw-r--r-- 1 root root 3526 Jul 19 03:33 fullchain5.pem
-rw-r--r-- 1 root root 1647 Jul 19 03:33 chain5.pem
-rw-r--r-- 1 root root 1879 Jul 19 03:33 cert5.pem
[root@Nethserver ~]#
[root@Nethserver ~]# ls -l /etc/pki/tls/certs/
total 24
lrwxrwxrwx 1 root root 49 Jun 13 18:22 ca-bundle.crt -> /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
lrwxrwxrwx 1 root root 55 Jun 13 18:22 ca-bundle.trust.crt -> /etc/pki/ca-trust/extracted/openssl/ca-bundle.trust.crt
-rw------- 1 root root 3527 May 22 12:05 httpd-admin.crt
-rw------- 1 root root 3527 May 22 12:05 localhost.crt
-rwxr-xr-x 1 root root 610 Feb 20 06:41 make-dummy-cert
-rw-r--r-- 1 root root 2388 Feb 20 06:41 Makefile
-rw-r--r--. 1 root root 1484 Mar 1 19:17 NSRV.crt
-rwxr-xr-x 1 root root 829 Feb 20 06:41 renew-dummy-cert
[root@Nethserver ~]#
[root@Nethserver ~]# grep SSLCertificate /etc/httpd/conf.d/ssl.conf
# Point SSLCertificateFile at a PEM encoded certificate. If
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
# Point SSLCertificateChainFile at a file containing the
# the referenced file can be the same as SSLCertificateFile
#SSLCertificateChainFile /etc/pki/tls/certs/server-chain.crt
[root@Nethserver ~]#
[root@Nethserver ~]# grep SSLCertificate /etc/httpd/admin-conf/httpd.conf
SSLCertificateChainFile /etc/letsencrypt/live/nethserver.bogolinux.net/chain.pem
SSLCertificateFile /etc/pki/tls/certs/httpd-admin.crt
SSLCertificateKeyFile /etc/pki/tls/private/httpd-admin.key
[root@Nethserver ~]#
httpd-admin.crt and localhost.crt are taken from the xxx4 set of certificates which expired today.
Cheers.